Disclaimer: The techniques described in this document are intended solely for ethical use and educational purposes. Unauthorized use of these methods outside approved environments is strictly prohibited, as it is illegal, unethical, and may lead to severe consequences.
It is crucial to act responsibly, comply with all applicable laws, and adhere to established ethical guidelines. Any activity that exploits security vulnerabilities or compromises the safety, privacy, or integrity of others is strictly forbidden.
Table of Contents
Summary of the Vulnerability
Parameter cloaking is a web cache poisoning technique that exploits discrepancies in how different components of a web application handle query parameters. In this lab scenario, the cache system ignores certain parameters (such as UTM tracking values) when generating cache keys, while the back-end application still processes them. This inconsistency creates an opportunity for attackers to inject malicious payloads using "cloaked" parameters that appear harmless to the cache but are interpreted by the server.
The attacker's objective is to smuggle malicious input into a response that becomes cached and subsequently served to unsuspecting users. In the lab, this is demonstrated by injecting JavaScript (alert(1)) into the cached homepage, which is then executed in the victim's browser when they visit the poisoned page.
Steps to Reproduce & Proof of Concept (PoC)
① Open the Lab Environment
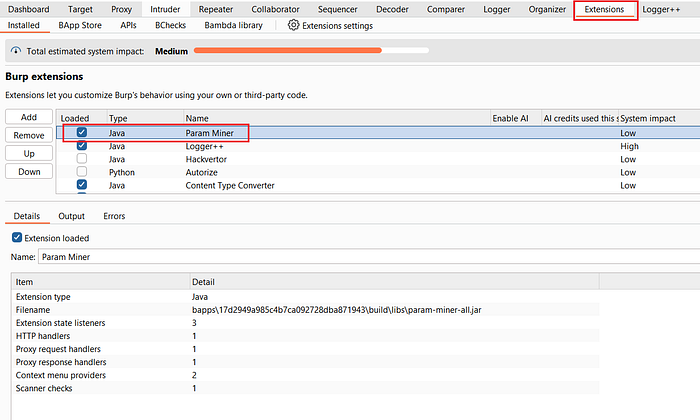
② Install and Enable Param Miner Extension
If you don't already have the Param Miner extension installed:
- Navigate to Burp Suite → Extensions → BApp Store.
- Search for Param Miner and install it.
- Once installed, ensure it's enabled.
This extension will help automate the discovery of hidden or ignored parameters.
③ Capture the Homepage Request
- In HTTP history, locate the request to the homepage:
GET / HTTP/2- Send this request to Repeater for further testing.
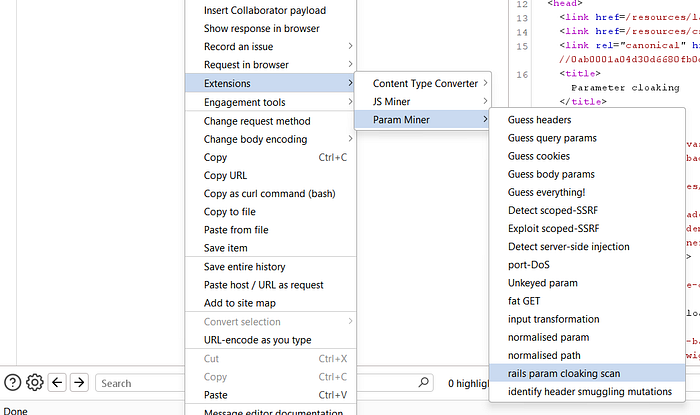
④ Run Param Cloaking Scan
- Right-click the request in Repeater.
- Select Extensions → Param Miner → Rails Param Cloaking Scan.
- Leave all settings at default and click OK.
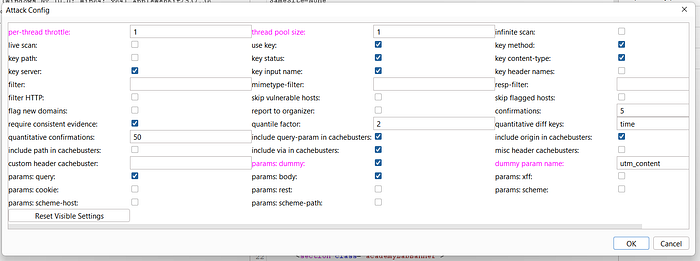
Burp Suite will now test for parameters excluded from the cache key.
⑤ Identify Vulnerable Parameter
- Wait for the scan to complete.
- You'll see a notification showing that the application is vulnerable when injecting with the
utm_contentparameter.
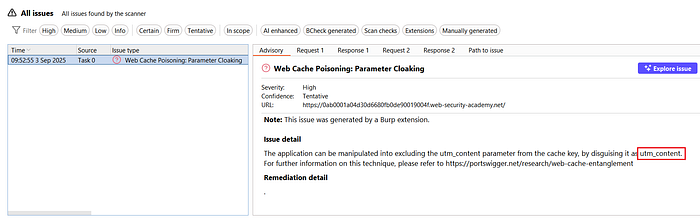
- Each request will reflect JavaScript from this endpoint:
/js/geolocate.js?callback=setCountryCookie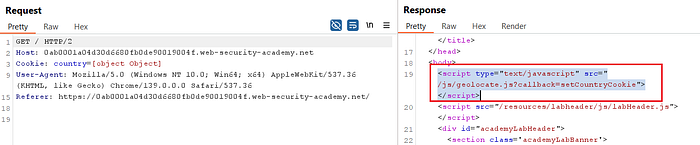
This indicates that the backend processes utm_content while the cache ignores it.
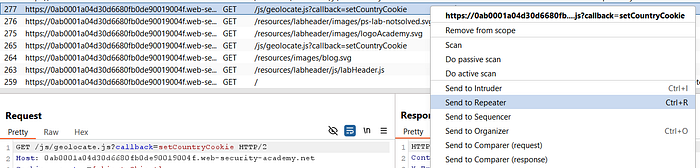
⑥ Inspect the Script
- In HTTP history, locate the
/js/geolocate.jsrequest. - Send it to Repeater.
- Notice that the script calls the
callbackparameter, but attempts to directly inject won't trigger an alert since the main logic is bound tosetCountryCookie.
⑦ Craft the Exploit Payload
- To bypass this restriction, use parameter cloaking with a semicolon (
;) to merge parameters:
?callback=setCountryCookie&utm_content=test;callback=alert(1)//- Here, the cache ignores
utm_content, but the backend interprets it, allowing the maliciouscallbackinjection to slip through.
⑧ Confirm the Payload Execution
- If Param Miner is still active, Disable it to prevent interference, because I have some issues while the extension is still active.
- Resend the crafted request multiple times.
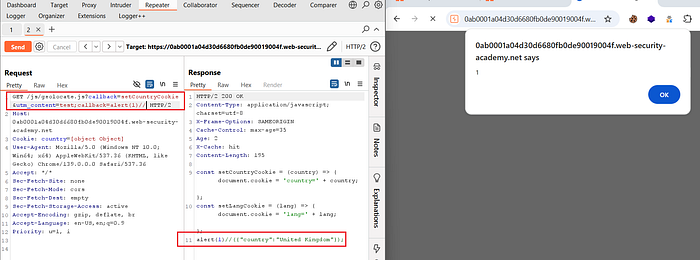
- Within a few seconds, the lab will be marked as solved, since a simulated user regularly visits the poisoned homepage.
Impact
Outside of a controlled environment, parameter cloaking poses serious risks for production systems. If an attacker successfully poisons cached responses, they can deliver persistent client-side attacks such as cross-site scripting (XSS) to large groups of users. This could lead to session hijacking, credential theft, or forced redirections to malicious domains.
Furthermore, because cached responses are often delivered by high-performance content delivery networks (CDNs), a single poisoned response can be propagated and served globally, amplifying the scale of the attack. This makes parameter cloaking a powerful vector for supply-chain style attacks where the compromise originates from shared infrastructure rather than targeting individual users directly.
📢 Enjoyed this post? Stay connected! If you found this article helpful or insightful, consider following me for more:
- 📖 Medium: bashoverflow.medium.com
- 🐦 Twitter / X: @_havij
- </> Github: havij13
🙏Your support is appreciated.