TOPICS
- What Is OSINT?
- What is Targeting?
- OSINT Mindset vs Targeter Mindset
- The Internet of Things
- The Internet of Bodies
- Researching IoB Devices for Targeting
What is OSINT?
OSINT (Open Source Intelligence) is the intelligence tradecraft of gathering publicly or commercially obtainable information and turning it, through analysis, into actionable insights that answer defined intelligence priorities, fills knowledge gaps, or meets specific requirements.
What is intelligence? Intelligence is the structured approach of critically evaluating information to reduce uncertainty and bias, distilling those insights into predictive assessments that clarify choices and forecast the most likely outcome.
What is Targeting?
Targeting is the intelligence driven, legally governed process of identifying, prioritizing, and characterizing specific actors, networks, infrastructure, and vulnerabilities, then converting policy or operational objectives into taskable requirements that enable precise effects, collection, recruitment, access, influence, disruption, or (where authorized) force, through all-source analysis, collateral/risk review, and continuous assessment to refine outcomes.
Example

The target is "Yumi," a Japanese diplomat stationed at the UN, with the ability to directly impact trade-negotiations which makes her an adequate target to fulfill intelligence requirements. Assemble a baseline, passport and company-registry information, travel manifests, meeting schedules, and social-media messages, which capture she visits the Midtown "Blue Sakura" café daily at 07:30AM before work.
One then uses satellite imagery and feeds from city cameras to validate that Yumi indeed takes this path during the next three weeks. One then uses open-source data from LinkedIn to map out her professional networks, discovering a retired university classmate now working at a think tank which has friendly relations to the United States. A targeting team then synchronizes with the HUMINT(Human Intelligence) collectors to set up a chance meeting with Yumi at the café, vetted to ensure diplomatic immunity considerations and third-party exposure to a minimum. Analysts maintain a living target folder keeping Yumi's schedule deviations current, newly emerged vulnerabilities (e.g., an upcoming panel on which she'll moderate), and red-line limitations, so decision-makers can continuously assess whether, when, and how to engage with minimizing operational security and political fallout.
Learning Resources
OSINT Mindset vs Targeter Mindset
Finding, validating, and quantifying publicly and commercially available information while searching for patterns and trends that can be confirmed across open sources is how an open source intelligence analyst goes about meeting intelligence requirements. Their mostly self contained and systematic workflow consists of checklists, databases, and meticulous documentation, which lowers the chance of personal risk while ensuring transparency and repeatability of sourced information.
Targeters on the other hand to support planned operations, have a 360 degree view of a particular individual, geographical location, or building. Because the assessments that targeters conduct have a direct impact on teams in the field to a degree that osint analyst will not be directly faced with, targeting analysts must consider vulnerabilities, collateral, and downstream repercussions while making use of classified, HUMINT, SIGINT, and technical documentation in addition to OSINT. As a result, targeting is by its very nature cooperative and risk-aware, striking a balance between the mission's overall safety and comprehensive intelligence.
The Internet of Things
The Internet of Things commonly abbreviated as (IoT) is a digital network of interconnected physical objects, such as devices, vehicles, appliances, and sensors, that communicate and exchange data over the internet. These devices have sensors and specific software components that allow individuals to interact with them or interact with their surrounding environment, often without the need for direct human intervention.
Some examples of these devices include thermostats for homes and offices, human wearable fitness trackers, house appliances such as toasters and refrigerators , industrial sensors, and urban infrastructure such as smart traffic lights. The goal of the internet of things is to enhance the efficiency and functionality of everyday life. This is done by automating daily processes and provide insights that humans can use for data analysis.
The rapid development of the internet of things has significantly impacted sectors such as healthcare, agriculture, and transportation. IoT is changing the way healthcare is performed as doctors and nurses now have devices and remote monitoring systems to monitor patient health in real time. In agriculture, sensors track the moisture of soil and the conditions in which the crops are grown, supporting data driven farming practices. Despite these advancements in technology IoT devices introduces critical challenges related to data privacy and security, as large volumes of sensitive information are generated and exchanged.
The Internet of Bodies
Wireless technology integrated with the human body is no longer science fiction and is an everyday reality as of 2025. Devices that physically integrate with the human body such as heart rate monitors, ingested personalized pills or sleep trackers are a small example of a larger interconnected ecosystem of IoT devices known as the "internet of bodies" (IoB). This ecosystem includes IoT devices that collect personalized health data or has the ability to alter specific bodily functions. In healthcare, IoB technologies, enable real time monitoring and highly personalized treatments, which is rapidly changing the way in which medical care is performed.
Yet, what cannot be overlooked is that the IoB presents serious privacy and security concerns. Sensitive data can be exposed due to vulnerabilities present in software and hardware, making these devices open to cyberattacks. There have been past incidents, such as soldiers' fitness trackers revealing the locations of military bases, highlight these dangers. As IoB technology becomes more accepted by the general populace, policymakers should prioritize safety and keeping pace with technological advancements. Only by taking these proactive steps can we realize the benefits of IoB while ensuring privacy, security, and autonomy in this rapidly evolving landscape.
Researching IoB Devices for Targeting
Society is gradually shifting towards a dystopian cyberpunk landscape envisioned in Blade Runner, where the lines between what is human and what is machine are increasingly blurred. The Internet of Bodies emerges as both a technological marvel and an opportunity for extensive personalized intelligence collection. The RAND Corporation, which coined the term "Internet of Bodies" in their research , envisioned a future where connected devices would monitor, alter, and integrate with human biological functions.
Today as of 2025, this vision has somewhat materialized into an expansive ecosystem of IoT devices, such as continuous glucose monitors, smart hearing aids, and even ingestible sensors that collect intimate and sensitive biometric data on patients for medical practitioners to analyze and make decisions. For the open source analyst or targeter, this represents an unprecedented sea of exploitable information, a digital categorical index of human activity and physiological states, and behavioral analytics which can be systematically harvested over long periods of time and analyzed to meet intelligence requirements as outlined by policy and decision makers.
The targeting methodology for IoB devices requires a sophisticated multi platform approach and somewhat of understanding of networking principles like IP address ranges/SIDR and networking terminology. This allows targeters to leverage internet of things search engines that go beyond the traditional scope of open source intelligence. Shodan remains at least somewhat my primary reconnaissance platform for IoB related devices and websites, using queries like "fitness tracker", "heart rate monitor", and tag:medical to identify exposed wearable devices and their associated infrastructure.
However, advanced targeters increasingly employ FOFA (Foresee & Find it All) for its superior fingerprinting capabilities and faster vulnerability detection. The infamous Strava incident exemplifies the advantage that targeting analysts can have when conducting planning on targets, picture the scenario where you take an open sourced photo of a politician or diplomat and notice that they are wearing a fitness tracker, you can potentially exploit this vulnerability depending on the manufacturer and perhaps track them down to their exact location, or map out an SDR (Surveillance Detection Route).
This has already occurred because military personnel's fitness data has inadvertently exposed patrol routes, base perimeters, and operational patterns across sensitive locations in Israel, Afghanistan, and Somalia. Modern targeting leverages this same methodology, correlating fitness tracker heat maps with geospatial intelligence, identifying patterns of life through exercise routines, and building comprehensive target profiles from aggregated biometric data. Professional targeters also now have the ability to employ automated web scraping tools to harvest vast amounts of data from multiple IoB platforms simultaneously and analyze that for their intended target by cross-referencing fitness tracker locations with social media check-ins, medical device serial numbers with hospital databases in the event you have access or it's been leaked somewhere on the DarkNet, and wearable device MAC addresses with network traffic analysis.
My Findings
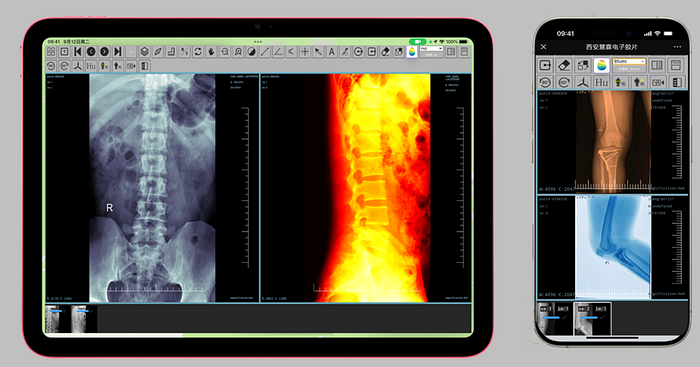
"DICOM Server Response" port:104 country:CN -authentication
"medical" vuln:CVE-2020-25175
port:445 http.title:"patient"