The goal of this project is to develop a powerful, automated reconnaissance script. A well-defined checklist and a robust workflow are the cornerstones of an effective script, ensuring comprehensive coverage and consistent, actionable results.
2. Objectives
- Produce repeatable, high-quality reconnaissance data with minimal manual effort.
- Cover the full surface area defined by scope (DNS, domain, IP ranges, application endpoints, and related assets).
- Normalize outputs so downstream scanners / triage processes can consume them easily.
- Trigger alerts or reports for critical findings and hand off non-critical findings for scheduled review.
3. The Checklist: The Backbone of Reconnaissance
Decide up-front what outputs we want; the checklist drives which tools to run and in what order. Typical checklist items:
Discovery
- DNS records (A, AAAA, CNAME, MX, TXT, NS, SOA) and zone transfers where applicable
- Subdomain enumeration (passive + active)
- Wildcard / typo / permutation discovery (e.g., fuzzing, permutation lists)
- Certificate transparency logs (discovering hostnames from certs)
Host & Network
- Host resolution and IP mapping
- Port scanning and service identification (fast + deep scans depending on scope)
- Cloud metadata endpoints / cloud service discovery (if allowed)
Application & Web
- Directory and file enumeration (wordlists, brute force)
- Endpoint gathering (API endpoints, parameterized routes)
- Robots.txt and sitemap analysis
- TLS/HTTPS configuration and certificate analysis
Content & Code
- Static code analysis (public repos, exposed source, client-side JS analysis)
- Secret detection in files (API keys, tokens)
- Open-source foot printing (GitHub, GitLab, package registries)
Vulnerabilities & Context
- Known CVE lookup for identified software and versions
- Package / dependency disclosure (from public repos or exposed package manifests)
- Common web vulns detection hints (possible SQLi, XSS, LFI endpoints) from passive scanning
Extras / OpSec
- Screenshots of web assets (visual triage)
- Historical snapshot analysis (Wayback / archived content)
- Owner contacts mapping (support, abuse, security contacts)
- False-positive reduction heuristics (rate-limit, caching, fingerprinting)
4. Workflow: Orchestrating the Process
The workflow dictates the sequence of execution, handles dependencies between tools, and manages the output.
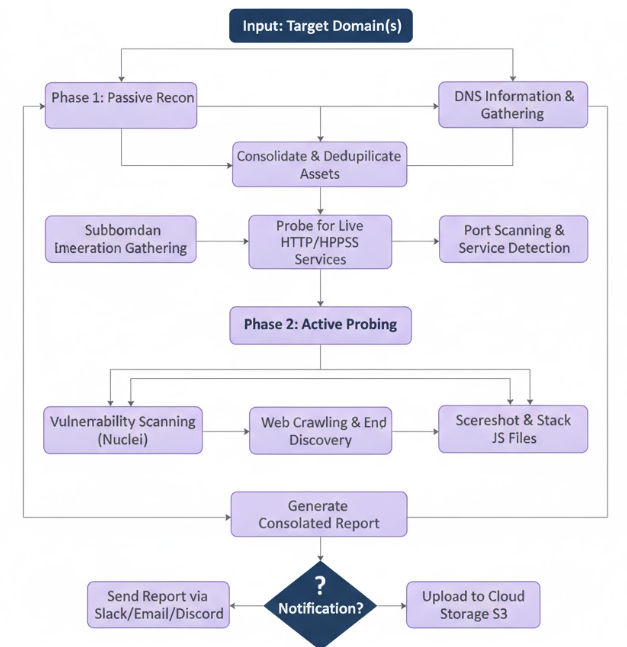
5. Summary
In summary, building a powerful automated recon script is a systematic process of translating a comprehensive methodology into executable code. By defining a rigorous checklist and implementing it through a structured workflow, we can transform raw targets into a prioritized, actionable intelligence report. The final step is closing the loop — ensuring these findings are delivered effectively to drive the next phase of security testing.

