In this journey, I will share my experience with a valid report I submitted. This will be a series until I discover new vulnerabilities. 😊 Let's begin!
While reading through HackerOne reports in the past, I came across this report. That's when I first learned about AWS Cognito and how misconfigurations in it can lead to serious vulnerabilities. Since then, it stuck with me — I never forgot it.
If you're unfamiliar with this and want to learn more, I'll drop the link above for you to check out.
https://hackerone.com/reports/1342088
I was trying to gain some reputation on a VDP, so I picked a wildcard domain( like *.example.com) and ran waybackurls, mostly just hoping to find some low-hanging fruit.
While reviewing the output, I found two interesting subdomains like:
. sub3.sub2.sub1.example.com
. sub3.sub2.sub1.example.com
Both had login and registration pages. I thought maybe I could find an account takeover vulnerability.
After registering an account and reviewing my Burp Suite history, I saw that the application was using AWS Cognito for authentication.
Immediately, I thought of testing for misconfiguration issues in Cognito.
After logging in, I grabbed my access token and used the following command to view the user attributes tied to my account:
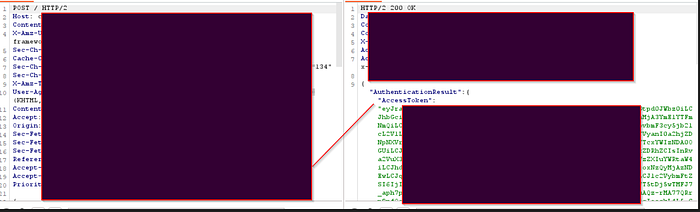
aws cognito-idp get-user --region REGIONUSEDBYSYSTEM--access-token YOURTOKENHEREAttributes tied to my account:

Next, I tried changing the email address in an attempt to achieve account takeover (same method as described in the HackerOne report), but it was unsuccessful — mainly because the web app was case-sensitive for email addresses also.
For example:
→ These were treated as two different accounts from web app.
I used the following command to change my email address:
aws cognito-idp update-user-attributes --region REGIONUSEDBYSYSTEM --access-token YOURTOKENHERE --user-attributes Name=email,Value=unverifiedanother@gmail.comAt this point, I noticed something strange: the web application normally does not allow users to log in without verifying their email address, but when I changed my email through the AWS CLI, the system gave skip option the email verification check, and I was able to log in successfully.
Additionally, there was no visible option in the UI to change the registered email.
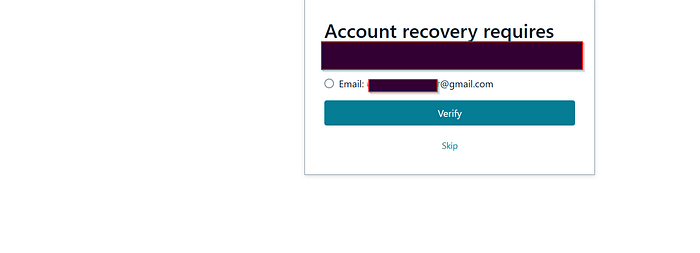
I reported both subdomains in a single report, and it was accepted.
Normally, an email verification bypass would be considered medium severity, but since the asset was classified as low priority, even a critical vulnerability would still be treated as low severity.
I know I could have reported them separately and earned more reputation, but that wasn't a big deal for me — because the asset itself was low impact.
I was just genuinely happy that I found a vulnerability based on something I had learned earlier.
Seems like learning new things really does pay off :)
