A supply chain attack is a category of cyberattack that targets an organization indirectly by compromising a less secure element within its network of external partners, suppliers, or vendors. The core principle is exploiting the implicit trust a company places in its third-party providers. By compromising the "link" (a piece of software, hardware, or a single vendor), attackers can gain access to the more heavily defended "target" organization. These attacks are also often referred to as third-party attacks.
SolarWinds (2020): Malicious code injected into a software update for SolarWinds' Orion network management tool, infecting thousands of governments and corporate customers.
MOVEit (2023): Attackers exploited a vulnerability in the widely used MOVEit Transfer file-sharing software, leading to data theft from hundreds of organizations worldwide.
Change Healthcare / UnitedHealth Group Ransomware (February 2024): A major ransomware attack on Change Healthcare (a subsidiary of UnitedHealth Group) disrupted health care systems across the U.S. This is a key example of a third-party compromise causing massive operational disruption and data exposure in critical infrastructure.
XZ Utils Backdoor (April 2024): A sophisticated supply chain attack was discovered targeting the XZ Utils data compression library, which is a component in many major Linux distributions. The attacker had secretly inserted a malicious backdoor into the code over a long period. This was a near-miss that could have led to massive server compromises globally had it not been detected.
Malicious Packages in Open-Source Repositories (Ongoing): Attacks targeting open-source software ecosystems like npm (JavaScript) and PyPI (Python) remain rampant. Threat actors continue to upload malicious packages (sometimes stealing SSH keys or credentials) or hijack abandoned packages to distribute malware, which then gets pulled into thousands of downstream development projects.
Salesloft Drift (August and September 2025) The widespread supply chain attack that targeted the marketing Software-as-a-Service (SaaS) provider Salesloft Drift was publicly disclosed and widely reported on in late August and early September 2025. The core of the attack involved:
- Attackers gaining access to Salesloft's GitHub environment (March–June 2025).
- Pivoting to the Drift's AWS environment and stealing OAuth tokens issued by Drift to its customers' technology integrations, primarily Salesforce.
- Using these stolen tokens between August 8 and August 18, 2025, to access and exfiltrate large volumes of data from hundreds of Salesloft/Drift customers' Salesforce environments, looking for sensitive credentials and customer information.
The incident was described as a supply-chain attack because it leveraged a trusted third-party integration (Drift) to breach the data of over 700 downstream customer organizations.
Why These Attacks Are Dangerous
Supply chain attacks are highly effective and pose a significant threat due to three main factors:
- Massive Scale: Compromising a single widely used vendor (like an IT management tool or a security product) can instantly give an attacker access to hundreds or thousands of downstream customers simultaneously.
- Evasion of Defenses: The malicious payload often bypasses traditional security controls because it appears to be a legitimate, digitally signed update or asset from a trusted source.
- Deep Access: The vendor, by nature of its service, often requires deep, system-level access to its client networks, which the attacker inherits upon successful infiltration.
General Trends and Statistics
- Attack Frequency is Rising: Reports indicate that software supply chain attacks are increasing significantly, with some estimates suggesting the rate has doubled or more in recent months compared to previous long-term averages.
- Open-Source is a Primary Target: The foundation of modern applications, open-source software, is a frequent vector, with the number of malicious packages in repositories growing substantially year-over-year.
- Third-Party Breaches are Common: A significant percentage of all data breaches are now reported to involve a third-party vendor or supply chain compromise, highlighting the risk of an organization's extended network of partners and suppliers.
- High Financial Cost: The average cost of a data breach is escalating, and breaches that originate from a supply chain compromise are often among the most expensive for organizations to identify and contain.
Supply Chain Security: Threat Landscape
Supply chain attacks exploit trust relationships — between software dependencies, hardware vendors, service providers, and internal/third-party components. Key vectors include:
- Malicious or compromised software packages (e.g. npm, PyPI, Maven, etc.).
- Poisoned builds or CI/CD pipelines.
- Compromised vendor credentials (email, access) leading to social engineering.
- Third-party service or library vulnerabilities (e.g. Log4Shell).
- Hardware / firmware tampering.
- Fraud, counterfeiting, document forgery especially in physical supply chains.
How Supply Chain Attacks Work
Instead of launching a costly, direct assault on a primary target (e.g., a major corporation or government agency), attackers follow a multi-step process known as "island hopping":
- Identify a Weak Link (The Victim's Supplier): Attackers look for a third-party vendor (a software company, an IT service provider, or a hardware manufacturer) that has direct, trusted access to the target's systems but maintains weaker security defenses.
- Infect the Trusted Asset (The Malicious Payload): The attacker compromises the supplier's environment. The goal is to secretly insert a malicious component into a product or service the supplier distributes to its customers.
- Software Supply Chain: The most common form involves injecting malicious code into a legitimate software update, an open-source library, or an application installer.
- Hardware Supply Chain: This may involve tampering with physical components, such as installing malicious microchips on circuit boards during manufacturing.
- Distribution and Execution: The supplier unknowingly distributes the compromised product to its clients (the ultimate targets). Because the product is digitally signed and comes from a trusted vendor, the target organization installs or executes the malicious code without suspicion, granting the attacker a covert foothold inside the system.
Framework for Potential Remedial Measures for proactive, detecting and protecting from the Supply Chain attacks:

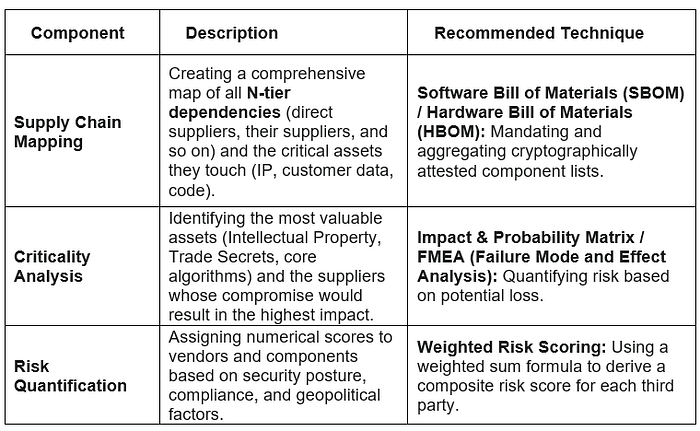
1. Risk Identification and Mapping
The initial phase focuses on gaining complete visibility and mathematically quantifying the risk exposure across all external dependencies.
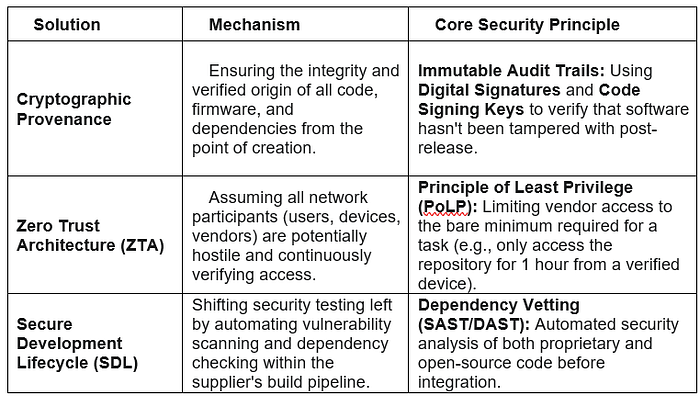
2. Proactive and Preventative Controls (Defense-in-Depth)
This layer implements controls designed to prevent attacks from succeeding in the first place, primarily focusing on third-party access and code integrity.
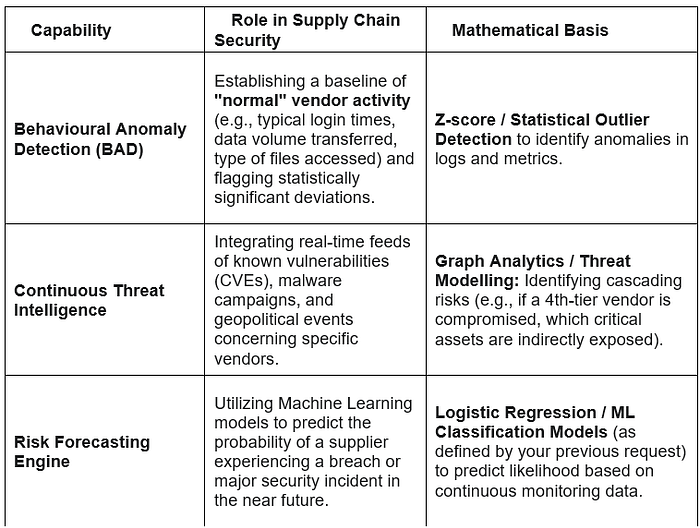
3.Detective and Predictive Monitoring
This layer focuses on actively looking for anomalies, unauthorized behavior, and signs of espionage that indicate a breach is in progress or imminent.
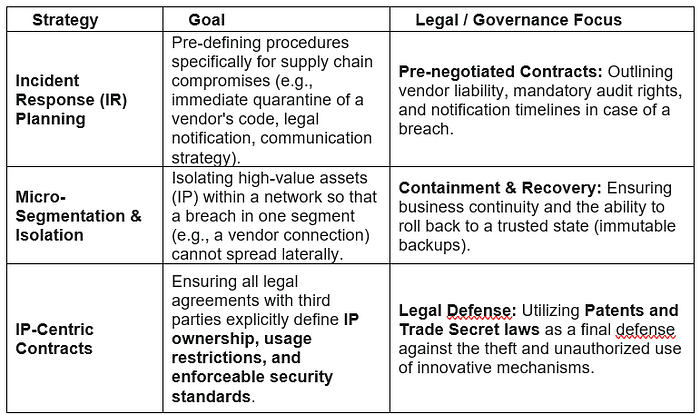
4. Resilient Defense and Governance
The final layer ensures the organization can survive an attack with minimal damage and maintain legal/operational continuity.
Recommended Solutions and Implementation
Effective supply chain security requires a unified strategy spanning Proactive (Preventive), Detective, and Predictive (Forecasting) controls.
· Proactive controls use weighted scoring to prioritize resources against the most critical risks in the supply chain.
· Detective controls use statistical methods (like Z-score) to mathematically define "normal" and flag statistically significant deviations that indicate a potential attack, ensuring high-speed detection.
· Forecasting controls use predictive modeling (like Logistic Regression) to assess the future probability of a threat, allowing for advanced preparation and dynamic resource allocation.
1. Cryptographic and Immutable Provenance
This mechanism ensures the integrity and verified origin of software, hardware, and data components, which is critical for scientific innovations like new AI models.
- Software Bill of Materials (SBOM) and Attestation: Organizations mandate and automatically scan detailed SBOMs from all software/hardware vendors. This list of components is cryptographically signed to attest to its integrity. Continuous monitoring then checks all components against known vulnerabilities, instantly flagging risks to scientific applications.
- Blockchain/DLT for Intellectual Property/IP Traceability: Distributed Ledger Technology (DLT) is used to create a tamper-proof record of ownership, custody transfers, and integrity checks for core IP assets. Any unauthorized access or alteration is immediately flagged and verifiable by all stakeholders.
- Code Signing Keys and Hardware Root of Trust: Utilizing strong cryptographic keys to digitally sign all software updates, code libraries, and firmware. The physical/virtual device executing the innovative mechanism must also contain a Hardware Root of Trust (HRoT) — a secure, tamper-resistant module — to verify the integrity of the boot process and the software's signature before execution.
2. Advanced AI/ML Defense Mechanisms
Instead of just defending data, AI is used to defend the very mechanisms of innovation (e.g., models and algorithms) by detecting subtle pre-attack reconnaissance.
- Behavioral Anomaly Detection (BAD): Advanced ML models establish a baseline of "normal" behavior for scientific workflows, like the typical data volume transferred during a simulation or the specific systems a developer accesses. Any subtle deviation — such as a large, unexpected data transfer from the R&D server to a third-party vendor's network — is instantly flagged as potential IP exfiltration.
- Dynamic Supplier Risk Scoring (DSRS): An AI system continuously collects security rating, news sentiment, and compliance data for all third-party suppliers. It generates a real-time, weighted risk score to proactively guide which suppliers need more stringent access controls or auditing, focusing on those critical to the innovative mechanism's supply chain.
3. Zero Trust and Micro-Segmentation for Isolation
This strategic shift assumes that the network is already compromised, forcing continuous verification of every user, device, and application.
- Principle of Least Privilege (PoLP) Isolation: Access to the most sensitive innovation assets (e.g., the server hosting the genetic sequence data, the cloud repository for the new chip design) is completely isolated using micro-segmentation. Access is granted only with multi-factor authentication, only from verified devices, and only for the exact duration and minimal scope required to perform a specific task.
- Secure Development Lifecycle (SDL) 'Shifting Left': Security is embedded at the earliest design stage of the innovative mechanism, not bolted on later. This includes automated security analysis of code (SAST/DAST) and vetting open-source dependencies before they are integrated into the final scientific application.
4. Strategic and Legal IP Protection
Beyond technology, innovative mechanisms must be protected by robust legal and organizational strategies.
- IP-Centric Contracts and Audits: Contracts with suppliers and partners must explicitly define IP ownership, usage, and liability in the event of a breach. This is backed by mandatory and surprise IP audits of a supplier's facilities and security systems to verify adherence to protective clauses.
- Patent Strategy as Defense: While patents disclose the invention, they serve as a powerful legal defense and a clear warning against infringement, particularly for innovations that rely on an exposed mechanism (e.g., a publicly used process or device).
Code / Tools Stack Suggestions
For real systems, some tools / frameworks to use or integrate:
- Dependency Scanners: e.g. OWASP Dependency-Check, Snyk, WhiteSource (Mend.io), GitHub Dependabot.
- CI/CD Pipeline Integration: integrate checks (signature, audit, anomalous update detection) inside build pipelines (Jenkins, GitLab CI, GitHub Actions).
- Graph / Knowledge Bases: store dependency graph; tools like NetworkX, Neo4j, RabbitGraph or other graph databases.
- Machine Learning Libraries: scikit-learn, TensorFlow, PyTorch, XGBoost / LightGBM etc.
- Immutable Logging / Provenance: blockchains (Hyperledger, Ethereum, private chains), or simpler append-only logs with cryptographic hash chaining.
Conclusion
Innovative supply chain defense now requires analytics-driven, zero-trust approaches that adapt as attackers evolve. Data-driven Zero Trust Architecture), which represents the fusion of the "never trust, always verify" is actionable today — enabling proactive, detective, and forecasting security for organizations determined to meet the threats of 2025 and beyond. Principle of Verify Explicitly, to continuously validate the identity (user and machine) and security posture (device health, vulnerability status) of every entity requesting access to supply chain data or systems. Implement Least Privilege Access, to Grant only the minimum permissions necessary for a task. For suppliers, this means access is limited to the specific data or system needed for a single, time-bound interaction and have Assumed Breach, thinking to Operate under the assumption that a trusted entity (a vendor or an internal system) has already been compromised. This mandates micro-segmentation to contain any breach and prevent lateral movement.
