Today, I want to share with you an interesting vulnerability I discovered in a bounty project, an XSS caused by file upload.
The vulnerable feature is located in the target's feedback section, which allows us to upload image files.
Let's take a look at the data packets.
First attempt.
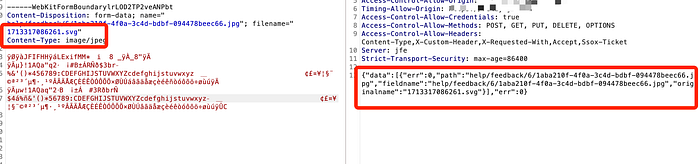
I changed filename="1713317086261.jpg" to filename="1713317086261.svg"
It seems it didn't work, as shown below.(Because the path to that SVG file could not be accessed.)
So, I made a second attempt.
I changed name="help/feedback/6/1aba210f-4f0a-3c4d-bdbf-094478beec61.jpg" to name="help/feedback/6/1aba210f-4f0a-3c4d-bdbf-094478beec61.svg"
Then, it errored.

I continued trying.

I tried svg, html, and xml, but all resulted in errors.
Just when I was about to give up, I suddenly thought to try xhtml.
So, I gave it a shot, and yes, it worked.

Afterwards, modify the file content to an XSS payload, then upload and access it.

Thank you for watching.

