Modern substations, energy grids, and industrial automation platforms all rely on one quiet, aging protocol to keep things running: Manufacturing Message Specification (MMS).
You'll find MMS deep in the heart of IEC 61850, powering communications in substations, SCADA systems, and DCS platforms.
But here's the dangerous part:
MMS was never built with cybersecurity in mind.
And attackers are taking full advantage.

🧠 What Is MMS and Why Does It Matter?
MMS is a protocol used to:
- Exchange real-time data, control commands, and device diagnostics
- Communicate between Intelligent Electronic Devices (IEDs)
- Operate across utility, electrical, and automation sectors
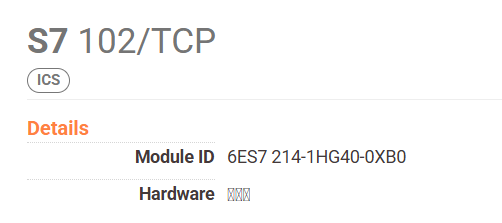
- Run over TCP port 102
- Serve as a foundational piece of the IEC 61850 standard
If you're operating in energy, power distribution, or industrial automation, there's a strong chance MMS is running somewhere in your environment.
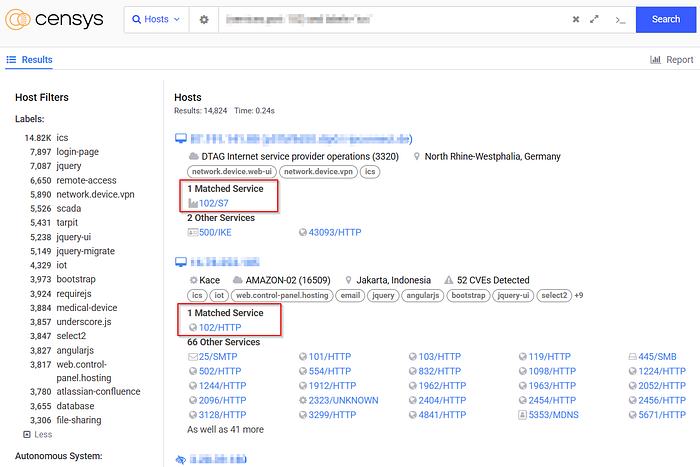
🚨 The Security Problem with MMS
Despite its critical role in industrial control systems (ICS), MMS has zero native security features.
Here's what that means in practice:
❌ No encryption ❌ No authentication 📡 All data and commands are sent in plaintext 🕵️ Susceptible to spoofing and Man-in-the-Middle (MitM) attacks 💥 Open to Denial of Service (DoS) and disruption of critical infrastructure
These aren't just theoretical risks. Threat actors are already exploiting these vulnerabilities in the wild.
🌍 What the Data Shows (Censys Research)
Using Censys, I identified:
- 🔎 15,000+ internet-exposed MMS-enabled endpoints
- 📍 Majority located in Japan and the United States
- ⚠️ Over 6,500 tied to known exploited vulnerabilities (CVE-mapped)
This means a significant portion of critical infrastructure is sitting wide open — accessible to anyone with a scanner and bad intentions.
🛡 How to Secure MMS Today
MMS may be insecure by design — but that doesn't mean you're powerless. Here's how to reduce your risk:
- Keep MMS traffic inside the OT network ➤ Airgap where possible and segregate it from IT networks.
- Block all external access to TCP port 102 ➤ If it's reachable from the internet, you're already at risk.
- Deploy IEC 61850-aware firewalls & Deep Packet Inspection (DPI) ➤ Generic firewalls won't cut it.
- Use Zeek, Snort, or Suricata to monitor MMS traffic ➤ Behavioral anomalies often precede active compromise.
- Enforce VPN + MFA for any remote access ➤ Reduce the risk of credential stuffing or session hijacking.
- Follow industrial standards like IEC 62443 and NIST 800–82 ➤ These frameworks provide baseline controls for ICS/OT environments.
⚡ TL; DR — MMS: Critical but Exposed
MMS is a legacy protocol designed for availability, not security.
But it's still core to how we operate substations, control electrical systems, and manage industrial automation.
If you're using it — protect it like your grid depends on it.
Because it absolutely does.
💬 Let's Talk
Are you seeing MMS in your environment? Ever audited port 102 exposure? Drop your thoughts or questions in the comments — I'd love to hear from folks in the field.
🛠️ Stay safe. Stay patched. Stay curious. Support Palestine.
This research part of oaps_another_attack_surface series, another interesting blog about industrial exposed: MMS And you found me LinkedIn