There are many ways to find parameters where the user input is getting reflected, this is just one such example using Nuclei (DAST). Other methods I discussed are included in the below collection of XSS writeups
Beginners want the tools to do everything for them, but I use nuclei to find parameters where the input is getting reflected without sanitization, and from there I try to proceed manually most of the time which also helps to get rid of false positives of fully automated tools. (Semi-automated initial recon to run in the background)
⚠️Before using this make sure to read the guidelines of the program, sometimes it is strictly mentioned that using automated tools is prohibited due to which you might be violating rules even if you are testing for good reasons. Use nuclei with rate-limit for better performance and get rid of overwhelming the server.
📒Template Link location in Kali
/home/kali/.local/nuclei-templates/dast/vulnerabilities/xss
/home/kali/.local/nuclei-templates/dast/vulnerabilities/xss/reflected-xss.yaml
/home/kali/.local/nuclei-templates/dast/vulnerabilities/xss/dom-xss.yaml🔗 Github Link (ProjectDiscovery — Nuclei)
🔍Nuclei (DAST — XSS)
- Only 2 templates we are interested in here.
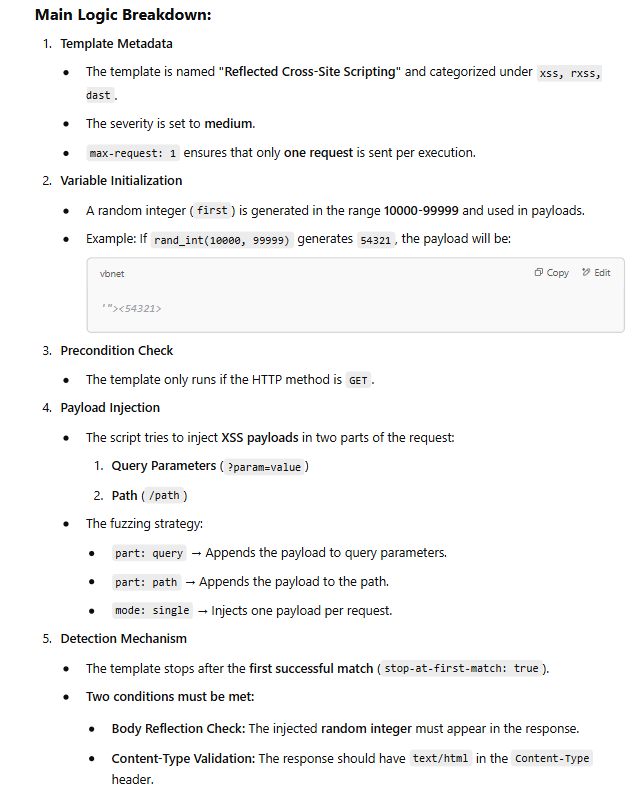
If you don't understand the template, just use ChatGPT. In the beginning days, you might not understand thoroughly, but with experience and time, new ideas will automatically click in your mind!
Prompt: Explain the main logic of the below nuclei template
- Save your URLs with parameters in any file urls.txt and run the below command, and the output we will get are the parameters where the input is not sanitized and getting reflected.
⚓This is the command that I use for XSS (DAST)
nuclei -l urls.txt -t /home/kali/.local/nuclei-templates/dast/vulnerabilities/xss/ -dast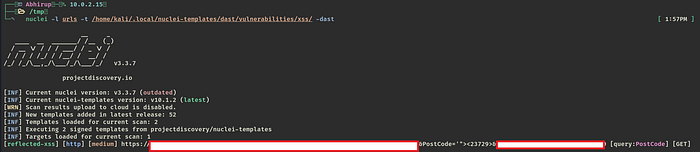
From above we can observe parameter PostCode is a potential area to test for XSS as the HTML tags and quotes are not getting sanitized and converted.
Now perform manual testing🙂
⛏️Labs with solutions
🔗Other Articles you might like:
📱Follow me on X and LinkedIn for daily bug-hunting updated tips.
🌐 Subscribe to YT Channel LegionHunter for intermediate to advanced content.
Hunter1: Blind automation without the core understanding.
Hunter2: Automation with a basic fundamental understanding.
Elite Hunter: They develop the automation!
