Hello Everyone!
Today, I'm excited to share how I discovered an email disclosure vulnerability. Buckle up because this one was quite an interesting find!
The Hunt Begins
I was searching for a program that hadn't been heavily targeted by other hackers. To increase my chances, I chose a self-hosted program where *.domain.com was in scope. The platform was a Web3 wallet site, and the only way to log in was through a wallet connection.
After initial testing yielded nothing significant, I decided to switch gears and use a Google dork:
site:*.domain.com This helped me uncover some subdomains, and one in particular caught my attention: Portal.

First Observations
I immediately opened the subdomain and found a registration/login form. Curious, I registered a new account and noticed something strange: I never received a confirmation email. Regardless, I attempted to log in directly but was met with an error:
"No account exists."
This was odd.
Digging Deeper
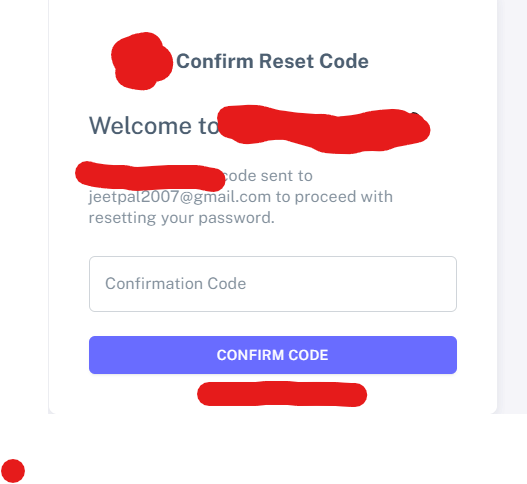
Next, I tried the password reset function. Here, the system asked for my username (not my email). I entered my username and waited for a reset email.
To my surprise, the error message revealed my entire email address in plain text!
Connecting the Dots
At this point, I recalled a similar vulnerability disclosed on HackerOne, where a logical flaw in the password reset process exposed LinkedIn users' phone numbers. The scenario was eerily similar.
Without wasting time, I documented my findings and submitted the report.
Current Status
The vulnerability is currently in the triage process, and I'm eagerly waiting for updates.
Final Thoughts
This experience reinforced the importance of paying attention to minor details, as even the most overlooked functionalities can lead to significant discoveries.
If you enjoyed this write-up, feel free to join our community of 1300+ hackers on Discord for free ethical hacking resources: 👉 discord.gg/Y467qAFM4X
Clap, share, and stay curious! 🚀
