Hello friends,
My name is Sohail and I am a Penetration Tester and also a Bug Bounty Hunter.
I am writing this write-up after a long time. My previous write-ups were useful to many people, so I thought that I should contribute to the community from which I have learned myself.
In this write-up I am going to tell you guys how I was able to perform a subdomain takeover and receive a 4-digit $$ bounty reward.
I will try to keeps things clear and easier for everyone to understand.
My methodology:
Suppose, we are testing "target.com"
- First, I used subfinder to enumerate all the subdomains of target.com.
- After collecting all the subdomains, I manually visited each subdomain and saw what response I was getting.
- One of the subdomain which I visited "assets.target.com" was returing an error which made me curious and I searched for that on google. What was that error message?
Fastly error: unknown domain asset.target.com. Please check that this domain has been added to a service.
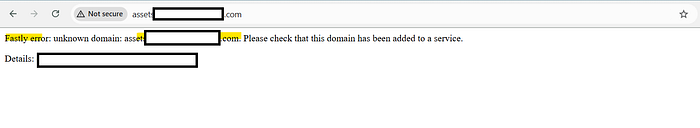
4. I googled this and found out that there is a possibility to takeoever this subdomain.
This was just the enumeration part. Now, we will begin the Exploit/POC part.
After confirming that subdomain takeover is possible, I needed to confirm it by exploiting this vulnerability to show impact.
- I ran the following command: dig assets.target.com CNAME
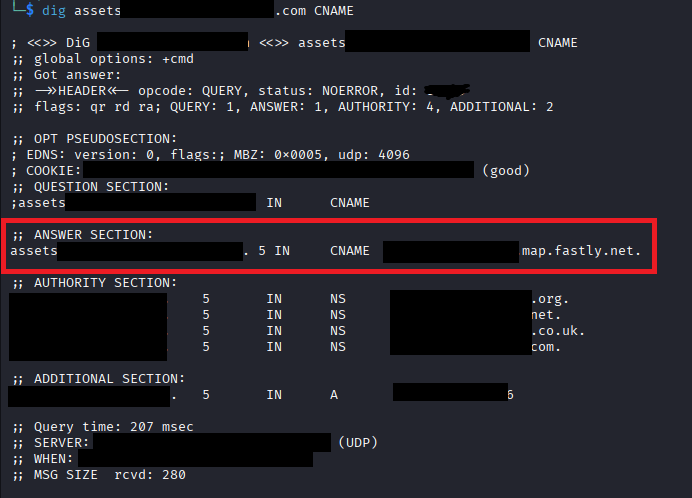
- The command confirmed that the DNS pointed to Fastly.
- Now, I created a Fastly account.
- I created a new CDN Service and added the asset.target.com in the domain field.
- I was expecting to receive the error message that "domain is already taken by another customer" instead I received the following.
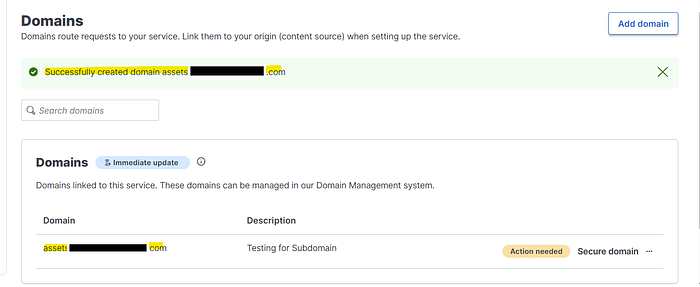
- This was the point where the vulnerability was confirmed.
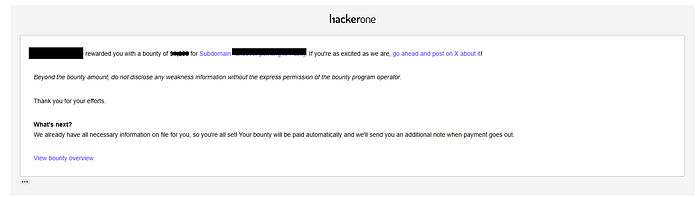
- I reported the vulnerability to the Bounty Program and received a $$$$ Bounty Reward.
I hope that this small write-up will be helpful for the community.
Don't give up just yet!