- Potential to find sensitive information disclosure
- CVE Hunt
- Hidden Path Discovery:
/path1/path2/<pdfjs-viewer>, previously it was difficult to find/path1/path2. So now we fuzz both /path1 and /path1/path2 - Test injection vulnerabilities
1️⃣ Shodan Dork (82)
#title dependent
http.title:"PDF.js viewer"
#HTML comment dependent
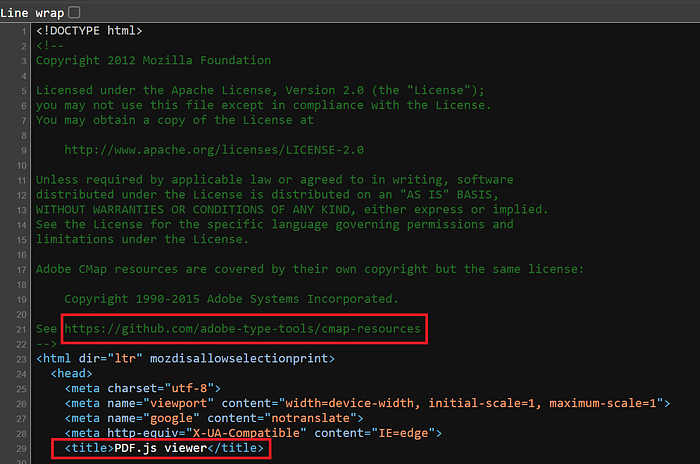
http.html:"github.com/adobe-type-tools/cmap-resources" http.html:"included from viewer.html"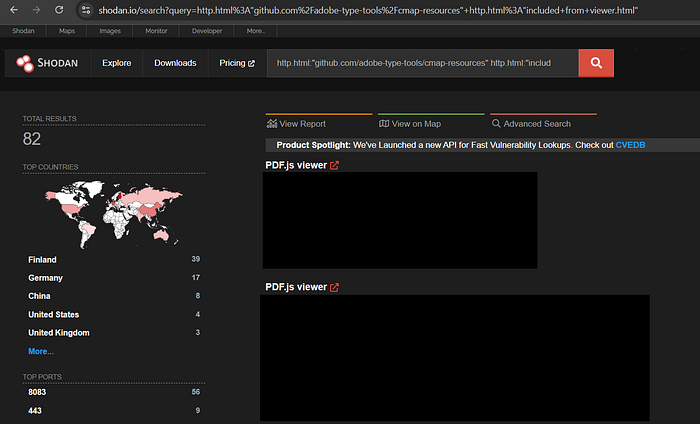
2️⃣ Google Dork (137)
inurl:/web/viewer.html site:target.tld
inurl:/web/viewer.html site:target.TLD.ccTLD
inurl:/web/viewer.html site:target.ccTLD
inurl:/web/viewer.html site:gov
inurl:/web/viewer.html site:gov.*
inurl:/web/viewer.html site:edu
inurl:/web/viewer.html site:edu.*
#parameterized endpoints
inurl:&
inurl:=
inurl:?
inurl:& inurl:= inurl:?

PDFJS Subdomain Hunt
site:pdfjs.*.* -site:pdfjs.express -site:pdfjs.community
site:pdfjs.*.*.* -site:pdfjs.express -site:pdfjs.community
site:pdfjs.*-*.* -site:pdfjs.express -site:pdfjs.community
//include pdfjs, pdf-js, pdf_js in your subdomain fuzzing wordlist3️⃣ Fofa Dork (354)
title="PDF.js viewer"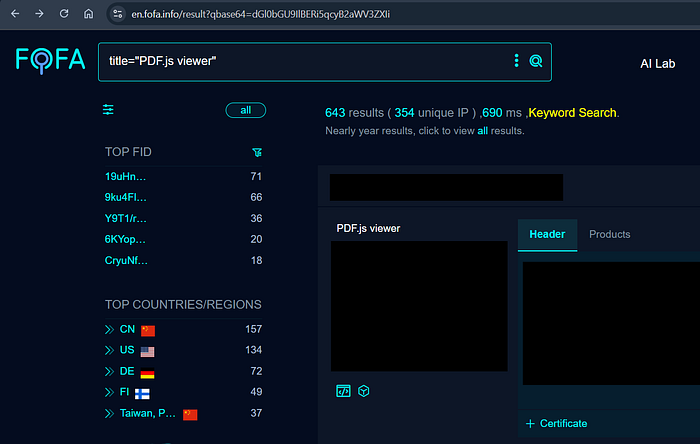
4️⃣ ZoomEye Dork (374)
title="PDF.js viewer"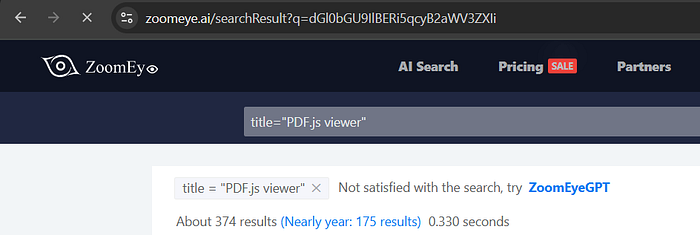
5️⃣ Netlas Dork (129)
http.body:("github.com/adobe-type-tools/cmap-resources" AND "included from viewer.html")
😈 Pro Tip of the day
How majority fuzz ? abc.xyz.123…..
How pros fuzz? abc-xyz.123_456……. (hyphens, underscores ,etc…)
Monitor the naming convention habits of the target
One hyphen can change your life :)
👇 Advanced Dorking Series

