Intro
Wi‑Fi is everywhere — at home, at work, in cafés — and understanding how it works (and how it can be attacked) is essential for anyone who manages networks or cares about privacy. This post explains Wi‑Fi fundamentals, security protocols, common attacks, and practical defensive guidance in a compact, beginner-friendly way. Use this knowledge ethically: test only on networks you own or where you have explicit permission.
What is Wi‑Fi?
Wi‑Fi (Wireless Fidelity) is a wireless networking technology that uses radio waves to transmit data over the air. It's part of the IEEE 802.11 family of wireless standards and operates in unlicensed ISM (Industrial, Scientific, and Medical) frequency bands — 2.4GHz, 5GHz, and 6GHz.
Key Points
- Full Form: Wireless Fidelity
- Technology: Wireless Local Area Network (WLAN)
- Frequencies: 2.4GHz / 5GHz / 6GHz
- Standard: IEEE 802.11
- Purpose: Transmit radio signals as digital data
- ISM Bands: Allow communication devices without a license
ISM = Industrial, Scientific, Medical — refers to the bands available for unlicensed use.
Wi‑Fi Security Protocols
+----------+---------------------------+------+----------------+------------------------+---------------------+---------------------------------------------+-------------+
| Protocol | Stands For | Year | Security Level | Encryption | Key Size | Authentication | Integrity |
+----------+---------------------------+------+----------------+------------------------+---------------------+---------------------------------------------+-------------+
| WEP | Wired Equivalent Privacy | 1997 | Very Low | RC4 (FMS) | 64-bit (40+24 IV) | Open System / Shared Key | CRC-32 |
| WPA | Wi-Fi Protected Access | 2003 | Low | TKIP with RC4 | 128-bit (48 IV) | PSK & 802.1x (EAP) | MIC (64-bit)|
| WPA2 | Wi-Fi Protected Access 2 | 2004 | High | AES-CCMP | 128-bit (48 IV) | PSK & 802.1x (EAP) | CCMP (AES) |
| WPA3 | Wi-Fi Protected Access 3 | 2018 | Very High | AES-CCMP / AES-GCMP | 128-bit / 256-bit | SAE (Simultaneous Authentication of Equals) | SHA-2 |
+----------+---------------------------+------+----------------+------------------------+---------------------+---------------------------------------------+-------------+- WEP is broken (FMS attack — Fluhrer, Mantin & Shamir).
- WPA improved over WEP but TKIP has known weaknesses (MIC exploits).
- WPA2 brought AES‑CCMP (stronger confidentiality & integrity).
- WPA3 adds protections for weak passphrases and open networks.
Important Terms
- Initialization Vector (IV): random value combined with a key to prevent repeating ciphertexts (thwarts simple replay analysis).
- Shared Key Authentication (SKA): WEP-era authentication method (insecure).
- Pre-Shared Key (PSK): passphrase used in WPA/WPA2 Personal.
- Extensible Authentication Protocol (EAP): framework used with 802.1X for enterprise authentication (RADIUS/IAS).
WPA2 — Enhanced Security
WPA2 improved wireless network security by fixing weaknesses in WEP and WPA.
Key Security Enhancements:
- AES encryption (stronger confidentiality).
- Improved key management and rekeying.
- Better authentication (802.1X/EAP).
- Stronger protection against man-in-the-middle attacks.
- Network isolation options (VLANs, guest networks).
Table: Terms
+-------------+---------------------------------------+
| Term | Description |
+-------------+---------------------------------------+
| Wi-Fi Name | ESSID (human readable) |
| Router MAC | BSSID (AP's MAC) |
| Client MAC | Station ID |
| Handshake | Key negotiation (4-way in WPA/WPA2) |
+-------------+---------------------------------------+How Wi‑Fi works
Every Wi‑Fi device has a unique hardware address (MAC).
Typical flow:
- AP broadcasts beacons with SSID & capabilities.
- Client scans and selects SSID.
- Client and AP authenticate & associate.
- 4‑way handshake (WPA/WPA2) derives session keys (PTK/GTK).
- Encrypted data frames are exchanged (IVs used to prevent replay).
Hacking Concept
Hackers can perform deauthentication attacks, where they disconnect devices from a Wi‑Fi network using the router's SSID.
(Only for awareness — do not perform attacks on networks you do not own or have permission to test.)
Wireless Network Services
Wi‑Fi enables flexible, cable‑free connectivity for various wireless network services:
- Voice Over WLAN (VoWLAN) — Voice calls over Wi‑Fi using IP.
- RFID Tracking — Identifies and tracks tagged objects using radio waves.
- Wireless Network Management — Monitors and controls wireless devices remotely.
Wi‑Fi Alternatives
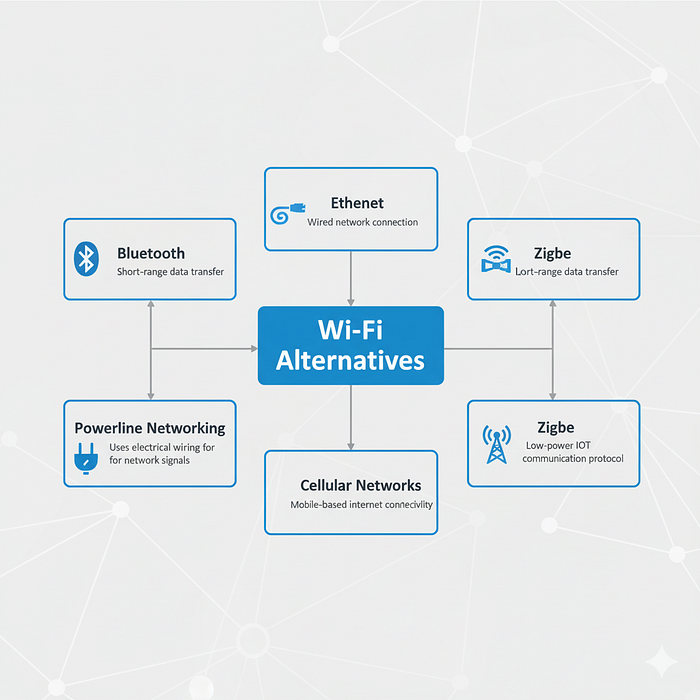
Zigbe Notes:
- Works on small ranges
- Transfers small data packets
- Often preferred for IoT devices
Internet of Things (IoT):
A network of smart, connected devices that collect and exchange data through the internet.
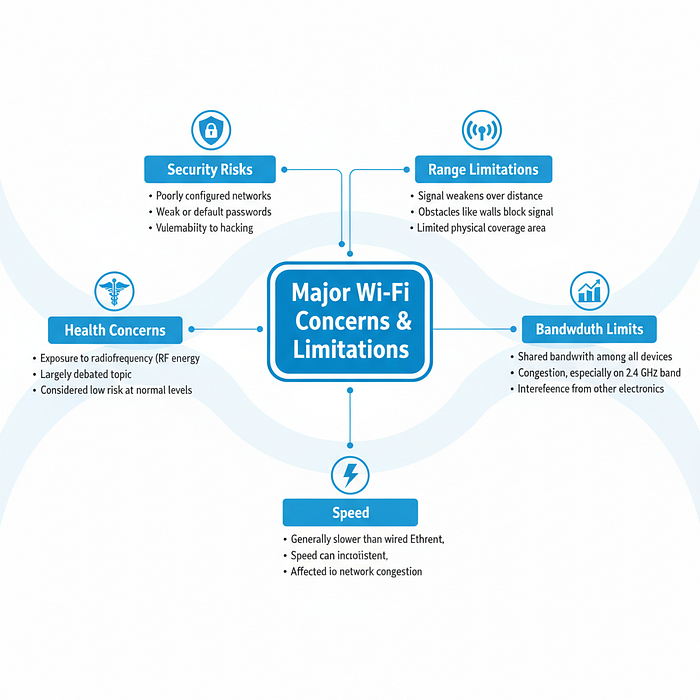
Major Wi‑Fi concerns & limitations
Wi‑Fi threats & hacking methodology
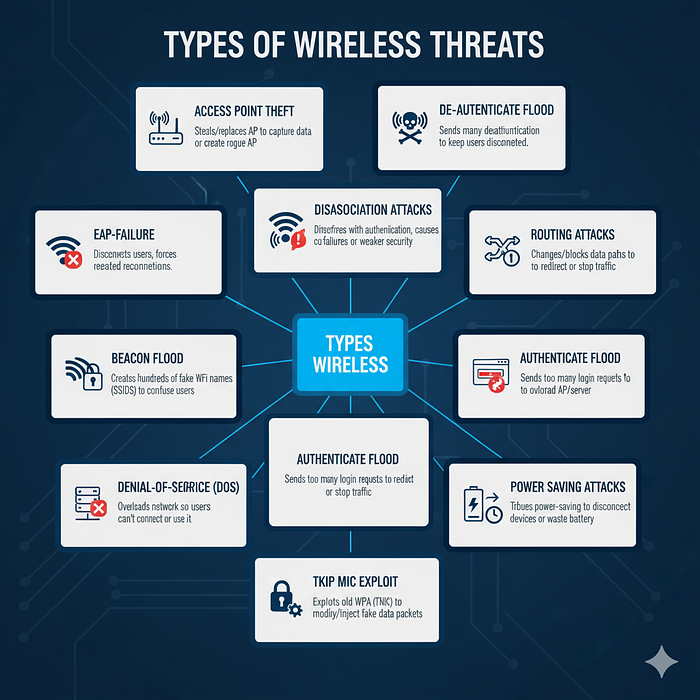
- ARP: maps IP → MAC (frequently targeted for MITM)
- EAP: carries authentication messages between supplicant & auth server
- Beacon flood: attacker broadcasts many fake SSIDs to confuse clients
- TKIP MIC exploit: exploits weaknesses in TKIP's message integrity check
💥 Wireless hacking methodology
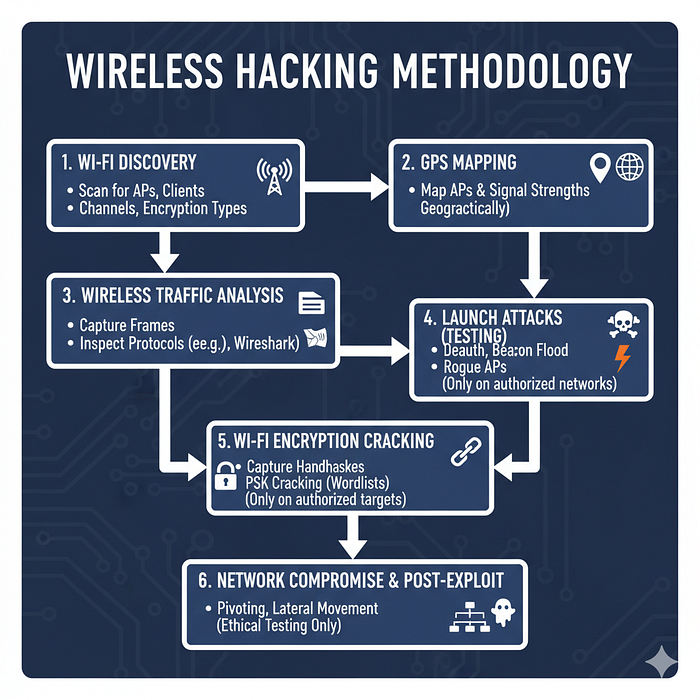
- Wi‑Fi discovery — scan for APs, clients, channels, encryption types
- GPS mapping — map APs and signal strengths geographically
- Wireless traffic analysis — capture frames, inspect protocols (e.g., Wireshark)
- Launch attacks (testing) — deauth, beacon flood, rogue APs (only on test/authorized networks)
- Wi‑Fi encryption cracking — capture handshakes and try PSK cracking with wordlists (only on authorized targets)
- Network compromise & post‑exploit — pivoting, lateral movement (ethical testing only)
Ethical reminder: Use this information responsibly and only on networks you own or are authorised to test.
End of document.