Fredrick Brennan, the original creator of 8Chan, the message board that Q uses to write postings, discussed today mathematical proof that Q's new postings are fake. Q is the person (or persons) whose postings since 2017 inspired the QAnon movement. One result of the QAnon movement was the near overthrow of the USA government on January 6, 2021. Hence, it is important to know whether Q has restarted posting and will restart the QAnon movement, or whether Q's new postings are fraudulent.
Hash Codes and User Anonymity on 8Chan/8Kun
The key is that on 8Chan/8Kun, every post is marked with a "tripcode". Users on this board are guaranteed anonymity, and the tripcode is an encrypted string that proves authenticity. Let's look at an example:
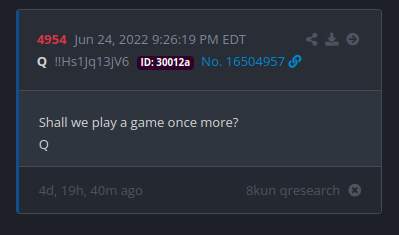
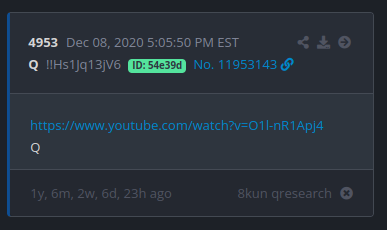
Up to December 2020, Q had regularly made postings on 8Kun (the successor site to 8Chan). Each posting was marked with the name, Q, followed by the tripcode, !!Hs1Jq13jV6, followed by an ID, which is apparently derived from the IP address, followed by a post number.
Notice that the tripcode in December 2020 is the same as the tripcode in June 2022. That may look like an incredibly tiny detail, but it is key to the claim that the new Q posts are fraudulent.
The tripcode is derived by encrypting the password, along with a secret salt, then generating a SHA1 hash. In a video live stream today, Fredrick Brennan explained what that means as follows:
$ salt=SALTYKERNEL
$ echo "mysecretpassword${salt}" | sha1sum
a830df5fede64b62bcaf62b1cca8067d0bda3cad -
$ salt=SALTYKERNELICIOUS
$ echo "mysecretpassword${salt}" | sha1sum
581c55e9cdc1f815a577abf0c4322753049b7746 -On the login form of the 8Kun website, a user enters a password. Here we're using the string mysecretpassword as the password. To make it extra difficult to crack the password, the website appends another phrase to the password, and that phrase is the "secret salt" mentioned earlier. In this case, I've put the salt in a variable named salt. Inside the website, the password and the salt are concatenated together, then encrypted. A hash of the encrypted string is generated using SHA1. What's shown here is simply generating the SHA1 hash using the sha1sum program, and no actual encryption is performed.
The output of this is the tripcode (more or less).
The word hash here refers to a mathematical operation. It takes a long block of data, using the data to compute a number that can be used to identify that data. A good hash function has a very low collision rate, meaning a very low probablity that the same hash value will be generated for two different pieces of data. The SHA1 hash algorithm is an industry standard, and has an extremely low collision rate. The result is it is extremely hard for someone to find another string that will generate the same tripcode.
Notice that if thesalt value is changed, the tripcode changes. It is known that 8Kun's administration changes the salt every so often. As we see above, if the salt is changed the tripcode changes. Hence, every time 8Kun goes through a "salt rotation", changing the salt used in computing the tripcodes, every tripcode on the site changed.
It is known that between December 2020 and June 2022, 8Kun had at least one salt rotation. This means every tripcode on 8Kun will have changed at least once. Therefore, how is Q able to post using the same tripcode?
One possibility is this piece of code that Fredrik Brennan posted on GitHub:
Remember that he is the original author of the code which runs the 8Kun website. This function is written in PHP and is an event handler executed while handling an incoming post on 8Kun. It is written so that if an 8Kun administrator has made a posting using a specific password, like#postAsQ, then the hardcoded tripcode will be used.
An Administrator of 8Kun is Apparently Fraudulently Posting as Q?
What Fredrick Brennan demonstrates is a proof that Q's newest postings must be created by an 8Kun administrator, or someone working closely with the 8Kun administration. His demonstration was compelling due to the mathematics behind the SHA1 hash function.
To generate the tripcode that previously identified Q requires some kind of trickery on the 8Kun website, according to Fredrick Brennan. Trickery that only the administrators can pull off.
