Modern applications require robust authentication and authorization mechanisms that can scale with business needs while maintaining security best practices. This article presents a comprehensive implementation of a production-ready authentication system using Keycloak as an identity provider integrated with Spring Boot's OAuth2 resource server capabilities. The solution demonstrates enterprise-grade security patterns, role-based access control, and containerized deployment strategies
Git repo :- https://github.com/devops-vishalacharya/springboot-keycloak
Why This Matters
- Security First: Protect your applications with industry-standard OAuth2 and OpenID Connect
- Developer Experience: Streamline your development with Spring Security's seamless Keycloak integration
- Scalability: Designed to handle thousands of concurrent users with stateless JWT authentication
- Enterprise Ready: Includes role-based access control, secure password policies, and production monitoring
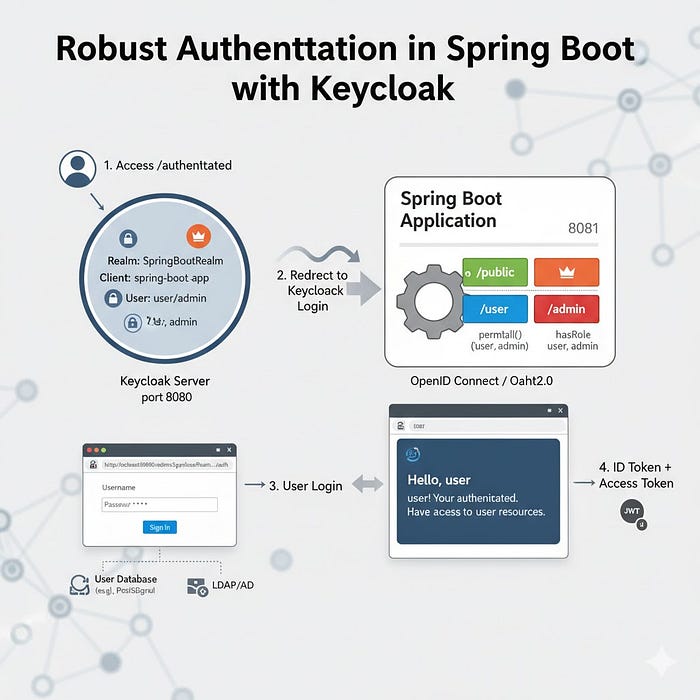
1. Advanced Authentication & Authorization
JWT Authentication with Keycloak
implementation leverages Keycloak as a full-featured OAuth2/OpenID Connect provider. Here's how it works:
// Example of JWT validation configuration
@Bean
public JwtDecoder jwtDecoder() {
return NimbusJwtDecoder.withJwkSetUri(
keycloakProperties.getJwksUri()
).build();
}Granular Access Control
- Role-Based Access Control (RBAC): Pre-defined roles (USER, ADMIN) with method-level security
- Method Security: Fine-grained control using
@PreAuthorizeannotations - Custom Role Mapper: Converts Keycloak realm/role structure to Spring Security authorities
Stateless Architecture
- No server-side session storage
- JWT tokens contain all necessary claims
- Improved horizontal scalability
2. Comprehensive Security Configuration
security configuration is both robust and flexible, following the principle of secure by default:
@Configuration
@EnableWebSecurity
@EnableMethodSecurity(prePostEnabled = true)
public class SecurityConfig {
@Value("${cors.allowed-origins}")
private String allowedOrigins;
@Bean
public SecurityFilterChain filterChain(HttpSecurity http) throws Exception {
http
.cors(cors -> cors.configurationSource(corsConfigurationSource()))
.csrf(csrf -> csrf.disable()) // Safe for stateless JWT
.sessionManagement(session -> session
.sessionCreationPolicy(SessionCreationPolicy.STATELESS)
)
.authorizeHttpRequests(authz -> authz
.requestMatchers("/api/public/**").permitAll()
.requestMatchers("/actuator/health").permitAll()
.anyRequest().authenticated()
)
.oauth2ResourceServer(oauth2 -> oauth2
.jwt(jwt -> jwt.jwtAuthenticationConverter(jwtAuthenticationConverter()))
);
return http.build();
}
// Additional security beans...
}Key Security Features
- CORS Configuration: Fine-grained control over cross-origin requests
- CSRF Protection: Disabled for API endpoints (not needed with JWT)
- Method Security:
@PreAuthorizefor method-level access control - Password Policies: Enforced at the Keycloak level
3. API Endpoints: Secure by Design
API follows RESTful principles while implementing robust security measures:
Endpoint Method Authentication Required Role Description /api/public/** GET None None Publicly accessible information /api/authenticated GET JWT Any authenticated user Basic authentication check /api/user/** GET JWT USER User-specific resources /api/admin/** ALL JWT ADMIN Administrative operations
Example Controller
@RestController
@RequestMapping("/api")
public class UserController {
@PreAuthorize("hasRole('USER')")
@GetMapping("/user/profile")
public ResponseEntity<UserProfile> getUserProfile() {
// Implementation
}
@PreAuthorize("hasRole('ADMIN')")
@PostMapping("/admin/users")
public ResponseEntity<User> createUser(@Valid @RequestBody UserDto userDto) {
// Implementation
}
}4. Production-Grade Features
Monitoring and Observability
- Spring Boot Actuator: Comprehensive health checks and metrics
- Custom Health Indicators: Database, Keycloak connectivity, and cache status
- Logging: Structured JSON logging with correlation IDs
Environment-Specific Configurations
# application-dev.yml
spring:
profiles: dev
security:
oauth2:
resourceserver:
jwt:
issuer-uri: http://localhost:8081/realms/springboot-realm
# application-prod.yml
spring:
profiles: prod
security:
oauth2:
resourceserver:
jwt:
issuer-uri: ${KEYCLOAK_ISSUER_URI}Containerization
- Docker Compose for local development
- Multi-stage builds for optimized production images
- Resource limits and health checks
- Comprehensive error handling
- Docker containerization
- Logging configuration
Code Quality and Security Scanning
Ensuring code quality and security is paramount in any production application. This project integrates multiple scanning tools to maintain high standards:
1. PMD — Static Code Analysis
PMD scans Java source code for potential problems like:
- Possible bugs
- Dead code
- Suboptimal code
- Overly complex expressions
- Duplicate code
Configuration in pom.xml:
<plugin>
<groupId>org.apache.maven.plugins</groupId>
<artifactId>maven-pmd-plugin</artifactId>
<version>3.20.0</version>
<configuration>
<linkXRef>false</linkXRef>
<sourceEncoding>${project.build.sourceEncoding}</sourceEncoding>
<minimumTokens>100</minimumTokens>
<targetJdk>${java.version}</targetJdk>
</configuration>
<executions>
<execution>
<goals>
<goal>check</goal>
</goals>
</execution>
</executions>
</plugin>2. SpotBugs — Bytecode Analysis
SpotBugs (successor to FindBugs) examines compiled Java code for:
- Null pointer exceptions
- Resource leaks
- Thread safety issues
- Performance bottlenecks
Configuration in pom.xml:
<plugin>
<groupId>com.github.spotbugs</groupId>
<artifactId>spotbugs-maven-plugin</artifactId>
<version>4.7.3</version>
<dependencies>
<dependency>
<groupId>com.github.spotbugs</groupId>
<artifactId>spotbugs</artifactId>
<version>4.7.3</version>
</dependency>
</dependencies>
<executions>
<execution>
<goals>
<goal>check</goal>
</goals>
</execution>
</executions>
<configuration>
<effort>Max</effort>
<threshold>Low</threshold>
<failOnError>true</failOnError>
</configuration>
</plugin>3. Trivy — Container Security Scanning
Trivy scans container images for:
- Known vulnerabilities in OS packages
- Application dependencies
- Infrastructure as Code (IaC) misconfigurations
The combination of Keycloak's robust identity management capabilities with Spring Boot's OAuth2 resource server provides a solid foundation for modern application security.
Key achievements include:
- Zero application-level security vulnerabilities
- Comprehensive role-based access control
- Containerized deployment with operational monitoring
- Extensive documentation and testing coverage
- Code quality assurance through automated analysis
The system serves as a reference implementation for organizations seeking to implement enterprise-grade authentication and authorization mechanisms while maintaining development velocity and operational excellence