XSSTRON is a small Chromium browser built with Electron that watches the pages you visit and looks for XSS patterns.
It operates quietly in the background and displays proof-of-concepts (POCs) when something appears suspicious, including POST-based cases that many scanners overlook.
In this guide, I will show you what XSSTRON does and how to run it.

What XSSTRON actually does (short version)
- It's an Electron app, built on Chromium and Node.js.
- You browse as usual inside the app.
- XSSTRON injects tiny detectors into pages and listens for reflections or dangerous DOM sinks.
- If a payload seems to execute (or is reflected unescaped), it records the finding and shows a POC.
- It covers GET and POST flows.
This tool helps you find issues fast, but it won't replace careful manual testing. False positives happen. Always verify before you report anything.
Ethics: Only test systems you own or have permission to test.
Disclaimer:- This guide is educational. Only test systems you own or have explicit authorization to test. I'm not responsible for any damage, data loss, legal issues, or other consequences that may arise from using XSSTRON or following steps here. Always validate findings manually, disclose vulnerabilities responsibly, and follow local laws and organizational policies.
Installation
Make sure Node and npm are installed. On Debian/Ubuntu:
sudo apt update
sudo apt install nodejs npmThen:
git clone https://github.com/RenwaX23/XSSTRON
cd XSSTRON
npm install
npm startIf npm start fails, try running Electron directly (troubleshooting below).
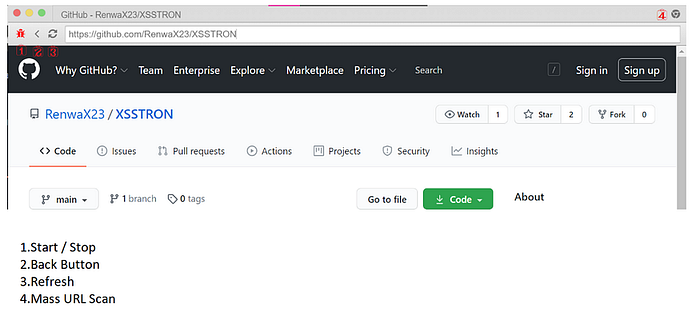
How to use it (really simple)
- Launch XSSTRON.
Browse websites in the window that opens.
When XSSTRON finds something, a results window appears with:
- URL
- POC payload (GET or POST)
- Short notes about where it was injected
Copy the POC, reproduce it in a safe environment, and confirm.
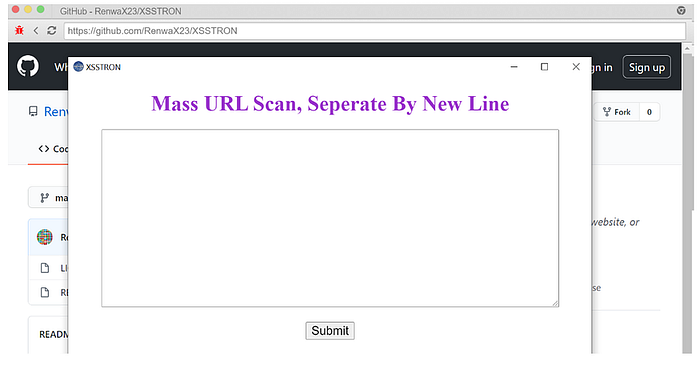
Example POCs
These are minimal, illustrative examples. The real POC XSSTRON generated will depend on the page.
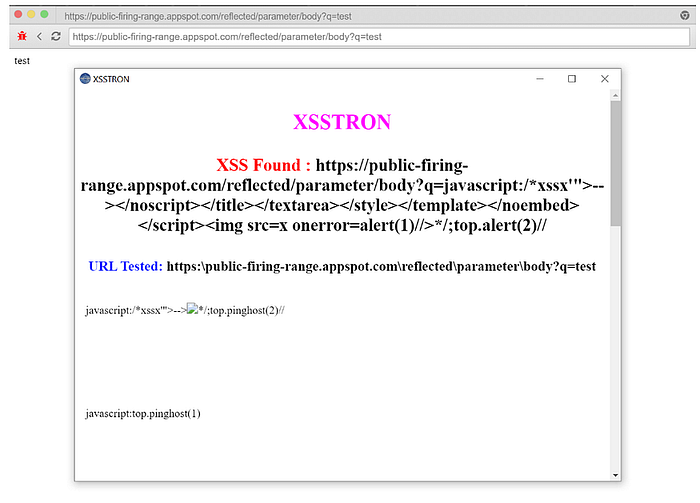
GET example
If a parameter is reflected directly into the HTML without escaping:
http://example.com/search?q=<script>alert(1)</script>If that payload gets injected and executes, XSSTRON flags it.
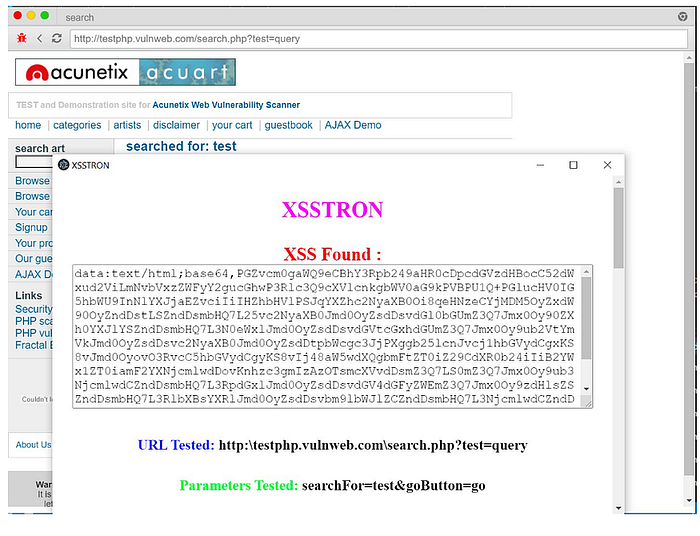
POST example
For a form that POSTs data, XSSTRON can craft or replay a POST like:
POST /submit HTTP/1.1
Host: example.com
Content-Type: application/x-www-form-urlencoded
name=<script>alert(1)</script>&age=30You can reproduce with curl:
curl -X POST "http://example.com/submit" \
-H "Content-Type: application/x-www-form-urlencoded" \
--data 'name=<script>alert(1)</script>&age=30'If the response contains the injected value without encoding, and it runs, that's a confirmed XSS.
How it's built
XSSTRON will typically include:
- Primary process:- creates windows, manages lifecycle (e.g.,
main.js). - Renderer/Browser window: the browsing surface.
- Preload / injected scripts:- small detectors that watch DOM changes, XHR/fetch responses, and form submissions.
- Scanner logic:- looks for standard sinks:
innerHTML,document.write,eval, unescaped attributes,onerror, etc. - Reporter UI: Lists findings and displays POCs.
If you open the repo, scan for main.js, preload.js, or folders named inject, detectors, or scanner , That's where the magic lives.
Tiny Electron example; demonstrates injection (educational)
This is a toy example to show a pattern, not production code.
main.js
const { app, BrowserWindow } = require('electron');
function createWindow() {
const win = new BrowserWindow({
width: 1200,
height: 800,
webPreferences: {
nodeIntegration: false,
contextIsolation: true,
preload: __dirname + '/preload.js'
}
});
win.loadURL('https://example.com');
}
app.whenReady().then(createWindow);preload.js
window.addEventListener('load', () => {
// naive detector: look for a known test payload
const html = document.documentElement.innerHTML;
if (html.includes('<script>alert(1)</script>')) {
console.log('Possible reflection: <script>alert(1)</script>');
// In a real app you would message the main process with the finding
}
});Real detectors are more sophisticated: they observe DOM mutations, hook XHR/fetch, and analyse responses and forms.
Troubleshooting: Linux pain points and fixes
Some Linux users (Kali, Debian, older distros) hit Electron-related issues. These steps fix most of them.
Try this sequence (works often on Debian/Kali)
sudo apt install npm
sudo npm install -g electron --unsafe-perm=true --allow-root
cd XSSTRON
sudo npm install
electron . --no-sandboxIf the Electron versions mismatch
Open package.json and try pinning a compatible Electron version:
"devDependencies": {
"electron": "^10"
}Or try electron11-bin. After changes, always reinstall:
rm -rf node_modules package-lock.json
npm install"Failed to serialise arguments" errors
This is usually an Electron IPC/serialisation mismatch. Try:
- Running with
--no-sandbox. - Downgrading/upgrading Electron (match the repo).
- Updating Node and npm (use
nvmfor easier upgrades. - Reinstalling modules (
rm -rf node_modules package-lock.json && npm install).
If nothing works
- Try it on Windows or macOS (Electron tends to be smoother on these platforms).
- Check the upstream GitHub issues for fixes or patches.
- Run Electron directly with the Electron you installed:
electron .
How to validate findings
Copy XSSTRON's POC.
Reproduce with curl or Burp Repeater.
Ask:
- Is the payload present in the response?
- Is it unescaped in HTML or an attribute?
- Does it execute in the browser context?
If it executes, identify the sink (innerHTML, attribute, eval, etc.).
Classify the bug (reflected, stored, or DOM) and report or fix it (escape output, sanitise input, or use CSP).
