In today's digital landscape, safeguarding online privacy has become more important than ever. With the proliferation of tracking tools, users must be aware of how their data is being collected and used. One tool that often raises eyebrows is Grabify, an IP logger. While Grabify has legitimate applications, it also sparks concerns around ethics and privacy. This article explores what Grabify is, how it functions, the ethical questions it raises, and how to protect your privacy online.
What is Grabify?

Grabify is an online tool that enables users to generate links that track the IP addresses of those who click on them. When someone interacts with a Grabify link, their IP address is logged, revealing details such as their general location, device, and sometimes even their internet service provider (ISP).
Grabify is often used to track website visitors, similar to analytics tools but with a narrower focus — IP logging.
How Does Grabify Work?
The process of using Grabify is straightforward:
A user visits the Grabify website and inputs a URL (such as a website or image link).

Grabify generates a shortened version of the URL.
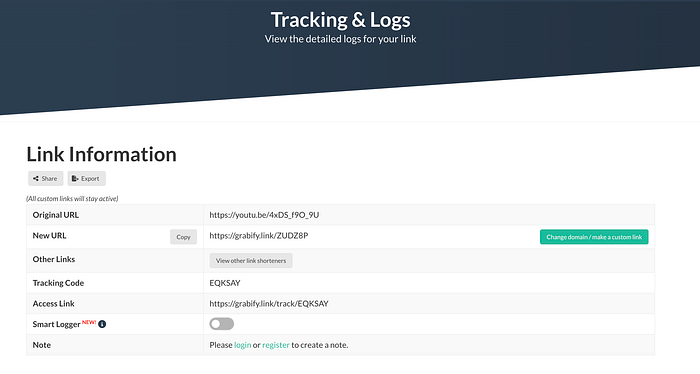
The user shares the shortened link. When someone clicks it, Grabify logs details such as the visitor's IP address, browser type, device, and more
The original content is displayed to the person who clicked the link, making the tracking virtually invisible.
What Information Does Grabify Collect?
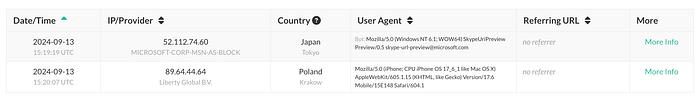
When a user clicks on a Grabify link, the following data may be collected:
- IP Address: Reveals the user's general location.
- Device and Browser Information: Specifies whether the visitor is using a mobile device, desktop, or other, and identifies the browser type.
- Operating System: Details the visitor's operating system (e.g., Windows, macOS, or Linux).
- User-Agent String: A technical identifier that includes information about the visitor's browser and operating system.
- Timestamp: Records the precise time of the click.
Ethical Considerations
Though Grabify can be used for legitimate purposes — like monitoring web traffic or identifying suspicious activity — it also poses ethical challenges. The ease with which IP logging can invade privacy raises serious concerns. Below, we explore both legitimate and illegitimate uses of Grabify.
Legitimate Uses
- Security: Website administrators or content creators can use Grabify to track suspicious IP addresses and identify potential threats.
- Audience Monitoring: Businesses or influencers may use Grabify links to analyze where their audience is coming from and optimize their content strategy.
- Digital Forensics: Law enforcement and security professionals may use IP logging to track cybercriminals or investigate online threats.
Illegitimate Uses
However, Grabify can easily be misused, including for:
- Doxxing: Malicious users may attempt to uncover personal information by tracking an individual's IP address to determine their location or ISP.
- Stalking: Grabify links can be exploited to track and invade someone's privacy without their consent.
- Social Engineering: Hackers may use IP logging to identify potential victims and launch targeted phishing or other cyberattacks.
Legal and Privacy Concerns
The use of tools like Grabify brings significant legal and privacy considerations. In many regions, using IP loggers for malicious activities — such as stalking, harassment, or fraud — can lead to legal action. Collecting user data without consent may also violate privacy laws like the General Data Protection Regulation (GDPR) in Europe and the California Consumer Privacy Act (CCPA) in the U.S.
While IP addresses may not always be considered "personal data," they can still be used to approximate a user's location. Thus, logging IP addresses without explicit permission, particularly for harmful purposes, can infringe on privacy rights.
How to Protect Yourself from IP Loggers
If you're concerned about tools like Grabify tracking your online activity, there are several ways to shield yourself:
- Use a VPN: A Virtual Private Network (VPN) masks your real IP address by routing your connection through another server, making it difficult to log your actual location.
- Be Cautious with Links: Avoid clicking on links from unknown or suspicious sources. If a link looks unfamiliar, it's better to err on the side of caution and avoid it.
- Use Browser Extensions: Various browser extensions and security tools can help block tracking attempts and prevent IP loggers from collecting data.
- Proxy Servers: Like VPNs, proxies serve as intermediaries between your device and the internet, hiding your real IP address.
Conclusion
Grabify is a versatile tool that can be used for both constructive and harmful purposes. While IP tracking has legitimate applications, such as bolstering security and monitoring web traffic, it's crucial to recognize the ethical and privacy concerns that arise when such tools are used irresponsibly. Users should be mindful of these issues and take proactive measures to protect their online privacy.
For those using Grabify or similar tools, respecting privacy laws and ethical standards is essential. Data collection should always be transparent and consensual. For everyone else, using tools like VPNs and practicing caution with unfamiliar links can significantly enhance your online security.
Remember: Your online privacy is valuable — stay informed and protect it.
