I know we've heard it a thousand times over, that security in the cloud is a shared responsibility, but many times it's hard to put that responsibility into actionable items. Thankfully, Toni de la Fuente (@tonyblyx) took the time to write a tool to do just that. With Prowler (named after the 1980 song on Iron Maiden's debut album \m/) you can assess your AWS environments in accordance to the CIS Benchmark standards. I'm going to walk you through usage of the tool.
Setup
AWS IAM Setup
As with anything, proper planning is important. The first step is to create an Audit Group and an Audit User within that group. Log into the AWS console, and go to IAM > Groups > Create New Group. Give it a good name, such as SecurityAuditors. Attach the "SecurityAudit" policy to it, and review. It should look something like this:

Once you've got your group created, you need to create the user that Prowler will utilize to audit your environment. Again, in IAM, go to Users > Add User. Give them a good name, and select Programmatic Access for the AWS access type. On the permissions page, add the new user to the SecurityAuditors group that we just created. Review it to make sure it's good to go:

IMPORTANT: On the next screen is the only time you'll have these credentials available to you. I recommend downloading the CSV and putting it in a safe place and putting the user/creds in your favorite password safe.

That's it on the AWS IAM side, the rest is all CLI, so fire up your favorite shell and lets go!
AWS CLI & Prowler Setup
The first step in this equation is to download and install the awscli tool. This is accomplished by three commands:
$ curl -o awscli.zip https://s3.amazonaws.com/aws-cli/awscli-bundle.zip
$ unzip awscli.zip
$ sudo ./awscli-bundle/install -i /usr/local/aws -b /usr/local/bin/awsNext, let's clone the Prowler repo using git.
git clone https://github.com/Alfresco/aws-cis-security-benchmark.git
Finally, we need to configure the awscli tool with the credentials of the SavageAudit user I created earlier. This is where you'll utilize the information in that .csv you downloaded earlier (and put into your password safe, right?)
aws configureI already had a previous access key ID and secret access key set up, so yours will look slightly different. You can leave the region name and output format as none (just press Enter).

With that, you're ready to run Prowler.
Working with Prowler
Running Prowler is pretty straightforward, now that you have your AWS access configured, simply execute the script:
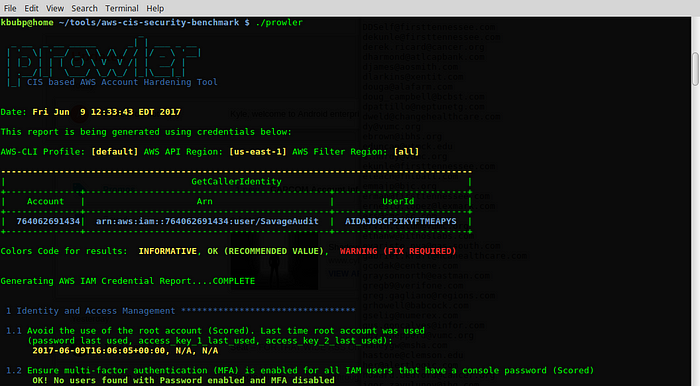
It will run through every CIS Benchmark check and give you the results. You can then use these results to harden your AWS environment.
Additional command line options, such as running one test at a time instead of the full gamut, can be found with the -h switch.

And if you want to export the results to a "report," simply do the following:
$ ./prowler > report.txtProwler is an awesome tool, but there are some things it won't do, such as tell you why a setting is a finding, or tell you how to fix it (I'm working on a pull request for that). If you want to know why your settings are a security risk and instructions on how to fix each finding, simply refer to the CIS Benchmark for AWS.
Wrap Up
At the end of the day, whether we want to admit it or not, there is no perimeter. We have users with access to a plethora of cloud services and we need to take sensible steps to secure those services. It's important to research, audit, and harden to the best of our ability (without impeding user workflow) all of the tools in our environments, both on-premises and in the cloud. This is just another tool to assist you with that. And, as always, if you need help, Savage Security has your back. We're just a phone call away (or email, you know, if you prefer not to hear the sound of another human's voice.)


