Whispers of the Dev-Server: The Journey of a Bug Hunter Discovering CVE‑2025‑30208 on the Government Portal.
Hello hackers, my handle is Will.Star. I'm a security researcher and bug bounty hunter who loves finding real‑world vulnerabilities. I found my target during a social engineering/networking trip.
1. The hunt begins
I started with a series of light checks: inspecting public headers, looking at robots.txt, checking for a sitemap if one existed, and noting subdomains. This was non‑intrusive reconnaissance — no force, no exploitation. After hours of probing, I paused on a particular subdomain and a closer inspection revealed that the site was built with Vite.
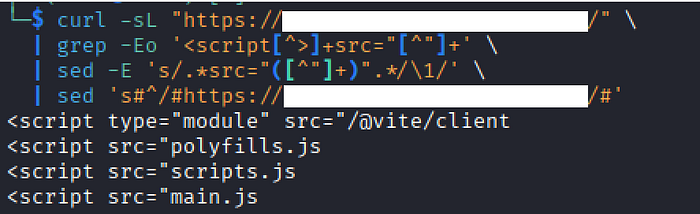
I immediately ran dirsearch to look for hidden directories. I also checked the site's /main.js file. It proved very useful for deeper discovery.
I found some important points in it like: * The app is SPA Angular, calling API on https://xxxx.xxxx.xxx.xxx (saved in environment.baseUrl). * The JWT token is saved in localStorage under key token-pladiermo, there is a validateToken function that decodes the payload part with atob(token.split('.')[1]) and compares exp to determine the operation; if active, the client will call more API to set user/menu/visit and save more data to localStorage. * Login calls endpoint /identidad/auth/login (login POST) and the token is saved after receiving data.data.token. There is a password recovery + password change page on client side. * Many client-side services build explicit RESTful routes (e.g. users: environment.baseUrl + environment.identidad + environment.users with endpoints like /table?active=&page=&size=, /${id}, create, ?id= for update/delete, getMenu(userId) etc.). These API paths are heavily "formatted" and predictable.
2. The harsh truth
I spent some time learning about Vite to be able to exploit it, we need to understand it.
********************************************************************* Vite is one of the most popular front-end development tools, supporting thousands of React, Vue and other modern JavaScript projects.
After a period of research and continuous efforts to penetrate, I discovered the vulnerability CVE 2025–30208 existing in the government website system.
CVE 2025–30208 Publication Date: March 25, 2025 Severity Level: HIGH CNA Score: 5.3
3. Technical details
If you tweak the URL properly, you can bypass these restrictions. By adding "raw" or "import&raw" to the file request URL, you will *bypass* the allowlist and get the raw contents of any file, as long as you know the path and that the file exists. Let's assume a public Vite development server application. In most setups, requesting a sensitive file like /etc/passwd (Linux) or a configuration file outside the project root directory will be rejected:
GET /@fs/etc/passwd --> 403 ForbiddenBut with the "skip" trick, everything changes.
GET /@fs/etc/passwd?raw?? --> 200 OKor
GET /@fs/etc/passwd?import&raw?? --> 200 OKAnd surprisingly, I successfully exploited a website belonging to the government of a state XXX. This surprised me, because they do not regularly upgrade or secure their systems.

I immediately reported it to their national cybersecurity incident response team. And got a response in less than 8 hours (from the time of reporting).
4. Minimize the risk
Patch Immediately! If you are running an older version, upgrade now.
npm install vite@latest
# or for a specific branch
npm install vite@6.2.3If you must use Vite on an older version (not recommended), never leave the dev server connected to the internet. Run on localhost only for development.