Hidden Secrets: Advanced Google Dorking on GitHub's raw.githubusercontent.com for Bug Hunters and Security Researchers
Disclaimer: This article is for educational purposes only, aimed at ethical cybersecurity researchers and bug bounty hunters. All activities discussed must be conducted within legal boundaries, such as authorized bug bounty programs. Do not use these techniques for unauthorized access, exploitation, or any illegal activities. Always follow responsible disclosure practices.
Introduction
In the world of cybersecurity, Google dorking (or Google hacking) is a powerful reconnaissance technique for uncovering sensitive information exposed on the web. Many experts teach how to use dorks on github.com to find leaked secrets, API keys, or PII (Personally Identifiable Information) in public repositories. However, what they often overlook is the goldmine hidden in raw.githubusercontent.com — GitHub's raw content endpoint.
Why does this matter? Unlike the main GitHub site, raw.githubusercontent.com serves the unrendered, raw files from repositories. Google's indexing can capture these even if the repo is later made private or deleted, as long as it was public at the time of crawling. This persistence makes it a critical tool for bug hunters spotting misconfigurations, leaked credentials, or data exposures that could qualify for bounties.
In this post, I'll explain the basics, provide advanced dorks categorized by purpose (e.g., PII, API secrets), and show how to customize them for general searches or specific targets. These are inspired by real-world techniques but refined to reduce noise — excluding obvious samples, tests, or contact lists.
Remember: Ethical use is key. Test on your own repos or in-scope bug bounty targets only.
Why raw.githubusercontent.com Over github.com?
- Persistence of Data: If a repo was accidentally made public and then deleted or privatized, its raw files might still be indexed by Google. Searching github.com won't always surface these.
- Direct File Access: Raw endpoints expose configs, dumps, and scripts without the repo's UI clutter, making it easier to find embedded secrets.
- Noise Reduction: By focusing on filetypes and intext keywords, you avoid irrelevant repo descriptions or issues.
- Real-World Impact: Many high-severity bugs (e.g., API key leaks leading to account takeovers) have been found this way. For bug hunters, this can reveal critical vulnerabilities in targets with bounty programs.
A simple example: The general dork site:raw.githubusercontent.com (filetype:env OR filetype:yaml OR filetype:json OR filetype:conf) (intext:"password" OR intext:"api_key") -intext:"sample" -intext:"test" searches for config files with potential credentials, excluding demos. This could uncover hardcoded passwords in .env files.
For a specific target (e.g., "example.com"), modify it to site:raw.githubusercontent.com "example.com" (filetype:env OR filetype:yaml OR filetype:json OR filetype:conf) (intext:"password" OR intext:"api_key") -intext:"sample" -intext:"test". This pulls repos mentioning the domain, but for precision, use the target's GitHub username/org (e.g., via browsing their site or OSINT) like site:raw.githubusercontent.com inurl:"target-org".
To reduce noise further, incorporate path patterns like inurl:/config/ or exclusions like -intext:"phone" -intext:"email" -intext:"contact" to skip benign lists.
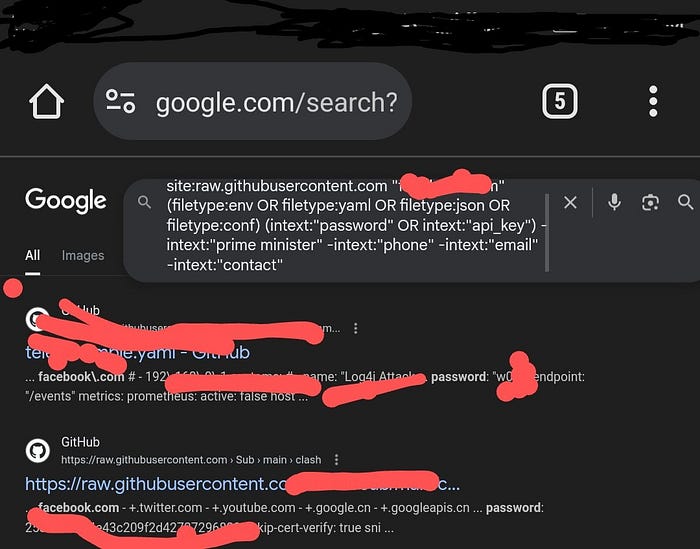
Categorized Google Dorks for raw.githubusercontent.com
Below, I've organized dorks by category. Each includes a general version (no target) and target-specific templates. Replace TARGET with a domain (e.g., "target.com") or GitHub org/username (e.g., "microsoft"). Use inurl:"TARGET" for repo paths, intext:"TARGET" for mentions inside files, or "TARGET" for broad matches.
1. PII (Personally Identifiable Information) Exposure Dorks
These target files leaking emails, names, phones, SSNs, or credit cards. Great for spotting data breaches.
General Dork: site:raw.githubusercontent.com (filetype:csv | filetype:xls | filetype:doc | filetype:docx | filetype:sql) (intext:"email" | intext:"name" | intext:"phone" | intext:"ssn" | intext:"credit card") -intext:"example" -intext:"sample" -intext:"demo" -intext:"test" -intext:"prime minister" -intext:"contact"
Target-Specific Templates: site:raw.githubusercontent.com "TARGET" (filetype:csv | filetype:xls | filetype:doc | filetype:docx | filetype:sql) (intext:"email" | intext:"name" | intext:"phone" | intext:"ssn" | intext:"credit card") -intext:"example" -intext:"sample" -intext:"demo" -intext:"test" -intext:"prime minister" -intext:"contact"
site:raw.githubusercontent.com/TARGET (filetype:csv | filetype:xls | filetype:doc | filetype:docx | filetype:sql) (intext:"email" | intext:"name" | intext:"phone" | intext:"ssn" | intext:"credit card") -intext:"example" -intext:"sample" -intext:"demo" -intext:"test" -intext:"prime minister" -intext:"contact"
site:raw.githubusercontent.com inurl:"TARGET" (filetype:csv | filetype:xls | filetype:doc | filetype:docx | filetype:sql) (intext:"email" | intext:"name" | intext:"phone" | intext:"ssn" | intext:"credit card") -intext:"example" -intext:"sample" -intext:"demo" -intext:"test" -intext:"prime minister" -intext:"contact" site:raw.githubusercontent.com intext:"TARGET" (filetype:csv | filetype:xls | filetype:doc | filetype:docx | filetype:sql) (intext:"email" | intext:"name" | intext:"phone" | intext:"ssn" | intext:"credit card") -intext:"example" -intext:"sample" -intext:"demo" -intext:"test" -intext:"prime minister" -intext:"contact" site:raw.githubusercontent.com inurl:/config/ "TARGET" (filetype:csv | filetype:xls | filetype:doc | filetype:docx | filetype:sql) (intext:"email" | intext:"name" | intext:"phone") -intext:"example" -intext:"sample" -intext:"demo" -intext:"test" -intext:"prime minister" -intext:"contact"
2. API Secrets and Keys Exposure Dorks
Ideal for finding leaked API keys, tokens, or private keys in configs — often bounty-worthy.
General Dork: site:raw.githubusercontent.com (filetype:env | filetype:yaml | filetype:json | filetype:conf | filetype:properties | filetype:pem) (intext:"api_key" | intext:"secret" | intext:"token" | intext:"private_key" | intext:"access_token") -intext:"sample" -intext:"test" -intext:"example" -intext:"demo" -intext:"phone" -intext:"email" -intext:"contact"
Target-Specific Templates: site:raw.githubusercontent.com "TARGET" (filetype:env | filetype:yaml | filetype:json | filetype:conf | filetype:properties | filetype:pem) (intext:"api_key" | intext:"secret" | intext:"token" | intext:"private_key" | intext:"access_token") -intext:"sample" -intext:"test" -intext:"example" -intext:"demo" -intext:"phone" -intext:"email" -intext:"contact"
site:raw.githubusercontent.com/TARGET (filetype:env | filetype:yaml | filetype:json | filetype:conf | filetype:properties | filetype:pem) (intext:"api_key" | intext:"secret" | intext:"token" | intext:"private_key" | intext:"access_token") -intext:"sample" -intext:"test" -intext:"example" -intext:"demo" -intext:"phone" -intext:"email" -intext:"contact" site:raw.githubusercontent.com inurl:"TARGET" (filetype:env | filetype:yaml | filetype:json | filetype:conf | filetype:properties | filetype:pem) (intext:"api_key" | intext:"secret" | intext:"token" | intext:"private_key" | intext:"access_token") -intext:"sample" -intext:"test" -intext:"example" -intext:"demo" -intext:"phone" -intext:"email" -intext:"contact" site:raw.githubusercontent.com intext:"TARGET" (filetype:env | filetype:yaml | filetype:json | filetype:conf | filetype:properties | filetype:pem) (intext:"api_key" | intext:"secret" | intext:"token" | intext:"private_key" | intext:"access_token") -intext:"sample" -intext:"test" -intext:"example" -intext:"demo" -intext:"phone" -intext:"email" -intext:"contact"
site:raw.githubusercontent.com inurl:/config/ "TARGET" (filetype:env | filetype:yaml | filetype:json | filetype:conf) (intext:"api_key" | intext:"access_token") -intext:"sample" -intext:"test" -intext:"example" -intext:"demo" -intext:"phone" -intext:"email" -intext:"contact"
3. Database Dumps and SQL Exposure Dorks
Uncover SQL dumps with user data or DB passwords — perfect for spotting injection risks.
General Dork: site:raw.githubusercontent.com (filetype:sql | filetype:dump) (intext:"INSERT INTO users" | intext:"email" | intext:"password" | intext:"name" | intext:"DB_PASSWORD") -intext:"sample" -intext:"test" -intext:"example" -intext:"demo" -intext:"prime minister" -intext:"phone" -intext:"contact"
Target-Specific Templates: site:raw.githubusercontent.com "TARGET" (filetype:sql | filetype:dump) (intext:"INSERT INTO users" | intext:"email" | intext:"password" | intext:"name" | intext:"DB_PASSWORD") -intext:"sample" -intext:"test" -intext:"example" -intext:"demo" -intext:"prime minister" -intext:"phone" -intext:"contact" site:raw.githubusercontent.com/TARGET (filetype:sql | filetype:dump) (intext:"INSERT INTO users" | intext:"email" | intext:"password" | intext:"name" | intext:"DB_PASSWORD") -intext:"sample" -intext:"test" -intext:"example" -intext:"demo" -intext:"prime minister" -intext:"phone" -intext:"contact" site:raw.githubusercontent.com inurl:"TARGET" (filetype:sql | filetype:dump) (intext:"INSERT INTO users" | intext:"email" | intext:"password" | intext:"name" | intext:"DB_PASSWORD") -intext:"sample" -intext:"test" -intext:"example" -intext:"demo" -intext:"prime minister" -intext:"phone" -intext:"contact"
site:raw.githubusercontent.com intext:"TARGET" (filetype:sql | filetype:dump) (intext:"INSERT INTO users" | intext:"email" | intext:"password" | intext:"name" | intext:"DB_PASSWORD") -intext:"sample" -intext:"test" -intext:"example" -intext:"demo" -intext:"prime minister" -intext:"phone" -intext:"contact" site:raw.githubusercontent.com inurl:/config/ "TARGET" (filetype:sql | filetype:dump) (intext:"password" | intext:"DB_PASSWORD") -intext:"sample" -intext:"test" -intext:"example" -intext:"demo" -intext:"prime minister" -intext:"phone" -intext:"contact"
4. Configuration and Environment File Exposure Dorks
Find leaked configs with passwords or endpoints.
General Dork: site:raw.githubusercontent.com (filetype:env | filetype:yaml | filetype:json | filetype:conf | filetype:properties) (intext:"password" | intext:"secret" | intext:"endpoint" | intext:"config") -intext:"sample" -intext:"test" -intext:"example" -intext:"demo" -intext:"phone" -intext:"email" -intext:"contact"
Target-Specific Templates: site:raw.githubusercontent.com "TARGET" (filetype:env | filetype:yaml | filetype:json | filetype:conf | filetype:properties) (intext:"password" | intext:"secret" | intext:"endpoint" | intext:"config") -intext:"sample" -intext:"test" -intext:"example" -intext:"demo" -intext:"phone" -intext:"email" -intext:"contact"
site:raw.githubusercontent.com/TARGET (filetype:env | filetype:yaml | filetype:json | filetype:conf | filetype:properties) (intext:"password" | intext:"secret" | intext:"endpoint" | intext:"config") -intext:"sample" -intext:"test" -intext:"example" -intext:"demo" -intext:"phone" -intext:"email" -intext:"contact" site:raw.githubusercontent.com inurl:"TARGET" (filetype:env | filetype:yaml | filetype:json | filetype:conf | filetype:properties) (intext:"password" | intext:"secret" | intext:"endpoint" | intext:"config") -intext:"sample" -intext:"test" -intext:"example" -intext:"demo" -intext:"phone" -intext:"email" -intext:"contact" site:raw.githubusercontent.com intext:"TARGET" (filetype:env | filetype:yaml | filetype:json | filetype:conf | filetype:properties) (intext:"password" | intext:"secret" | intext:"endpoint" | intext:"config") -intext:"sample" -intext:"test" -intext:"example" -intext:"demo" -intext:"phone" -intext:"email" -intext:"contact"
site:raw.githubusercontent.com inurl:/config/ "TARGET" (filetype:env | filetype:yaml | filetype:json | filetype:conf) (intext:"password" | intext:"secret") -intext:"sample" -intext:"test" -intext:"example" -intext:"demo" -intext:"phone" -intext:"email" -intext:"contact"
5. AI/ML Model and Tech-Specific Exposure Dorks
Hunt for leaked ML models, keys, or frameworks like TensorFlow.
General Dork: site:raw.githubusercontent.com (filetype:h5 | filetype:pth | filetype:pb | filetype:ipynb) (intext:"model" | intext:"tensor" | intext:"api_key" | intext:"tensorflow" | intext:"pytorch") -intext:"example" -intext:"sample" -intext:"test" -intext:"demo" -intext:"phone" -intext:"email" -intext:"contact"
Target-Specific Templates: site:raw.githubusercontent.com "TARGET" (filetype:h5 | filetype:pth | filetype:pb | filetype:ipynb) (intext:"model" | intext:"tensor" | intext:"api_key" | intext:"tensorflow" | intext:"pytorch") -intext:"example" -intext:"sample" -intext:"test" -intext:"demo" -intext:"phone" -intext:"email" -intext:"contact" site:raw.githubusercontent.com/TARGET (filetype:h5 | filetype:pth | filetype:pb | filetype:ipynb) (intext:"model" | intext:"tensor" | intext:"api_key" | intext:"tensorflow" | intext:"pytorch") -intext:"example" -intext:"sample" -intext:"test" -intext:"demo" -intext:"phone" -intext:"email" -intext:"contact" site:raw.githubusercontent.com inurl:"TARGET" (filetype:h5 | filetype:pth | filetype:pb | filetype:ipynb) (intext:"model" | intext:"tensor" | intext:"api_key" | intext:"tensorflow" | intext:"pytorch") -intext:"example" -intext:"sample" -intext:"test" -intext:"demo" -intext:"phone" -intext:"email" -intext:"contact" site:raw.githubusercontent.com intext:"TARGET" (filetype:h5 | filetype:pth | filetype:pb | filetype:ipynb) (intext:"model" | intext:"tensor" | intext:"api_key" | intext:"tensorflow" | intext:"pytorch") -intext:"example" -intext:"sample" -intext:"test" -intext:"demo" -intext:"phone" -intext:"email" -intext:"contact" site:raw.githubusercontent.com inurl:/config/ "TARGET" (filetype:ipynb | filetype:yaml) (intext:"api_key" | intext:"tensorflow") -intext:"example" -intext:"sample" -intext:"test" -intext:"demo" -intext:"phone" -intext:"email" -intext:"contact"
6. Web3/Crypto Vulnerability Exposure Dorks
Target wallet keys, seed phrases, or smart contracts.
General Dork: site:raw.githubusercontent.com (filetype:js | filetype:json | filetype:sol | filetype:txt) (intext:"privateKey" | intext:"wallet" | intext:"seedPhrase" | intext:"0x" | intext:"pragma solidity") -intext:"test" -intext:"sample" -intext:"example" -intext:"demo" -intext:"prime minister" -intext:"phone" -intext:"contact"
Target-Specific Templates: site:raw.githubusercontent.com "TARGET" (filetype:js | filetype:json | filetype:sol | filetype:txt) (intext:"privateKey" | intext:"wallet" | intext:"seedPhrase" | intext:"0x" | intext:"pragma solidity") -intext:"test" -intext:"sample" -intext:"example" -intext:"demo" -intext:"prime minister" -intext:"phone" -intext:"contact"
site:raw.githubusercontent.com/TARGET (filetype:js | filetype:json | filetype:sol | filetype:txt) (intext:"privateKey" | intext:"wallet" | intext:"seedPhrase" | intext:"0x" | intext:"pragma solidity") -intext:"test" -intext:"sample" -intext:"example" -intext:"demo" -intext:"prime minister" -intext:"phone" -intext:"contact" site:raw.githubusercontent.com inurl:"TARGET" (filetype:js | filetype:json | filetype:sol | filetype:txt) (intext:"privateKey" | intext:"wallet" | intext:"seedPhrase" | intext:"0x" | intext:"pragma solidity") -intext:"test" -intext:"sample" -intext:"example" -intext:"demo" -intext:"prime minister" -intext:"phone" -intext:"contact" site:raw.githubusercontent.com intext:"TARGET" (filetype:js | filetype:json | filetype:sol | filetype:txt) (intext:"privateKey" | intext:"wallet" | intext:"seedPhrase" | intext:"0x" | intext:"pragma solidity") -intext:"test" -intext:"sample" -intext:"example" -intext:"demo" -intext:"prime minister" -intext:"phone" -intext:"contact"
site:raw.githubusercontent.com inurl:/config/ "TARGET" (filetype:json | filetype:sol) (intext:"privateKey" | intext:"0x") -intext:"test" -intext:"sample" -intext:"example" -intext:"demo" -intext:"prime minister" -intext:"phone" -intext:"contact"
7. Zero-Day and CVE-Related Exposure Dorks
Look for logs hinting at vulnerabilities or deprecated code.
General Dork: site:raw.githubusercontent.com (filetype:log | filetype:txt | filetype:php | filetype:js) (intext:"CVE-202" | intext:"vulnerable" | intext:"deprecated" | intext:"exception") -intext:"sample" -intext:"test" -intext:"example" -intext:"demo" -intext:"phone" -intext:"email" -intext:"contact"
Target-Specific Templates: site:raw.githubusercontent.com "TARGET" (filetype:log | filetype:txt | filetype:php | filetype:js) (intext:"CVE-202" | intext:"vulnerable" | intext:"deprecated" | intext:"exception") -intext:"sample" -intext:"test" -intext:"example" -intext:"demo" -intext:"phone" -intext:"email" -intext:"contact" site:raw.githubusercontent.com/TARGET (filetype:log | filetype:txt | filetype:php | filetype:js) (intext:"CVE-202" | intext:"vulnerable" | intext:"deprecated" | intext:"exception") -intext:"sample" -intext:"test" -intext:"example" -intext:"demo" -intext:"phone" -intext:"email" -intext:"contact"
site:raw.githubusercontent.com inurl:"TARGET" (filetype:log | filetype:txt | filetype:php | filetype:js) (intext:"CVE-202" | intext:"vulnerable" | intext:"deprecated" | intext:"exception") -intext:"sample" -intext:"test" -intext:"example" -intext:"demo" -intext:"phone" -intext:"email" -intext:"contact"
site:raw.githubusercontent.com intext:"TARGET" (filetype:log | filetype:txt | filetype:php | filetype:js) (intext:"CVE-202" | intext:"vulnerable" | intext:"deprecated" | intext:"exception") -intext:"sample" -intext:"test" -intext:"example" -intext:"demo" -intext:"phone" -intext:"email" -intext:"contact" site:raw.githubusercontent.com inurl:/config/ "TARGET" (filetype:log | filetype:txt) (intext:"vulnerable" | intext:"deprecated") -intext:"sample" -intext:"test" -intext:"example" -intext:"demo" -intext:"phone" -intext:"email" -intext:"contact"
8. Directory and Backup Exposure Dorks
Expose hidden directories, backups, or .git files.
General Dork: site:raw.githubusercontent.com intitle:"index of" (env | .git | .svn | backup | db.sql | .bak | config | secrets | uploads) -intext:"sample" -intext:"test" -intext:"example" -intext:"demo" -intext:"prime minister" -intext:"phone" -intext:"contact"
Target-Specific Templates: site:raw.githubusercontent.com "TARGET" intitle:"index of" (env | .git | .svn | backup | db.sql | .bak | config | secrets | uploads) -intext:"sample" -intext:"test" -intext:"example" -intext:"demo" -intext:"prime minister" -intext:"phone" -intext:"contact"
site:raw.githubusercontent.com/TARGET intitle:"index of" (env | .git | .svn | backup | db.sql | .bak | config | secrets | uploads) -intext:"sample" -intext:"test" -intext:"example" -intext:"demo" -intext:"prime minister" -intext:"phone" -intext:"contact"
site:raw.githubusercontent.com inurl:"TARGET" intitle:"index of" (env | .git | .svn | backup | db.sql | .bak | config | secrets | uploads) -intext:"sample" -intext:"test" -intext:"example" -intext:"demo" -intext:"prime minister" -intext:"phone" -intext:"contact"
site:raw.githubusercontent.com intext:"TARGET" intitle:"index of" (env | .git | .svn | backup | db.sql | .bak | config | secrets | uploads) -intext:"sample" -intext:"test" -intext:"example" -intext:"demo" -intext:"prime minister" -intext:"phone" -intext:"contact" site:raw.githubusercontent.com inurl:/config/ "TARGET" intitle:"index of" (env | config | secrets) -intext:"sample" -intext:"test" -intext:"example" -intext:"demo" -intext:"prime minister" -intext:"phone" -intext:"contact"
9. Compliance and Regulatory Document Leaks Dorks
Find docs mentioning GDPR, HIPAA, or leaks.
General Dork: site:raw.githubusercontent.com (filetype:pdf | filetype:doc | filetype:xls) (intext:"GDPR" | intext:"HIPAA" | intext:"PII" | intext:"personal data" | intext:"violation" | intext:"leak") -intext:"sample" -intext:"test" -intext:"example" -intext:"demo" -intext:"prime minister" -intext:"phone" -intext:"contact"
Target-Specific Templates: site:raw.githubusercontent.com "TARGET" (filetype:pdf | filetype:doc | filetype:xls) (intext:"GDPR" | intext:"HIPAA" | intext:"PII" | intext:"personal data" | intext:"violation" | intext:"leak") -intext:"sample" -intext:"test" -intext:"example" -intext:"demo" -intext:"prime minister" -intext:"phone" -intext:"contact"
site:raw.githubusercontent.com/TARGET (filetype:pdf | filetype:doc | filetype:xls) (intext:"GDPR" | intext:"HIPAA" | intext:"PII" | intext:"personal data" | intext:"violation" | intext:"leak") -intext:"sample" -intext:"test" -intext:"example" -intext:"demo" -intext:"prime minister" -intext:"phone" -intext:"contact" site:raw.githubusercontent.com inurl:"TARGET" (filetype:pdf | filetype:doc | filetype:xls) (intext:"GDPR" | intext:"HIPAA" | intext:"PII" | intext:"personal data" | intext:"violation" | intext:"leak") -intext:"sample" -intext:"test" -intext:"example" -intext:"demo" -intext:"prime minister" -intext:"phone" -intext:"contact" site:raw.githubusercontent.com intext:"TARGET" (filetype:pdf | filetype:doc | filetype:xls) (intext:"GDPR" | intext:"HIPAA" | intext:"PII" | intext:"personal data" | intext:"violation" | intext:"leak") -intext:"sample" -intext:"test" -intext:"example" -intext:"demo" -intext:"prime minister" -intext:"phone" -intext:"contact"
site:raw.githubusercontent.com inurl:/config/ "TARGET" (filetype:doc | filetype:xls) (intext:"PII" | intext:"violation") -intext:"sample" -intext:"test" -intext:"example" -intext:"demo" -intext:"prime minister" -intext:"phone" -intext:"contact"
10. Exploit Chain and Error Exposure Dorks
Reveal error logs for RCE, injections, or deprecations.
General Dork: site:raw.githubusercontent.com (filetype:log | filetype:txt) (inurl:"/api/" | inurl:"/debug/" | inurl:"/trace/") (intext:"error" | intext:"500" | intext:"RCE" | intext:"injection" | intext:"deprecated") -intext:"sample" -intext:"test" -intext:"example" -intext:"demo" -intext:"phone" -intext:"email" -intext:"contact"
Target-Specific Templates: site:raw.githubusercontent.com "TARGET" (filetype:log | filetype:txt) (inurl:"/api/" | inurl:"/debug/" | inurl:"/trace/") (intext:"error" | intext:"500" | intext:"RCE" | intext:"injection" | intext:"deprecated") -intext:"sample" -intext:"test" -intext:"example" -intext:"demo" -intext:"phone" -intext:"email" -intext:"contact" site:raw.githubusercontent.com/TARGET (filetype:log | filetype:txt) (inurl:"/api/" | inurl:"/debug/" | inurl:"/trace/") (intext:"error" | intext:"500" | intext:"RCE" | intext:"injection" | intext:"deprecated") -intext:"sample" -intext:"test" -intext:"example" -intext:"demo" -intext:"phone" -intext:"email" -intext:"contact" site:raw.githubusercontent.com inurl:"TARGET" (filetype:log | filetype:txt) (inurl:"/api/" | inurl:"/debug/" | inurl:"/trace/") (intext:"error" | intext:"500" | intext:"RCE" | intext:"injection" | intext:"deprecated") -intext:"sample" -intext:"test" -intext:"example" -intext:"demo" -intext:"phone" -intext:"email" -intext:"contact"
site:raw.githubusercontent.com intext:"TARGET" (filetype:log | filetype:txt) (inurl:"/api/" | inurl:"/debug/" | inurl:"/trace/") (intext:"error" | intext:"500" | intext:"RCE" | intext:"injection" | intext:"deprecated") -intext:"sample" -intext:"test" -intext:"example" -intext:"demo" -intext:"phone" -intext:"email" -intext:"contact" site:raw.githubusercontent.com inurl:/config/ "TARGET" (filetype:log | filetype:txt) (intext:"error" | intext:"injection") -intext:"sample" -intext:"test" -intext:"example" -intext:"demo" -intext:"phone" -intext:"email" -intext:"contact"
Tips for Customization and Best Practices
- Reducing Noise: Add more exclusions like -intext:"fake" or limit to recent years with &tbs=cdr:1,cd_min:1/1/2023.
- Finding Target GitHub Orgs: Browse the target's website for GitHub links or use OSINT tools to identify their org name.
- Automation: Use tools like googler or scripts to run dorks in batches, but respect Google's terms.
- Ethical Reporting: If you find a leak, report it via the target's bug bounty program (e.g., on HackerOne). Never exploit.
- Legal Note: Google dorking is passive recon, but verify scope. In 2025, platforms like GitHub have improved secret scanning, but leaks still happen.
Conclusion
raw.githubusercontent.com dorking fills a gap in traditional GitHub hunting, offering persistent access to exposed data. As a bug hunter, customize these dorks to your targets and always prioritize ethics. Share your findings responsibly to make the web safer.
If you have refinements or success stories (anonymized, of course), drop them in the comments!
Thanks for reading! Follow for more cybersecurity write-ups.
Abba Abdullahi Wakili is a security researcher, OSINT expert, and malware analyst who conducts defensive research and responsible disclosure. He is the founder of Netclouts and works to build accessible cybersecurity training and tools that protect communities and organizations.
- Google Dorking
- GitHub Security
- Bug Bounty
- OSINT
- Ethical Hacking
Cybersecurity Infosec Hacking Penetration Testing Vulnerability Hunting Reconnaissance Web Security Hacker Security Research Dorking google hacking

