Introduction
Today I'm sharing my first write-up about a Hack The Box lab, where I learned how to exploit a Local File Inclusion (LFI) vulnerability.
Before jumping into the challenge, let's quickly talk about a well-known file in Linux systems: /etc/passwd.
What is /etc/passwd?
It's a system file that exists on almost all Linux distributions. It contains a list of the users registered on the server along with some basic information.
Being able to read this file through a web application is already a critical issue, because it means an attacker can access sensitive information that should never be exposed.
The relation with LFI
The LFI vulnerability allows an attacker to make the server include and display the content of local files that should not normally be accessible from the web application.
In short: LFI = including an existing file on the server and displaying its content in the web page.
Step 1: Lab
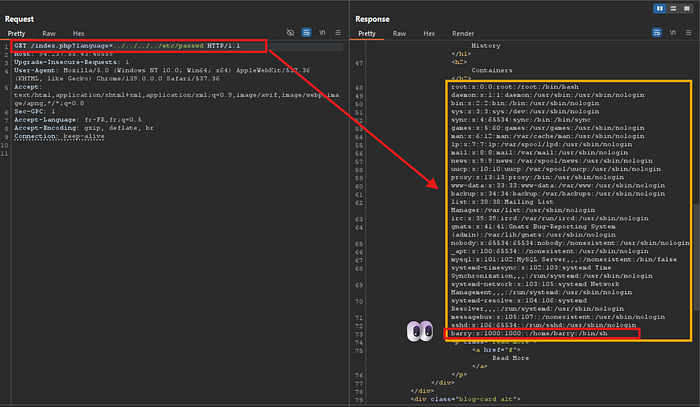
The goal of this lab is to exploit an LFI vulnerability in order to read the sensitive file /etc/passwd and extract a username that starts with the letter "b".

Step 2: Using Burp Suite
To make the process easier, we will use Burp Suite to intercept and modify the requests.
With Burp, we can capture the request sent by the browser, change the value of the parameter (for example language), and then send it again to the server to test for LFI.
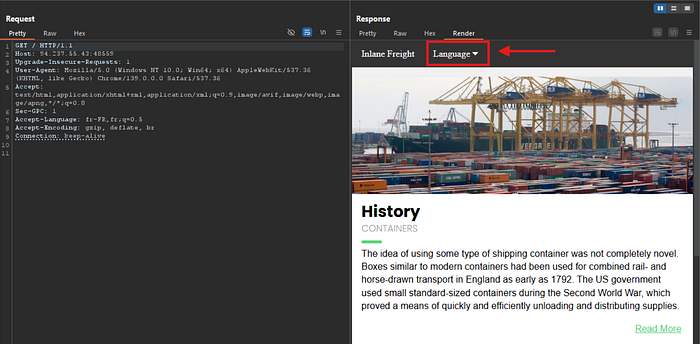
While exploring the application, we notice that it is possible to change the language.
This change is handled through a parameter in the URL (language).
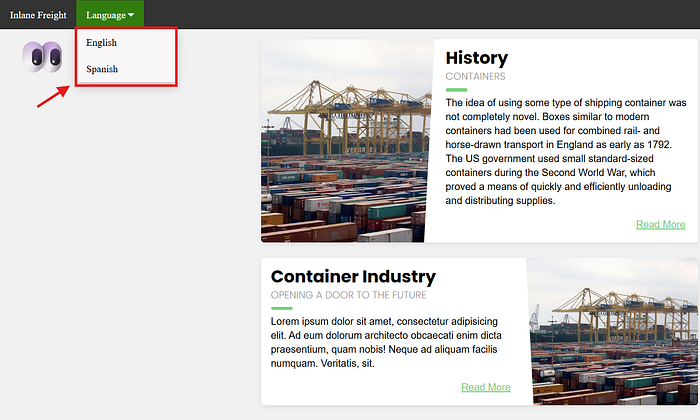
This parameter will be our input for the exploitation, as shown in the screenshot below:
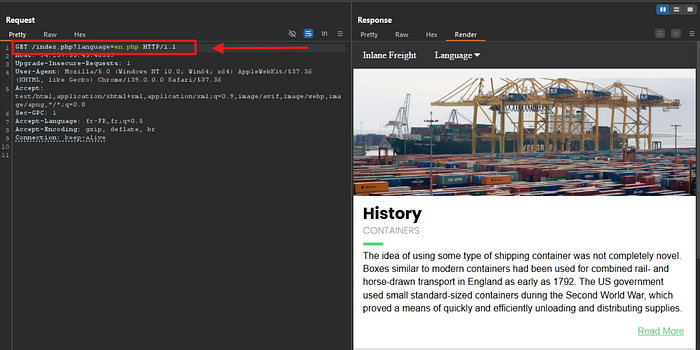
Step 4: Understanding Path Traversal
If we try to read /etc/passwd directly, it doesn't work, because the developer restricted access to files inside the languages/ directory.
To bypass this restriction, we use a technique called Path Traversal.
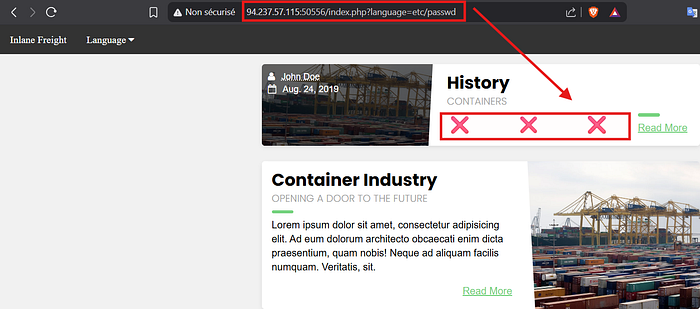
In summary, Path Traversal allows us to move up in the server's directory tree using ../.
Each ../ goes one step back in the folders. For example:
- If we are in
/var/www/html/languages/: ../→ goes to/var/www/html/../../→ goes to/var/www/../../../→ goes to/var/../../../../→ goes to/(the root of the system)
Once we reach the root, we can specify the absolute path of the file we want to read, like /etc/passwd.
Example payload: ../../../../etc/passwd
Conclusion
We took a very simple example to understand the basics of the LFI vulnerability, especially how to access the sensitive /etc/passwd file using the Path Traversal technique.
This exercise clearly shows that a website which does not properly filter user input can be exposed to a critical vulnerability, allowing an attacker to read internal server files.
Risks of LFI
- Reading the application's source code
- Stealing sensitive information
- Executing arbitrary code
Thanks for reading!

