Ever wondered what happens when OAuth trusts you a little too much? I found a way to log into any account — no password, just an email and a little creativity.Here's how an old but gold OAuth misconfiguration quietly handed me the keys.
This happened while I was analyzing an invited Bugcrowd program few years ago , specifically hunting for authentication bypasses — one of my favorite things to break.Initially, I poked around the classic username + password login flow. Nothing special there. But then… I shifted my focus to the OAuth configuration — and that's where the gold was hiding: a clean, critical bug. Here's how the bug worked:
Proof of Concept (PoC):
1. First, I created a Facebook account using only a phone number — no email attached. 2. Logged into that account and went to the target site's login page: https://[TARGET_DOMAIN]/login 3. Chose Sign in with Facebook and started intercepting the request (Burp Suite, of course). 4. After a few redirects, I spotted a POST request with Facebook profile data — it included parameters like first_name, last_name, and picture.
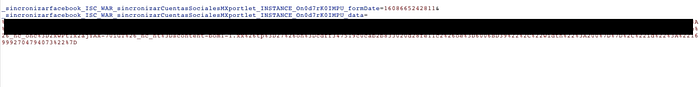
5. I manually injected an email parameter into the request, setting it to the victim's email address.
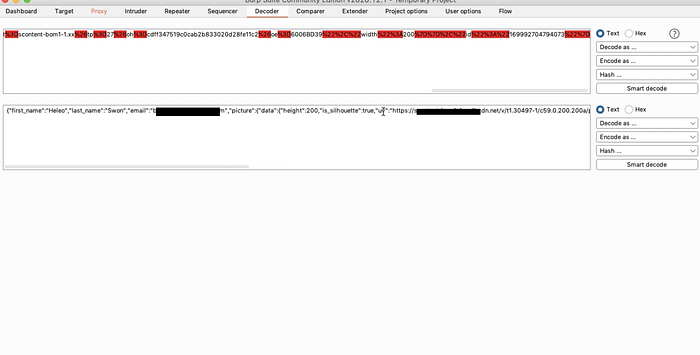
6. Forwarded the modified request, stopped intercepting, and boom — I was logged in as the victim.
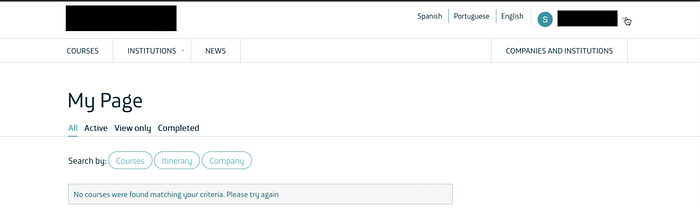
7. No credentials. No confirmation. Just complete authentication bypass. 8. Bonus: I could now change the victim's email, which meant full account takeover.
Impact:
Any user account could be taken over by simply knowing their email — no password, no confirmation needed. It opened the door for mass exploitation and full identity compromise.
I reported this issue to the program through Bugcrowd, and they accepted it as valid.
It was marked as a P1 vulnerability (highest severity), and I received a bounty of $$$$ — not bad for a few lines of misplaced trust in OAuth.
Conclusion: Sometimes, even the simplest misconfigurations lead to the loudest impacts.Keep digging — every overlooked corner might be hiding your next $$$$ moment.

