When I receive an invitation to an old program and decide to test it, I start by understanding the program's business and navigating its pages. Since it's an older program, I often check the What's New section for recently released features, paying close attention to security enhancements.
I noticed a new feature that lets Organization owners generate activation tokens to securely invite new members, instead of relying on user-supplied credentials. I decided to test the full flow, from creating an activation token to revoking it.
Environment Setup
I created two separate test accounts, one for the victim and one for the attacker, and completed the organization initialization for both. I then used the activation token feature to generate a token in each account. While testing, I reviewed Burp's history, copied the victim's activation token ID and the attacker's activation token ID, and pasted them into my notes.
Exploitation Flow
💡In a secure system, only the owner of an activation token should be able to revoke it, and any request from an unauthorized user should be rejected.
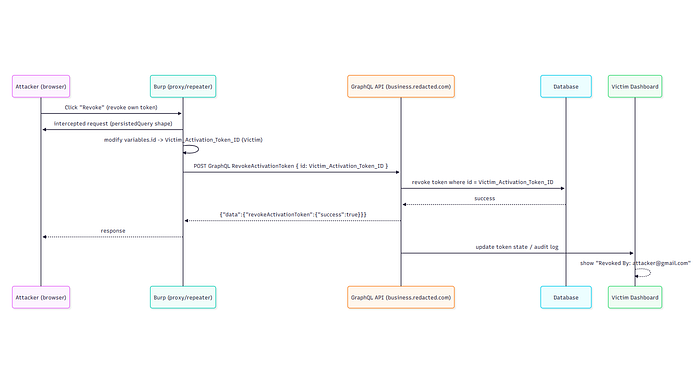
- As an authenticated attacker (User2), open the dashboard and click Revoke on an activation token while intercepting requests with Burp Proxy.
- Send the captured GraphQL revoke request to Burp Repeater.
- In Repeater, replace the attacker's token ID with the victim's activation token ID.
- Forward the modified request.
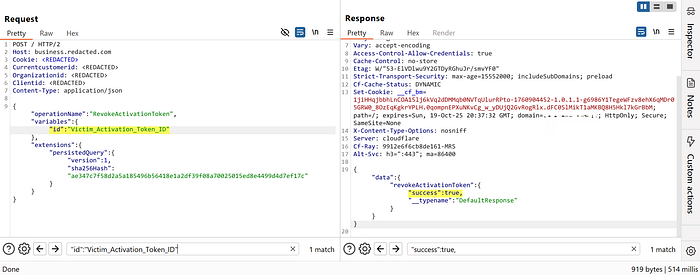
5. The server accepts and executes the revoke because it only validates that the caller is authenticated, but does not verify token ownership. 6. The victim's activation token is revoked, and the UI shows the action attributed to the attacker.
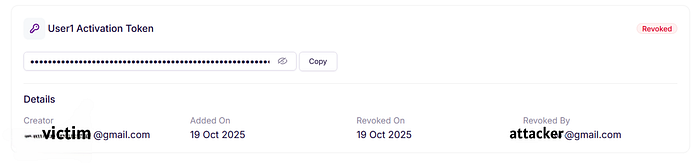
Impact
Allows an authenticated attacker to revoke other users' activation tokens.
Stay curious. Thanks!