I've spent years building tools for pentesters and security teams, and one thing has become clear: fixing vulnerabilities isn't the finish line — it's just another checkpoint.
Here's the truth most teams don't like to hear: patching without retesting leaves you exposed. On paper, the CVE might be closed. In practice, you may have shifted the risk somewhere else. And in 2025, where AI is amplifying how attackers discover and chain weaknesses, that's a risk you can't afford.
Patching Alone Creates a False Sense of Security
Most organizations measure themselves by patch speed. That's logical — it reduces exposure time. But I've seen too many cases where "fast patching" actually masked a deeper issue:
- Was the fix applied consistently across environments?
- Did staging and production both get updated?
- Did the change introduce new misconfigurations or IAM drift?
- Did it solve the root cause, or just silence the immediate symptom?
These blind spots aren't hypothetical. Attackers don't care about your SLA; they care about whether the door is really locked. And with AI-driven reconnaissance, they'll find the smallest crack.
Why AI Changes the Equation
Attackers today aren't limited by time or human fatigue. They're running LLM-powered tools that can:
- Generate tailored payloads
Reason across multiple service interactions
- Probe for lateral movement opportunities you never anticipated
This isn't brute force. It's intelligent, adaptive hunting. And if your remediation isn't validated through retesting, AI will find the gaps before you do.
Retesting Is Reenactment, Not a Checkbox
Retesting doesn't mean rerunning a scan. It means replaying the original exploit chain, in the real environment, after the fix. It means checking the context: IAM roles, adjacent services, network exposure.
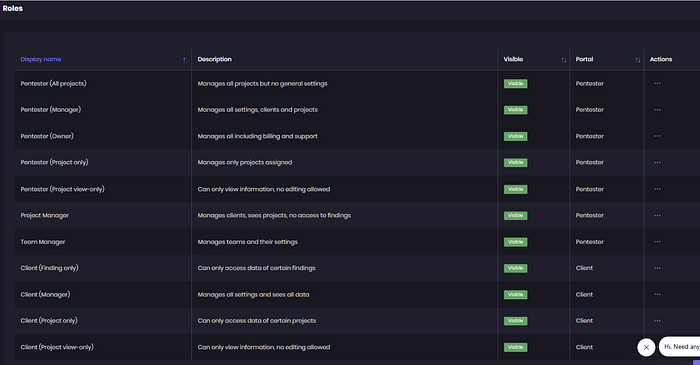
This mindset aligns with Continuous Threat Exposure Management (CTEM). Instead of "find, patch, and hope," CTEM is about simulate, validate, and close the loop — continuously. Retesting is the heartbeat of that loop. It turns fixes into measurable assurance, not theoretical compliance.
How We Built Retesting Into Cyver
When I started Cyver, I wanted to break away from the old pentesting cycle: find → report → fix → forget. That's why retesting is core to our approach.
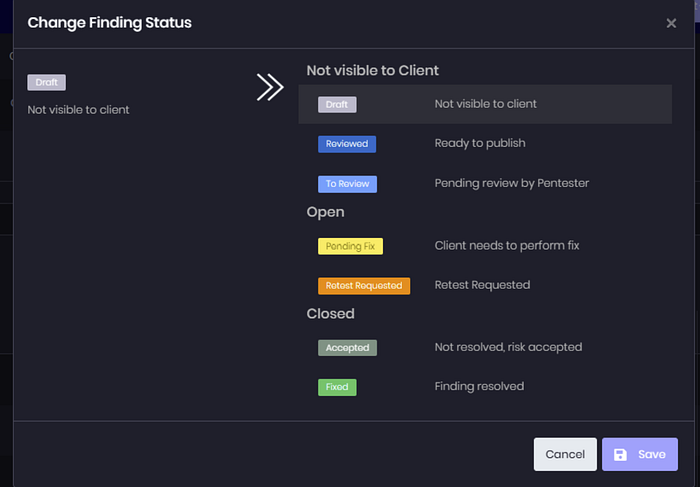
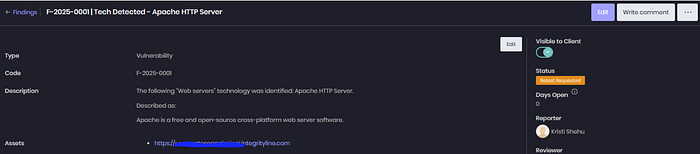
On Cyver Core, security teams and pentesters can:
- Re-execute test cases immediately after a fix
- Track attack paths across remediation stages
- Document whether an issue is still exploitable or resolved — with evidence
And because we built it for scalability, teams can standardize validation across clients and environments. Less human error, faster turnaround, stronger assurance.
From Reactive to Proactive Security
The attackers have already gone proactive. AI has given them reach and creativity at scale. If defenders stick to reactive patch-and-move-on cycles, they'll always be a step behind.
Retesting is how we catch up. It's how we verify fixes in real-world conditions, not just in Jira tickets. It's how security teams move from "we think it's fixed" to "we know it's closed."
And that's what gives me confidence in the work we do at Cyver — helping teams prove their security, not just assume it.
Because in the end, attackers don't read your reports. They test your systems. And you should too.