Introduction:
Email verification is a crucial security measure to confirm user identity and prevent unauthorized access. However, a vulnerability discovered in the email verification process of app.target.com exposes a serious flaw that allows attackers to bypass this security measure. This article details the vulnerability, its impact, and the necessary remediation steps.
Vulnerability Overview:
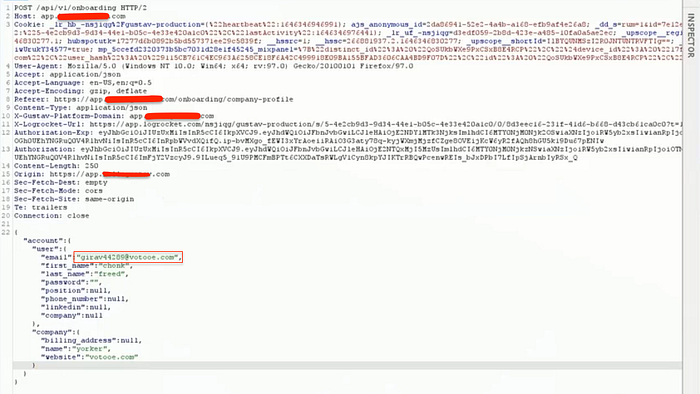
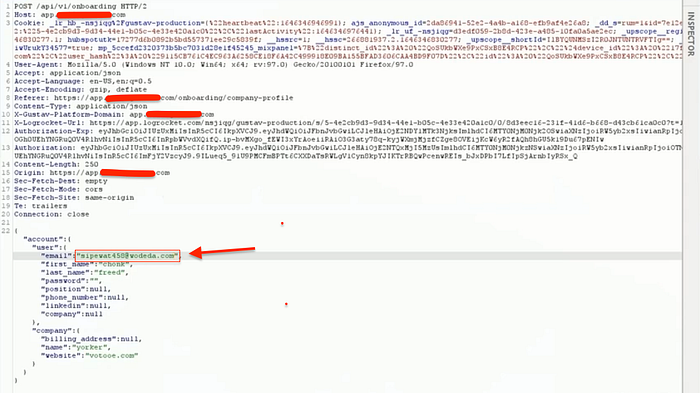
The flaw allows an attacker to register an account with their email, receive a verification link, intercept the request, and modify the email parameter to a victim's email address. This enables unauthorized use of the victim's email without proper verification.
Technical Analysis: The vulnerable API endpoint:
POST /api/v1/onboarding HTTP/2
Host: app.target.com
...
{
"account": {
"user": {
"email": "attacker@malicious.com",
"first_name": "John",
"last_name": "Doe",
"password": "securepassword",
"company": "Malicious Inc."
}
}
}By modifying the email parameter in the intercepted request, the attacker can successfully register an account under the victim's email address without their knowledge.
Steps to Reproduce
- Register an Account: Create an account using any email address.
- Access the Verification Link: Click on the email verification link sent by the platform.
- Intercept and Modify the Request: Before submitting the verification form, capture the outgoing request using a proxy tool (e.g., Burp Suite) and replace the attacker's email with the victim's email.
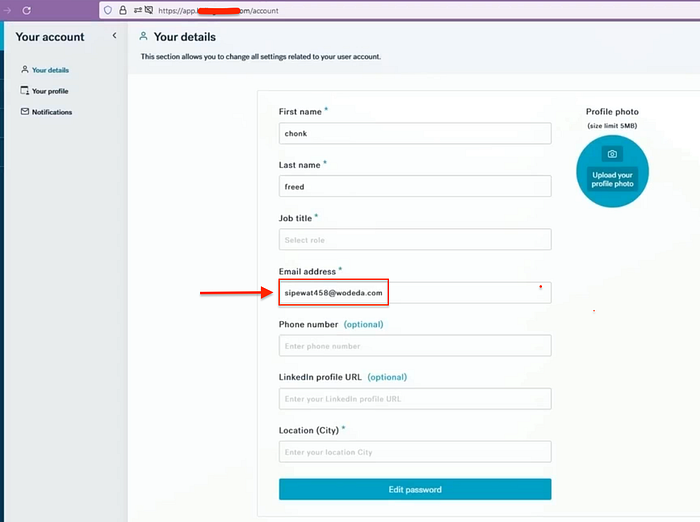
- Bypass Email Verification: Forward the modified request, return to the login page, and log in using the victim's email and the originally set password.
- Gain Unauthorized Access: The system registers the victim's email without requiring them to verify it, allowing unauthorized access.
Impact:
This vulnerability enables attackers to fraudulently verify and use victim email addresses, which can lead to identity theft, unauthorized access to sensitive information, and potential exploitation of user accounts.
Conclusion:
This security flaw creates an opportunity for attackers to manipulate the email verification flow, granting them the ability to falsely authenticate a victim's email address. The root cause is the application's failure to require re-verification when an email address is altered, allowing an attacker to hijack the verification link meant for their own email and use it to verify someone else's email instead.
Thanks for reading! Follow for more.
