Hello everyone! I hope you're doing well. How about we take a little break from the wonderful Hack The Box and dive into Google Dorks — our way?
🐾 Before we start: Google Dorks are amazing for learning and research, but always use them ethically. Hack to learn, hack to protect, not to harm.
It's truly a powerful tool, especially if website evaluation for bug bounty is your thing. For this article, all examples will be done manually. I know we have automated tools, but as I've always said: first, let's learn what it's all about, understand how it works, and then we can take that next step.
In short, Google Dorks is all about using the Google search engine to perform searches and gather information from websites that you wouldn't get through a regular query.
But to understand it better, let's jump straight into action. We'll start with a simple query on the site vulnweb.com.
😸 Open your Google Chrome browser, go to the Google homepage, and in the search bar type the following:
site:vulnweb.com
This simple query does nothing more than ask Google:
"Hey, give me all the results that belong only to the vulnweb.com domain, please."
As a result, Google will return all the indexed pages of that domain, including its subdomains.
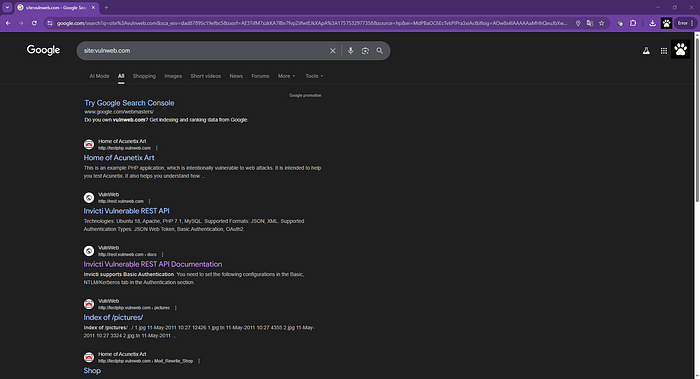
If you're performing a passive reconnaissance process, Google Dorks becomes an indispensable tool. Let me tell you — using it, you can see and evaluate all the information exposed on a domain. This can help you determine what shouldn't be exposed and what might put you, as the site owner, or your client, friend, etc., at risk.In the end, it's a hacking tool that we're going to use to our advantage.
Let's do a more precise search, like peeking into a little corner. Oh, and I forgot to mention — vulnweb.com is made so we can safely experiment with all kinds of hacking exercises during lessons. Think of it like a practice shooting range, but for hacking!

With that clarified, let's continue.
😸 Let's type the following in the search bar:
site:vulnweb.com filetype:txt
What are we asking for? Well, we're basically telling Google:
"Hey, bring me only from the vulnweb site all the files that are of type 'txt' "
The result would look like this:
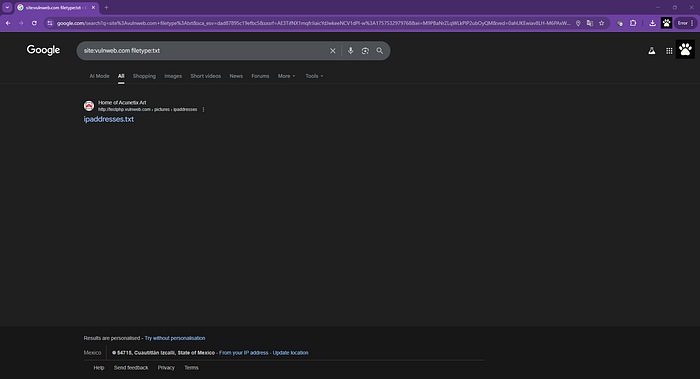
Interesting, right? Just imagine if someone accidentally leaves a document exposed with usernames and emails. You might think it doesn't happen, but I've already handled a case like this.
Now you know the basics of Google Dorks. The tricky part is the findings, because those are exactly what can affect a company. If you discover something during a Bug Bounty process, report it. Remember, we're here to contribute, and these kinds of observations are extremely helpful.
The possibilities for searches are vast — you might even want to check if any admin portals are exposed.
😸Let's type the following in the search bar:
site:vulnweb.com inurl:"admin*"
What are we asking for? We're basically telling Google:
"Hey, bring me only from the vulnweb site all the URLs that include words starting with 'admin' ". Did you notice I used a wildcard?
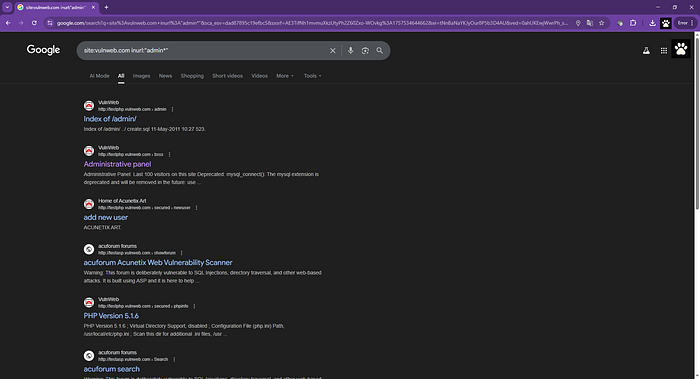
Google Dorks is vast — you don't need to learn everything, but it's highly recommended to prepare your queries to help you discover vulnerabilities that could have a high impact on a site's operation if a malicious actor comes along and tries to exploit them.
😸You can use operators within the same query and combine them however you like. Let's type the following in the search bar:
site:vulnweb.com ("index of" OR "internal use only")
Which basically tells Google:
"Hey, look inside vulnweb.com and show me any page that has either the phrase 'index of' or the phrase 'internal use only.' As long as it has one of the two, it's fine."
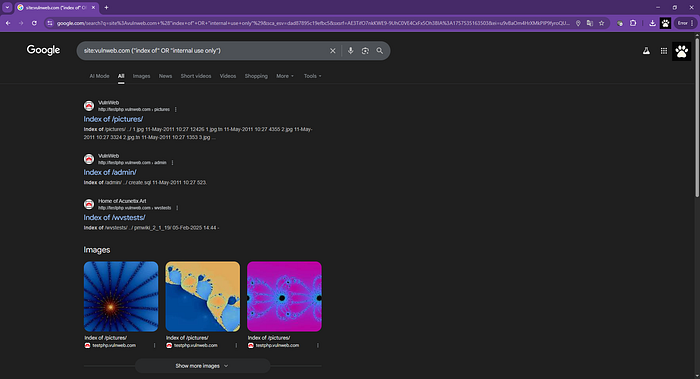
😸Haha, good boy, right!, let's try another combination.
site:vulnweb.com "index of" inurl:admin
Which basically tells Google:
"Show me pages on vulnweb.com that list files and have 'admin' in the URL". If you notice, you don't need to write "AND" — it's implicit for the browser.
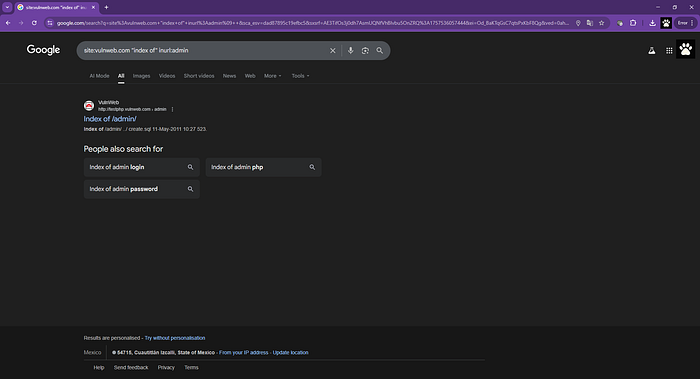
See, you can combine, right? Easy, isn't it? The point here is to think outside the box — think evil but act good. If your goal is to find vulnerabilities to report them, you're doing a good thing for the community.
With what we've learned today, you'll be able to better understand queries and start building your own tools to increase your chances of finding discoveries. I haven't shared a list of queries because we have colleagues who already do that wonderfully. My goal is that, beyond just copying and pasting queries, you truly understand how Google Dorks work. Always strive to understand everything, and if you haven't adopted this approach yet, I warmly invite you to give it a try.
If you want to explore more Google Dork combinations and tools, check out this great Medium article by MeetCyber — they do an excellent job diving deeper into the topic!
Now you have two options: either learn and understand everything you do to become a professional ethical hacker (chicken), or be just a simple executor of code and automated systems (tuna fish). The choice is yours, and you have plenty of information to learn from.
Guys, I hope you enjoyed it and learned something new. If you did, give me a round of applause and follow me. I constantly share content so we can all learn and increase the number of good guys out there.

