On October 2025, elite European law-enforcement agencies pulled off a major takedown of a sophisticated cybercrime-as-a-service (CaaS) network that weaponised SIM cards in unprecedented volume. The implications are huge for telecom operators, businesses, and everyday users alike.
What happened
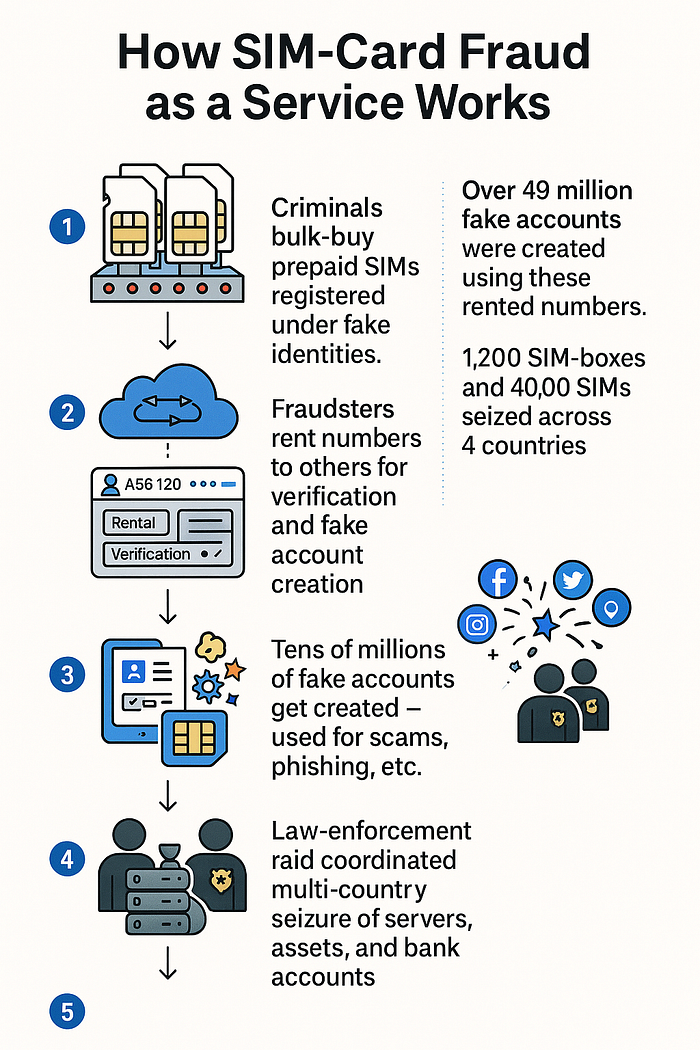
In a joint operation involving Europol, Eurojust, and authorities in Austria, Estonia, Finland and Latvia, a criminal network codenamed "SIMCARTEL" was dismantled. Source. Here are the key facts:
- The network operated a fleet of about 1,200 "SIM-box" devices and 40,000 active SIM cards, which were used to rent telephone numbers and facilitate criminal operations.
- These numbers were registered from more than 80 countries and then used to create fake online accounts, verify identities, hide locations and conduct fraud at scale.
- More than 49 million fake accounts are estimated to have been created through this infrastructure.
- The network was linked to over 3,200 individual fraud cases in Austria and Latvia alone, with losses of about €4.5 million in Austria and €420,000 in Latvia so far.
- Law-enforcement seized luxury vehicles, froze bank & crypto accounts, shut down websites that facilitated the service, and disrupted servers supporting the operation.
Why it matters
The rise of "fraud infrastructure as a service"
This is not the run-of-the-mill scam. What's emerged is a business-model where criminals provide the platform — SIM cards, phone numbers, verification services — for other actors to deploy fraud. The SIM-box farm is essentially cybercrime infrastructure for hire.
"The online service created by the criminal network offered telephone numbers registered to people from over 80 countries for use in criminal activities." The Hacker News+1
Why SIM cards? Because they break one of the key defences.
Many verification systems rely on a phone number: "we'll text a code", "enter the number", "one-time password sent to this number". By controlling large volumes of legitimate-appearing numbers, criminals can:
- Create fake user accounts for social media, marketplaces, financial services.
- Carry out phishing, business-email-compromise, "daughter-son" emergency scams, fake investment schemes. BankInfoSecurity+1
- Hide their true origin location, rotate numbers, evade tracking.
- Automate scams at scale: the network supported creation of tens of millions of accounts.
The damage is real and growing
Losses of millions of euros have already been traced. But the real damage may be far larger, given the volume of fake accounts and the global reach of the infrastructure. And the bigger worry: this model can scale, be replicated, and target any industry that uses phone-based identity or verification.
What this means for businesses & users
For telecom operators
- If SIM-cards are being used in bulk for illicit purposes, your network may become an unwitting facilitator of crime. This means reputational, regulatory and legal risk.
- Monitoring SIM-box activity, number-rotations, abnormal registration volumes should become a priority. (Research shows detecting SIM-box devices via latency/behaviour anomalies is possible.) arXiv
- Collaborate with law‐enforcement and cross-border agencies; these crimes often transcend national jurisdictions.
- Make sure verification/number-issuance processes include strong identity checks, fraud-flagging, and ideally multi-factor verification beyond just SMS.
For online services & platforms
- Don't rely on "phone number = unique user" alone. Accepting phone-verified accounts as inherently trustworthy is risky when such number-rental services exist.
- Implement fraud detection layers: suspicious behaviour after account creation, rapid switching of numbers, unusual geographies or IP patterns.
- Educate users: phishing via WhatsApp, marketplace scams using numbers rented from such services are rising. For example, "daughter‐son number change emergency" scam:
- "Calls from multiple numbers… the callers claiming his Aadhaar card was being misused … and demanding urgent payments" The Hacker News+1
For everyday users
- Be wary of unsolicited calls/texts even if the number looks local. The scammer can make it look like your child, bank, or another trusted party.
- Don't assume "phone verified account" equals secure. Always enable strong authentication (e.g., app-based MFA, hardware token) where available.
- Monitor your accounts (email, banking, social) for account creation alerts, login from new devices, number changes.
- If your network operator offers "number portability" or "SIM swap" requests, ensure you enhance the security: PINs, personal verification, immediate alerts.
Lessons & key take-aways
- Infrastructure matters: The big shift in cyber-fraud is that infrastructure (rented numbers, fake accounts, SIM-boxes) is now being commercialised.
- Scale + anonymity = danger: With tens of thousands of SIMs and millions of accounts in play, the volume of attacks can explode.
- Cross-border & collaborative: The takedown happened across multiple countries — Austria, Estonia, Finland, Latvia etc. Fraud knows no borders.
- Verification is weak unless layered: Phone number alone is a weak pillar of identity/verification. Add device checks, behaviour analytics, MFA.
- Everyone has a role: Telecoms, platforms, users — all must play a part. If any link is weak, frauders exploit it.
What's next? The future of SIM-based fraud
- As networks evolve (5G, IoT, eSIM) attackers will adapt. The ability to spin up large volumes of numbers remotely will likely increase.
- Regulators may tighten requirements for number issuance, SIM portability, cross-carrier verification.
- Fraud detection will lean more on machine learning: spotting unnatural patterns, number-rotation behaviour, SIM-box latency anomalies (see recent academic work). arXiv
- For the cyber‐crime-as-a-service model: expect more offerings, more "rent-a-fraud-kit" platforms. This takedown is just one node.
Conclusion
The SIM-card still seems innocuous: a little plastic card, a number. But as this major criminal takedown shows, when organised crime builds rental-services around it, it becomes a powerful tool for mass-fraud. Whether you're a telecom operator, an online service, or an everyday user, it's time to regard the phone number not as a guarantee of identity — but as a potential vulnerability.
Protect your infrastructure. Protect your identity. And treat number-based verification with the scrutiny it now deserves.

