So, you've got the skills, the curiosity, and maybe a slightly mischievous glint in your eye when you look at a website's code. You're ready to dive into the world of Bug Bounty programs, where ethical hacking meets real-world impact (and sometimes, real-world cash!). Think of it as a treasure hunt, but instead of gold, you're looking for digital weaknesses.
This guide is for you, whether you're just starting out or looking to sharpen your focus. We'll cut through the jargon and get straight to what matters, with a sprinkle of humor because, let's be honest, hacking can be a serious business, but it doesn't always have to be.
What Exactly _Is_ Bug Bounty and How Does It Work?
At its core, a Bug Bounty program is a deal: companies offer rewards to ethical hackers who find and report security vulnerabilities in their systems. It's a win-win: companies get stronger security, and hackers get to hone their craft, earn some income, and build a stellar reputation.
There are two main flavors of programs out there:
- In-house programs: These are run directly by tech giants like Google or Microsoft. They're often massive and well-funded, but can be intimidating for newcomers.
- Bug Bounty platforms: These are like matchmakers (think HackerOne, Bugcrowd, Intigriti, YesWeHack). They connect hackers with companies, handle the admin, and manage payouts. For beginners, these platforms are usually your best bet because they offer standardization and support.
Types of Bug Bounty Programs: What's Your Flavor?
Not all programs are created equal, and knowing the differences can save you a lot of time (and potential headaches).
- Public Programs: Open to everyone! They're a fantastic starting point for newbies, but be prepared for a crowd. High competition means more duplicate findings, so you gotta be quick!
- Private Programs: These are by invitation only. Less competition, higher payouts, and access to fresh targets. How do you get invited? By proving your mettle in public programs, of course!
- Vulnerability Disclosure Programs (VDPs): These don't always offer cash, but they're gold for gaining experience, getting recognition, and building that all-important reputation. Consider them your personal "sandbox" for learning without the pressure of a bounty. I'd actually say, start with VDPs to gain experience and reputation, then gradually move to Bug Bounty Programs.
- Time-Limited Programs: These are intense, highly competitive, and often tied to specific events (like product launches). They offer elevated rewards, but are generally best left for seasoned hackers who thrive under pressure.
Key Criteria for Choosing Your Next Hunt
So, you're ready to pick a program. What should you look for?
Payout Structure and Reliability
It's all about the rewards — dollars, euros, or your currency of choice! Rewards typically depend on the severity and impact of the vulnerability. The more critical, the higher the payout. Some programs also consider the quality of your report, so make it shine!
Payout speed is crucial. Who wants to wait months for their hard-earned cash? Check the "time to bounty" metric on a program's page. While the average can be 2–3 months, some platforms boast quicker turnarounds after approval (e.g., Intigriti claims 3–5 days, Bugcrowd pays out every Wednesday). Prioritize programs with transparent and speedy payout statistics.
Table 1: Industry Average Bug Bounty Payouts by Severity (Approximate)
_______________________________________________________
|Severity Category (CVSS Score)|Industry Average (USD)|
|------------------------------|----------------------|
|Critical (9-10) |$7,200 |
|High (7-8.9) |$3,000 |
|Medium (4-6.9) |$1,100 |
|Low (0.1-3.9) |$254 |
-------------------------------------------------------Scope and Targets: Know Your Playground
A clear scope is your map to the treasure. It's a list of permitted targets. Avoid programs with vague scopes — that's a recipe for accidentally going out of bounds (and potentially getting yourself in hot water).
- Limited Scope: Specific targets (e.g., example.com). Easy to understand, but fewer opportunities.
- Broad Scope: Includes subdomains (*.example.com). More ground to cover, more potential bugs.
- Open Scope: Any external assets owned by the organization. This is where the wild west of hacking begins!
For experienced hackers, broad or open scopes offer more opportunities. Always prioritize "primary" assets for higher payouts.
Response Time and Triage Quality: Don't Get Ghosted!
Imagine finding a killer bug, sending in a detailed report, and then… crickets. A quick response time and efficient triage (initial vulnerability verification) are hallmarks of a good program. Slow responses are a red flag and can be seriously demotivating. Look for programs with transparent and low metrics for "time to first response" and "time to triage."
Table 2: Average Response Times (Examples)
__________________________________________________________________________
|Platform / Program|Average Time to First Response|Average Time to Triage|
|------------------|------------------------------|----------------------|
|Bugcrowd |4-5 business days |5 days |
|Intigriti |1 day |2 day |
|HackerOne |2 business days |10 business days |
--------------------------------------------------------------------------
Reputation System and Progress: Your Hacking Street Cred
Your reputation is your currency in the Bug Bounty world. It measures the quality of your findings and directly impacts your invitations to those sweet, sweet private programs. Focus on submitting high-quality reports, even if the initial bounties are lower. It's a long-term investment in your hacking career.
Community and Support: We're All in This Together
A strong community and robust support (forums, learning resources, dispute resolution) are invaluable, especially for learning and growing. Check out how programs handle disputes. For example, Intigriti offers compensation for platform errors, while some HackerOne users have reported "radio silence" in the past.
Available Tools and Resources: Your Hacking Toolkit
Many platforms offer fantastic educational materials (like Hacker101, Bugcrowd University, Hackademy, Dojo) and specialized tools (e.g., YesWeHack with YesWeBurp, PwnFox; HackerOne with Hai AI). These resources can significantly boost your efficiency.
A Quick Peek at the Leading Platforms
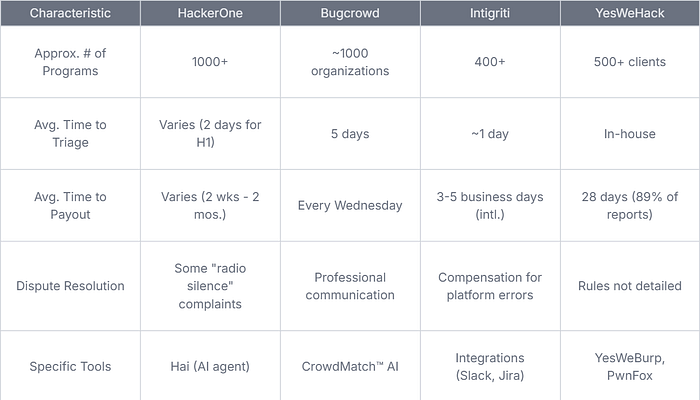
- HackerOne: The biggest player in the game (around 39.8% market share) with over 1000 programs and over $380 million paid out. Their Hacker101 educational resources are extensive. However, some users have expressed concerns about dispute resolution.
- Bugcrowd: They emphasize "engineered triage" and use AI to match hackers (CrowdMatch™ AI). They boast paying 100% of rewards and have good triage metrics.
- Intigriti: A leading European platform with over 400 programs. Known for fast payouts after processing and a transparent mediation process with compensation for platform errors.
- YesWeHack: Founded by ethical hackers, they have a strong focus on education (Dojo) and their own tools (YesWeBurp, PwnFox). They also claim fast payouts (89% within 28 days).
Table 3: Quick Comparison of Leading Bug Bounty Platforms
Real-Life Riches: Successful Bug Bounty Stories
Want some inspiration? Companies are shelling out serious dough for critical vulnerabilities.
- In 2019, Google paid over $6.5 million through its Google Vulnerability Reward Program. One researcher alone bagged $161,337 for a Google Cloud vulnerability!
- In 2018, Facebook dished out over $1.1 million to hackers. One lucky participant pocketed $100,000 for an Instagram flaw.
- In 2020, Apple announced it had paid over $3.7 million to hackers in their program, with one hacker receiving $250,000 for a critical iOS vulnerability.
Conclusions and Your Hacking Action Plan
- Start with VDPs for experience, aim for private programs for profit. Use public programs to build skills and reputation, which will unlock those higher-paying private invites.
- Prioritize reputation as a long-term investment. Always submit high-quality reports, even if the initial rewards aren't huge. This opens doors to better opportunities.
- Carefully examine the program scope and targets. Choose programs with clearly defined boundaries. For experienced hackers, broad or open scopes offer more hunting grounds.
- Choose platforms with transparent and fast response and payout metrics. Slow response times are a major red flag. Always check a program's public metrics.
- Leverage the community and educational resources. An active community and access to quality learning materials are invaluable for growth and knowledge sharing.
- Evaluate platform-provided tools. Specialized tools or AI features can significantly boost your efficiency and help you sniff out those elusive bugs.
Pro Tip:
- Check out t.me/OfficialHacKitBot! One of its cool features is automatic alerts for new Bug Bounty programs. Getting in early on a fresh program can seriously increase your chances of being the first to find a bug and grab that bounty!
- What 10 websites and applications do you use most often in your daily life? Seriously, tell me! Got something more niche that has a Bug Bounty program? Even better! The best targets are often the ones you know inside and out.
— -
Join My InfoSec Journey! 🚀
On my Telegram channel, the worlds of InfoSec, pentesting, and bug bounty hunting come together. Here's what you'll get:
- Exclusive techniques and tips to uncover vulnerabilities like a pro. - Step-by-step guides for bug bounty hunters. - Quests with rewards and challenges for real-world experience. - Latest trends and news to stay ahead in cybersecurity.
Level up your skills, explore deeper methodologies, and join a growing community of security enthusiasts!
- Telegram: TheHackerSaga
- LinkedIn: Aleksandr Fastenko
- Twitter: @fastenko89038
- HacKitBot(Telegram Bot): t.me/OfficialHacKitBot
Let's unlock new levels of knowledge and success in InfoSec — together! 🛡️
Author: Nebty

