ProConOS — a real-time operating system (RTOS) used in many industrial controllers — is quietly powering everything from factory floors to smart grids. But here's the problem: it's showing up online. And in many cases, it's wide open to attackers.
Here's what you need to know — and what to do about it.
🧠 What Is ProConOS?
Originally developed by KW Software (now part of Phoenix Contact), ProConOS runs on PLCs and embedded controllers used in:
- Industrial automation
- Energy infrastructure (including smart grid components)
- OEM embedded systems
- Building automation systems
You'll find it inside hardware from Phoenix Contact, WAGO, Berghof, and others. It communicates over TCP/IP and supports deterministic control — making it ideal for industrial environments.
🚨 The Problem: Internet Exposure
One major issue is that ProConOS doesn't use a fixed port. That means defenders can't rely on consistent network signatures.
- Sometimes it's TCP/1200
- Sometimes it's TCP/49152 or higher
- Sometimes… it's whatever the vendor decided
This inconsistency makes it harder to detect and monitor.
But that's not the worst part.
🔓 No Encryption. No Authentication.
Many ProConOS deployments lack basic security controls. That includes:
- No encryption
- No authentication
- Open debug/config interfaces
This opens the door to:
- Remote code execution
- Configuration theft
- Unauthorized command injection
- Full system compromise
Some of these issues are well-documented, such as CVE-2022–40145, which describes a ProConOS vulnerability leading to unauthenticated memory write.
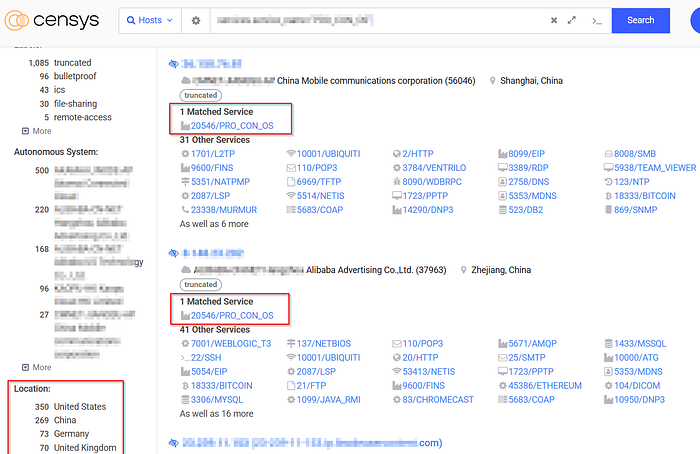
🌍 The Internet Can See You
Using Censys, a scan revealed 1,128 ProConOS endpoints exposed to the internet.
The U.S. has the highest number of exposed systems — an obvious red flag for industrial cybersecurity teams.
🛡️ What You Can Do Right Now
ProConOS isn't inherently insecure. It just wasn't built for a hyperconnected world where anyone can scan for PLCs like a search engine. Here's how to stay ahead:
1. Segment Your Network
Keep your OT network isolated. No direct access from corporate networks or the internet.
2. Block High-Risk Ports
Shut down any public-facing ProConOS ports (especially TCP/1200 and high TCP ranges).
3. Use ICS-Aware IDS Tools
Deploy and tune tools like Zeek or Suricata to detect unusual activity in OT protocols.
4. Secure Remote Access
VPNs are mandatory. So is multi-factor authentication (MFA).
5. Patch Known Vulnerabilities
Address CVEs like 2022–40145 immediately. Review vendor firmware advisories regularly.
6. Follow ICS Standards
Adopt best practices from IEC 62443 and NIST 800–82. These frameworks exist for a reason — use them.
Final Word
ProConOS was never designed to be discoverable on the open internet. But that's the reality we live in.
If you're running ProConOS-powered equipment, it's time to ask: ➡️ Can someone find it from a browser? ➡️ Can they log in without credentials?
If the answer is yes — or even maybe — it's time to lock it down.
Don't wait for an incident to take ICS security seriously. Act now. Protect your systems before someone else finds them first.
This research part of oaps_another_attack_surface series, another interesting blog about industrial exposed: From Packaging Lines to Hackers' Goldmine: The Hidden Risk of PCOM And you found me LinkedIn
