الْحَمْدُ لِلَّهِ الَّذِي عَلِمَ بِالْقَلَمِ، عَلَّمَ الإِنْسَانَ مَا لَمْ يَعْلَمْ، وَالصَّلَاةُ وَالسَّلَامُ عَلَى خَيْرٍ مُعَلِّمِ النَّاسِ الْخَيْرَ، مُحَمَّدٍ أَمَّا بَعْدُ
I'm Hosam Al-Sedawi (xs0x), a part-time bug hunter. Excited to share with you today a writeup about a really delicious vulnerability I found in a public program on Yes We Hack.
Let Me First Tell You About My Methodology
So, here's how I usually approach any program. I start by exploring it a bit, diving into every path and checking out every function.
Then I focus on each function individually, and the thing I concentrate on the most is finding all the "no's".
If you don't know what "no's" means: it's basically the restrictions, When the program tells you "nope, you can't do that" because your role doesn't allow it or because it breaks the program's logic. I document each function with all its "no's" in my notes, and honestly, this approach has helped me catch so many things.
Alright, so the program we're dealing with is an organization management SaaS for cloud admin stuff. It has three roles:
- Owner — Obviously has every permission in the program. Makes sense.
- Admin — Has almost the same permissions as the Owner, except they can't remove the Owner. Logical, right?
- Membership — Just a viewer in the org with some basic permissions that an Owner or Admin can grant.
The Vulnerable Function
The function we care about is the organization invitation feature, available only to Owners and Admins. The restriction here? It doesn't accept emails with special characters;
For example:
freePalestine@anyth.com ✓
freePalestine@ányth.com ✗And let me tell you, I discovered this approach through a Fares Walid (SirBugs) video — the guy is truly inspiring and I've learned a lot from his expertise.
The idea is straightforward: when the website blocks special characters in the UI
what if we could bypass that and send the invitation with the special character anyway?
I tried adding a special character through the UI and got
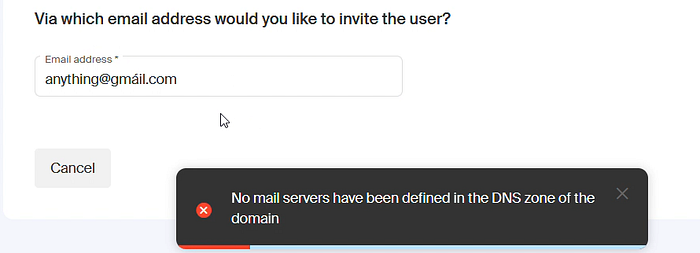
So I fired up Burp, intercepted the request, and tried adding the special character there?
Boooo…. wait There's a Problem… The invitation was sent to an email that doesn't actually exist anywhere — so how the hell do we even receive that email to register the account?
yup thats it
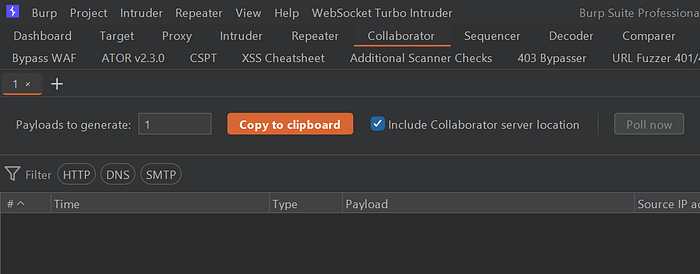
I used Burp Collaborator to receive the email (Unfortunately, Pro version only) If you don't have it, Pipedream is a solid free alternative that gives you your own domain, Or just ask ChatGPT for other options.
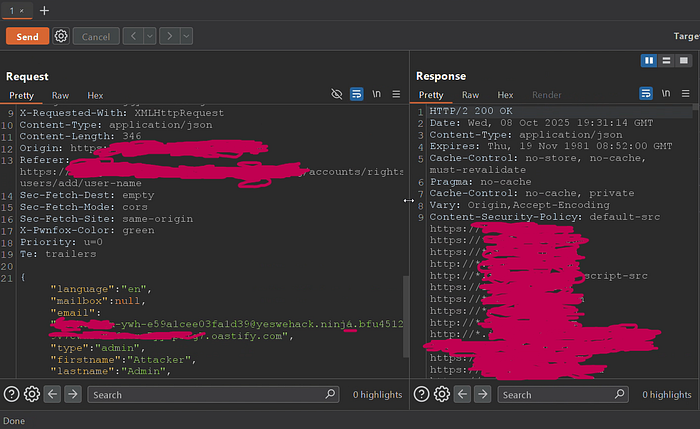
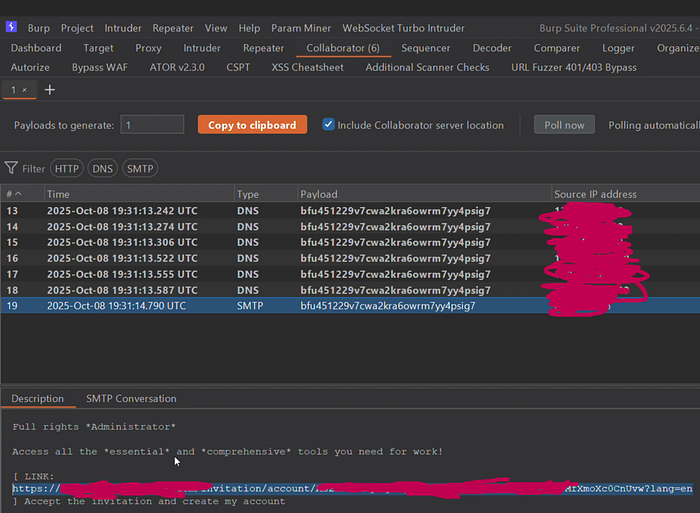
200 — OK and the email actually landed on my Burp Collaborator server!
So now, let's test the important part — can the Owner actually remove this attacker account?
And here's the kicker:
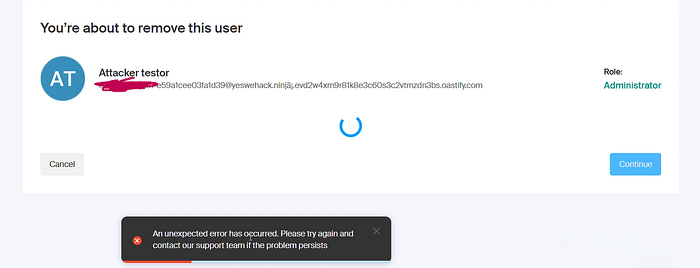
The Owner can't remove the attacker account! 💣
This is literally an Persistent organization takeover. This new admin account can't be removed by anyone, and it has almost the same permissions as the Owner. They can do whatever they want.
The Impact
Think about it: if any admin in your org (a hacked admin account or a malicious admin) finds out about this, they can create a second permanent admin account for themselves, and the Owner can't kick them out. That's a full organization takeover.
I reported it as High severity and I was hyped about my first bounty 😅
But guess what? The Plot Twist is
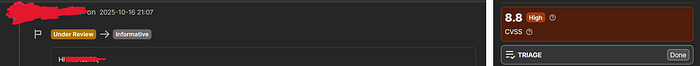
Yeah, That's it. Surprising? Nope — that's just how bug bounty work, man. the client is always right. الحمد لله thank God anyway, I'm pretty sure they didn't actually understand the bug from their response, So I sent them a follow-up email with some resources about this vulnerability and why it's actually critical/high. If they respond, I'll let you know.
anyway This is only my first month doing bug bounty, and while this isn't my first valid bug Alhamdulillah, but all my previous findings were either VDPs, duplicates, or Informative on HackerOne and other platforms. But HackerOne is still my favorite platform despite all its flaws, and I still love it
See you in the next writeup after I get that first bounty inshallah.

Peace. ✌️