🔐Free Article Link
"Google Dorking is not about breaking into systems — it's about revealing the secrets the internet already whispers to those who know how to ask the right questions."

Hey hackers 👋
I'm Abhijeet Kumawat, a passionate cybersecurity enthusiast, bug bounty hunter, and someone who started with literally zero technical background.
This write-up is the fourth part of my series: "Bug Bounty from Scratch", where I'll be posting 25+ deep-dive stories on everything you need to know to start and succeed in the world of ethical hacking.
"And the best part? Everything I share is something I wish — — — — — someone told me when I was starting." — — — —
🔎 Why Google Dorking?
Imagine having access to billions of hidden treasures online — files, databases, credentials, and secrets — without hacking a single server. That's the secret power of Google Dorking.
Most people see Google as just a search engine, but security researchers and bug bounty hunters know it as a reconnaissance weapon. By crafting smart queries (called dorks), you can uncover sensitive information that organizations never intended to expose.
Think about it: misconfigured servers, forgotten backup files, exposed cameras, login portals, and even misindexed documents — all just a search away.
🛠️ How Google Dorking Works: It's Not Magic, It's Indexing
At its core, Google indexes everything it can crawl. Developers, admins, and careless users often leave behind files or pages that weren't supposed to be public.
By using Google search operators, we can filter results to target specific file types, keywords, or even site sections.
Google Dorking is simply the process of crafting precise queries that tell Google's algorithm exactly what to look for within its index. You're not hacking Google; you're using its own power to find specific, often sensitive, patterns of data it has already collected.
Here's the workflow 👇
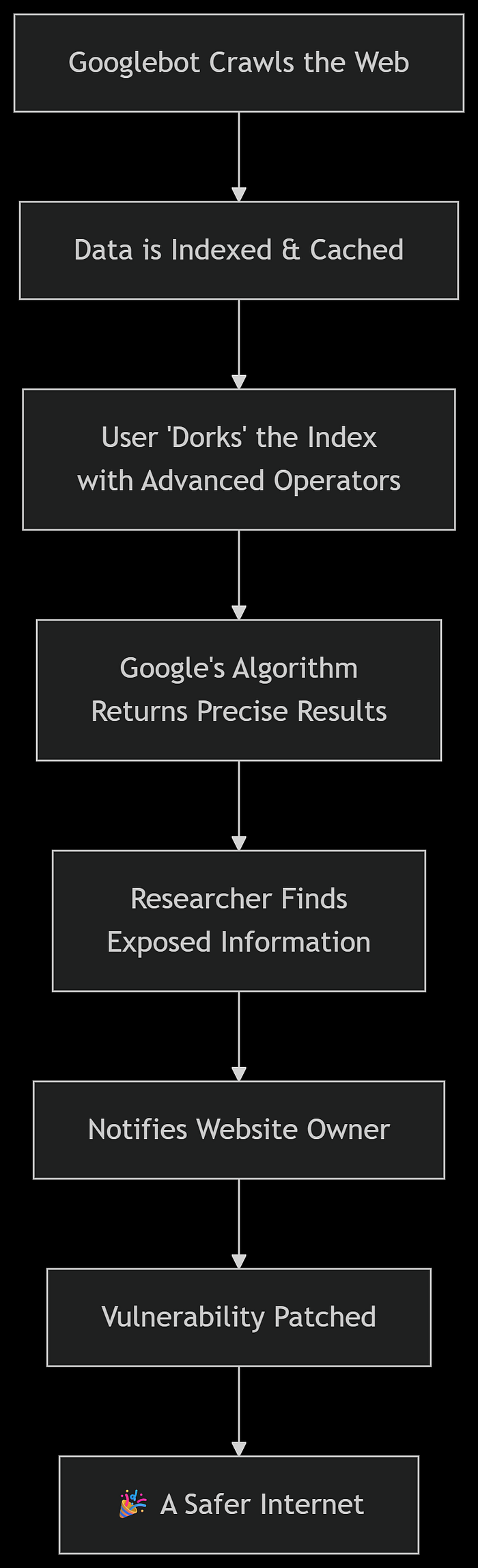
Building Your Own Dorks
Google dorks are just customized search queries. Think of operators as your search filters. Combine them to create a powerful "search lens."
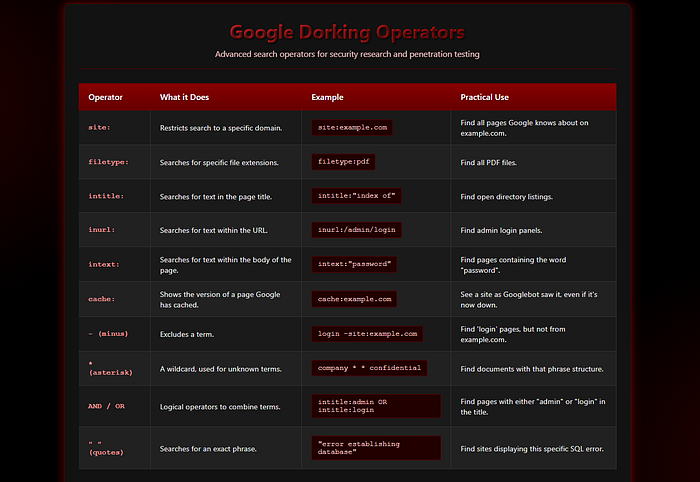
🔑 Pro Tip: Combine multiple operators for powerful results. Example:
site:gov.in filetype:xls intext:"password"This targets government domains with Excel files containing the word "password."
1. Exposed Credentials
Target: filetype:env, inurl:ftp, exposed keys in configs.
Why it's bad: Leaked credentials can lead to full database or server access.
Example Dorks:
filetype:env "DB_PASSWORD="
inurl:ftp intitle:"index of"2. Exposed Confidential Documents
Target: filetype:pdf, filetype:xlsx, filetype:docx.
Why it's bad: Financial records, client lists, manuals, and API keys may be exposed.
Example Dorks:
site:target.com filetype:pdf OR filetype:xlsx OR filetype:docx "confidential"
filetype:log site:example.com3. Open Web Directories & Sensitive Files
Target: intitle:"index of", inurl:/wp-content/ backups.
Why it's bad: Reveals entire file structure—downloadable configs, backups, or source code.
Example Dorks:
intitle:"index of" "parent directory" site:target.com
inurl:/wp-content/ backups site:target.com filetype:zip4. Misconfigured Login Portals & Admin Panels
Target: inurl:admin, intitle:login, phpMyAdmin.
Why it's bad: Attackers can brute-force, credential-stuff, or exploit misconfigured dashboards.
Example Dorks:
intitle:"admin login" site:target.com
inurl:/phpmyadmin/ site:target.com5. Error Messages Revealing System Info
Target: intext:"sql syntax", PHP/MySQL errors.
Why it's bad: Error traces reveal DB structure, software versions, and even code snippets.
Example Dorks:
intext:"warning: mysql_fetch_array()" site:target.com
intext:"sql syntax near" | "syntax error has occurred"6. Open Cameras & IoT Devices
Target: Camera dashboards (intitle:webcam, inurl:view.shtml).
Why it's bad: Default credentials allow attackers to spy, pivot, or control devices.
Example Dorks:
inurl:"/view/view.shtml"
intitle:"webcamXP 5"
intitle:"webcam 7" OR inurl:webcam.html
inurl:/view.shtml intitle:"live view"7. Source Code & Configuration Files
Target: .bak, .sql, config backups.
Why it's bad: Database dumps, hardcoded secrets, and app logic can be exposed.
Example Dorks:
filetype:bak site:example.com
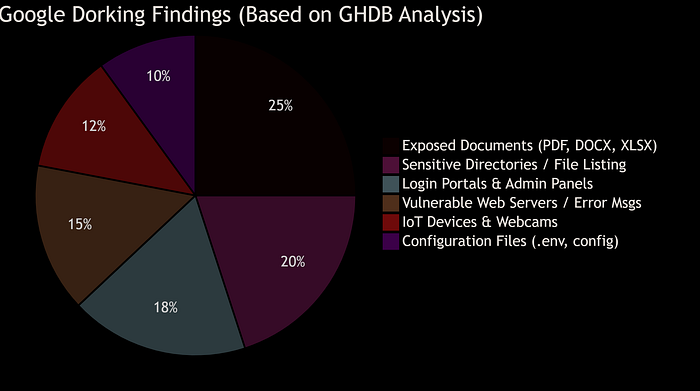
filetype:sql "INSERT INTO"Note: To understand the landscape of what's out there, this pie chart breaks down the most common categories of vulnerabilities and information exposed via Google Dorking, based on data from the Google Hacking Database (GHDB).
The Professional's Workflow: Beyond Simple Dorks
Amateurs use single dorks. Professionals use a systematic workflow.
-> Recon & Discovery:
site:target.com -www(Discover subdomains and non-www sites)site:*.target.com(Find all subdomains indexed by Google)
-> Content & Technology Mapping:
site:target.com filetype:php(Map all PHP pages, likely endpoints)site:target.com inurl:wp-(Check if the site uses WordPress)site:target.com "powered by"(Find out what tech stack it uses)
-> Vulnerability Hunting:
- Use the examples from the previous section, tailored to your target's tech stack (e.g., hunt for
.asperrors on a Windows server).
-> Documentation & Reporting:
- This is critical. For every finding, take a screenshot, note the full URL, and the exact dork used. This evidence is vital for your report to the client or site owner.
Exciting news! I'll soon be releasing a Google Dorking Cheat Sheet — a practical, easy-to-use resource packed with powerful search operators, real-world use cases, and pro tips to help you uncover hidden data like a true security researcher. Whether you're a bug bounty hunter, ethical hacker, or just curious about the unseen corners of the web, this cheat sheet will give you the exact queries you need to supercharge your reconnaissance. Stay tuned — this is going to be a must-have guide for anyone serious about mastering Google Dorking!
🧩 Practical Use Cases in Bug Bounty & Pentesting
-> Recon Phase
- Find forgotten subdomains:
site:*.example.com -www - Gather open portals for brute force.
-> Information Disclosure
- Exposed API keys in
.jsfiles:filetype:js site:example.com "api_key"
-> Social Engineering Edge
- Discover employee directories, emails, or phone numbers from indexed files.
-> Competitive Intelligence (rarely discussed!)
- Use Google Dorks for OSINT on competitors (marketing files, public tenders, or unprotected reports).
🕵️The Secret No One Talks About: The Google Hacking Database (GHDB)
The real treasure trove isn't just hidden dorks you see floating around Twitter or blogs — it's the Google Hacking Database (GHDB). Hosted by Offensive Security as part of the Exploit Database, GHDB is a curated collection of the most effective and dangerous Google Dorks ever discovered.
It's a living repository of queries attackers and researchers use to uncover exposed credentials, misconfigured servers, sensitive documents, and even IoT devices.
How to Use GHDB Like a Pro?
1. Don't Just Copy, Understand Patterns
- Each dork has a logic — whether it's targeting file types, error messages, or directory listings.
- Understand the why behind the query to craft your own custom dorks.
2. Adapt to Different Technologies
- A dork written for Apache servers (
intitle:"index of") can often be adapted to Nginx or IIS. - Example:
intitle:"index of /" site:target.com→ tweak variations for other server setups.
3. Combine & Customize
- Use GHDB dorks as a base, then combine them with:
site:→ to narrow down to specific targets.filetype:→ to isolate formats like.xls,.sql,.env.- Example:
site:target.com filetype:xls "password"4. Chain with Other Tools
- Don't stop at Google. Feed your dork results into automation frameworks:
- Katana → for crawling discovered endpoints.
- Nuclei → for scanning misconfigurations or known CVEs.
- Eyewitness → for screenshotting admin panels or directories.
5. Country-Targeted Dorks
- Restrict your searches to specific TLDs (Top-Level Domains).
- Example:
site:*.in filetype:xls password site:*.gov confidential filetype:pdf6. Time-Bounded Searches
- Use Google's search filters (Tools → Time) to find recently indexed leaks before they're cleaned up.
- Example:
filetype:log site:target.com(then filter results for "Past 24 hours").
7. Shodan + Google Dorks Combo
- Shodan finds open services (e.g., cameras, databases, IoT).
- Google Dorks refine those findings to pinpoint exposed files and dashboards.
- Example workflow:
- Step 1: Use Shodan for
"port:21 country:IN". - Step 2: Plug exposed domains into Google with dorks like:
inurl:ftp intitle:"index of"⚠️ Be an Ethical Hacker
You do not have permission to download or exploit files from systems you don't own.
Even if a file is exposed, accessing it may violate laws such as the Computer Fraud and Abuse Act (CFAA) or equivalent international laws.
The right way: If you discover a vulnerability on a system you don't own, document it, report it professionally, and stop there.
🔥Bonus: 34,000+ Bug Bounty Programs
Looking to skip the noise and dive straight into real bug bounty opportunities?
This exclusive list of 34,000+ Bug Bounty Programs is your shortcut.
You know what?
It includes top-tier targets from platforms like HackerOne, Bugcrowd, Intigriti, and many more ,and all help you focus on what's important:
finding bugs and earning bounties
Whether you're just starting or already hunting, this collection will save you hours of research and give you a clear path to real rewards.
Premium XSS Payload Cheat Sheet
I've created a Premium XSS Cheat Sheet that compiles advanced techniques, payloads, and practical tips to take your skills to the next level. Inside, you'll find:

- 📖 The Fundamentals — core concepts every researcher must know
- 🛡️ WAF & Filter Bypass — techniques to outsmart modern protections
- 🔑 Escalation to Account Takeover — moving from injection to impact
- ⚡ DOM-based Payloads — client-side exploitation strategies
- 🎭 Polyglot & Multi-Context Payloads — bypassing tricky scenarios
- 🔍 Rare & Obscure Contexts — payloads most guides don't cover
- 🛠️ External Tooling & Delivery — resources to supercharge your workflow
🔐 Final Thoughts
Google Dorking isn't about "hacking Google." It's about understanding how much data organizations unintentionally leak online.
For ethical hackers and bug bounty hunters, it's a treasure chest that reveals: ✔ Forgotten credentials ✔ Backup files ✔ Admin panels ✔ Hidden portals
The secret power lies not in knowing dorks, but in crafting unique ones for your target.
🎯 Coming Up Next:
"Hunting for IDORs: The Most Underrated Vulnerability"
❤️ Support My Work
If this helped you save money, time, or confusion: 👉 Buy Me a Coffee ☕❤️
Every cup fuels the next write-up.
